Spy collection program using fake mobile phone apps linked to Pakistani military
May 22, 2018 2 Comments
 The Pakistani military is suspected of having orchestrated a lucrative intelligence collection campaign using mobile phones, which targeted diplomats from India, Israel and Australia, as well as from North Atlantic Treaty Organization (NATO) member countries such as the United States and Britain. Others targeted in the operation include officials from Iraq, Iran and the United Arab Emirates. News of the alleged spy operation was published earlier this month by Lookout Mobile Security, a security software company based in the United States.
The Pakistani military is suspected of having orchestrated a lucrative intelligence collection campaign using mobile phones, which targeted diplomats from India, Israel and Australia, as well as from North Atlantic Treaty Organization (NATO) member countries such as the United States and Britain. Others targeted in the operation include officials from Iraq, Iran and the United Arab Emirates. News of the alleged spy operation was published earlier this month by Lookout Mobile Security, a security software company based in the United States.
The company said that the perpetrators of the operation managed to hack into a number of diplomats’ phones by creating a number of fake applications for Android and iOS mobile phone systems. The applications, called Tangelo (for iOS) and Stealth Mango (for Android), took control of mobile phone devices once their owners downloaded them through fake third-party app stores advertising online. According to Lookout, the two apps were designed by a consortium of freelance software developers who have close links with the Pakistani military establishment. The technical report published by Lookout points to the use of IP addresses that lead to a server housed in Pakistan’s Ministry of Education in the country’s capital, Islamabad. Lookout also said that it managed to trace the identity of the person who was the main developer of the two fake mobile phone applications. He is reportedly a full-time government employee who “moonlights as a mobile app developer”. The group that built the fake apps is known for creating legitimate apps, said Lookout, but also works for hire creating surveillanceware for mobile phone systems. In the past, the same group has been found to target military and civilian government officials in India, according to Lookout.
In its technical report, the Lookout security team describes how the Pakistani hackers collected a variety of data from their victims, by having it stealthily transmitted from compromised mobile phones to servers in Islamabad. The data included photos and videos, lists of contacts, logs of phone calls and texts, as well as detailed calendar entries. German and Australian diplomats had their travel plans stolen, and a letter from the United States Central Command to Afghanistan’s assistant minister of defense for intelligence was also acquired by the hackers. The latter also gained access to the contents of an entire database of pictures of traveler passports —many of them diplomatic— from the Kandahar International Airport in southern Afghanistan. The report said it was impossible to know for certain when Tangelo and Stealth Mango were first developed and utilized. However, the most recent version of the apps was released in April of this year.
► Author: Joseph Fitsanakis | Date: 22 May 2018 | Permalink
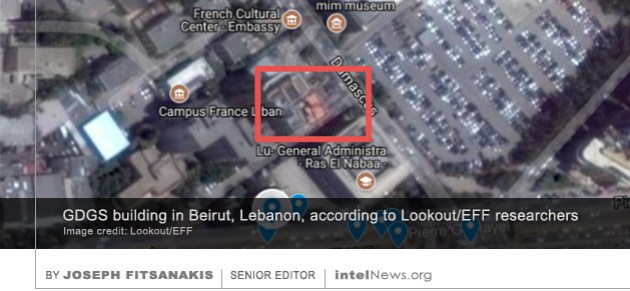 The spy agency of Lebanon used a virus designed for the Android mobile operating system to compromise the cell phones of thousands of people in at least 20 countries, according to a new mobile security report. The 50-page
The spy agency of Lebanon used a virus designed for the Android mobile operating system to compromise the cell phones of thousands of people in at least 20 countries, according to a new mobile security report. The 50-page 






Most government hackers now target cell phones, not computers, experts say
June 8, 2018 by Ian Allen Leave a comment
According to Lookout, the increase in hacking operations targeting mobile phones reflects the proliferation of smartphone usage around the world, as well as the increase in consumption of cell phone software. Government-sponsored hackers usually compromise their targets’ cell phones through malicious software disguised as cell phone applications. The Wall Street Journal also reports that the software needed to build malicious software for cell phones has become cheaper and more readily available. Compromising a target’s cell phone provides hackers with information that is far more personal and sensitive than what can be found on a personal computer. The paper quotes Mike Murray, Lookout’s vice president of security research, who says: “It is one thing to compromise someone’s computer. It’s another thing to have a listening device that they carry around with them 24 hours a day”. Compromised phones become immensely powerful espionage tools, explains Murray.
Many of the individuals whose cell phones are targeted by governments are activists or dissidents who campaign for political or economic reforms in their countries. Their cell phones are targeted in systematic hacking campaigns by countries like Ethiopia, the United Arab Emirates, Cambodia, and Mexico, said Lookout. The Wall Street Journal cites Raj Samani, chief scientist for the antivirus firm McAfee, who claims that nearly 11 percent of cell phones worldwide were infected with some kind of malware in 2017. That statistic is likely to rise significantly by the end of 2018, says Samani.
► Author: Ian Allen | Date: 08 June 2018 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with cellular telephony, Lookout Mobile Security, McAffee, Mike Murray, News, Raj Samani, telephone hacking