Cell phones of leading Polish opposition figures hacked by government, group claims
December 27, 2021 3 Comments
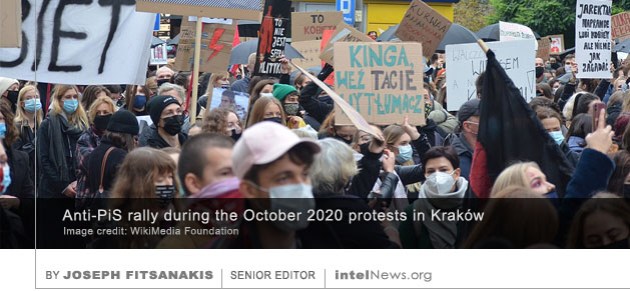 CENTRAL FIGURES OF POLAND’S opposition coalition, which narrowly lost the 2019 parliamentary election, had their cell phones hacked with a surveillance software used by the country’s spy services, according to a new report. A major target of the hacks was Krzysztof Brejza, a member of the lower chamber of the Polish parliament and campaign director of the Civic Coalition, a centrist-liberal alliance. In the parliamentary election of 2019, the Civic Coalition challenged the all-powerful Law and Justice Party (PiS), which has ruled Poland for much of the past decade.
CENTRAL FIGURES OF POLAND’S opposition coalition, which narrowly lost the 2019 parliamentary election, had their cell phones hacked with a surveillance software used by the country’s spy services, according to a new report. A major target of the hacks was Krzysztof Brejza, a member of the lower chamber of the Polish parliament and campaign director of the Civic Coalition, a centrist-liberal alliance. In the parliamentary election of 2019, the Civic Coalition challenged the all-powerful Law and Justice Party (PiS), which has ruled Poland for much of the past decade.
The PiS is a populist pro-Russian party that opposes many of the core policies of the European Union, of which Poland is a member. In contrast, the Civil Coalition is pro-Western and supports Poland’s integration into the European Union. In 2019, while the two parties were competing in a feverish electoral campaign, Poland’s state-owned television aired a number of texts acquired from Brejza’s phone, in what the opposition decried as a “smear campaign”. Eventually, the PiS won the election with a narrow majority.
The information about Brejza’s cell phone hack was revealed last week by Citizen Lab, a research unit of the University of Toronto’s Munk School of Global Affairs and Public Policy, which focuses on information technology, international security and human rights. According to the report, at least three senior figures in the Civil Coalition were under telephonic surveillance throughout the election campaign. Brejza’s cell phone was breached over 30 times between April and October of 2019, according to Citizen Lab. The other two victims of the surveillance operation were Ewa Wrzosek, a public prosecutor and leading critic of the PiS, as well as Roman Giertych, an attorney who represents leading members of the Civic Coalition.
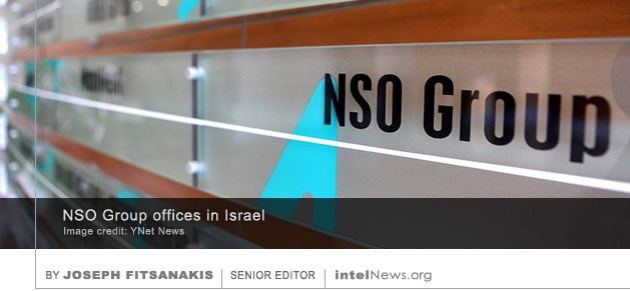
The report claims that the surveillance against the Civil Coalition members was facilitated by Pegasus, a controversial spyware that is sold to governments around the world by NSO Group Technologies, an Israeli digital surveillance company based near Tel Aviv. Earlier this year, the United States government blacklisted NSO Group Technologies, in a move that surprised many in Israel and beyond. Meanwhile, on December 24, the Polish government denied it had any role in the phone hacking affair. Poland’s Prime Minister, Mateusz Morawiecki, dismissed the Citizen Lab revelations as “fake news”.
► Author: Joseph Fitsanakis | Date: 27 December 2021 | Permalink

 THE CHANNEL ISLANDS, AN archipelago consisting of dependencies of the British Crown located off the northern coast of France, are being used as an offshore global spy center due to their unregulated telecommunications industry, according to a new study. The archipelago is made up of Jersey and Guernsey, groups of islands that are not technically part of Britain, but are instead considered offshore British territories. They are regularly
THE CHANNEL ISLANDS, AN archipelago consisting of dependencies of the British Crown located off the northern coast of France, are being used as an offshore global spy center due to their unregulated telecommunications industry, according to a new study. The archipelago is made up of Jersey and Guernsey, groups of islands that are not technically part of Britain, but are instead considered offshore British territories. They are regularly  The personal smartphones of leading Catalan pro-independence politicians were hacked using a highly invasive software built by a controversial Israeli firm, according to an investigative report by two newspapers. The revelation is likely to reignite a tense row between Madrid and pro-independence activists in one of the country’s wealthiest regions, which led to a major political crisis in 2017.
The personal smartphones of leading Catalan pro-independence politicians were hacked using a highly invasive software built by a controversial Israeli firm, according to an investigative report by two newspapers. The revelation is likely to reignite a tense row between Madrid and pro-independence activists in one of the country’s wealthiest regions, which led to a major political crisis in 2017. The government of Saudi Arabia may be exploiting a decades-old tracking system embedded in the global mobile telecommu- nications network in order to spy on its citizens as they travel abroad, a report suggests. The report was
The government of Saudi Arabia may be exploiting a decades-old tracking system embedded in the global mobile telecommu- nications network in order to spy on its citizens as they travel abroad, a report suggests. The report was 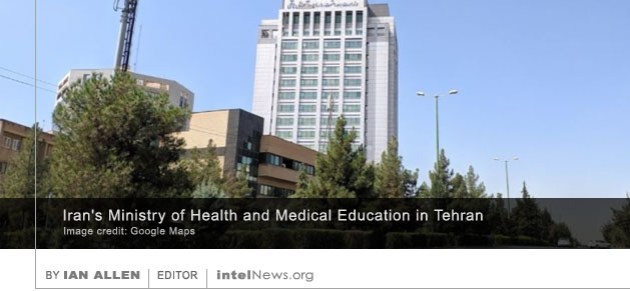 An Android application developed by the Iranian government to assist in coordinating the country’s response to the COVID-19 epidemic has been removed by Google amidst accusations that it may be used to track Iranian dissidents. The application, named AC19, was released several days ago by Iran’s Ministry of Health and Medical Education. Its release was announced through a text message sent by the Iranian government to every mobile telephone subscriber in the country. The text message urged citizens to download the application through a dedicated website or third-party app stores, including the Google Play Store. Millions have since done so.
An Android application developed by the Iranian government to assist in coordinating the country’s response to the COVID-19 epidemic has been removed by Google amidst accusations that it may be used to track Iranian dissidents. The application, named AC19, was released several days ago by Iran’s Ministry of Health and Medical Education. Its release was announced through a text message sent by the Iranian government to every mobile telephone subscriber in the country. The text message urged citizens to download the application through a dedicated website or third-party app stores, including the Google Play Store. Millions have since done so. The intelligence services of Israel planted surveillance devices around the White House in an attempt to spy on United States President Donald Trump and his senior advisors, according to a report published on Thursday. The
The intelligence services of Israel planted surveillance devices around the White House in an attempt to spy on United States President Donald Trump and his senior advisors, according to a report published on Thursday. The  Officials in the White House are concerned about President Donald Trump’s insistence on using an unsecured iPhone to communicate with friends and associates, despite warnings that foreign spies may be listening in. Prior to being elected president, Trump used an Android phone, made by Google, which the NSA advised him to abandon due to security concerns. That is when he switched to using iPhones. Since his election to the presidency, Trump has routinely used three iPhone cell phones. He uses one of them to access a limited list of authorized applications, including Twitter. He uses the second iPhone for phone calls, but cannot use it to send texts, take pictures, or download and install applications. Both of these iPhones have been vetted and secured by the National Security Agency (NSA).
Officials in the White House are concerned about President Donald Trump’s insistence on using an unsecured iPhone to communicate with friends and associates, despite warnings that foreign spies may be listening in. Prior to being elected president, Trump used an Android phone, made by Google, which the NSA advised him to abandon due to security concerns. That is when he switched to using iPhones. Since his election to the presidency, Trump has routinely used three iPhone cell phones. He uses one of them to access a limited list of authorized applications, including Twitter. He uses the second iPhone for phone calls, but cannot use it to send texts, take pictures, or download and install applications. Both of these iPhones have been vetted and secured by the National Security Agency (NSA). The Pakistani military is suspected of having orchestrated a lucrative intelligence collection campaign using mobile phones, which targeted diplomats from India, Israel and Australia, as well as from North Atlantic Treaty Organization (NATO) member countries such as the United States and Britain. Others targeted in the operation include officials from Iraq, Iran and the United Arab Emirates. News of the alleged spy operation was published earlier this month by Lookout Mobile Security, a security software company based in the United States.
The Pakistani military is suspected of having orchestrated a lucrative intelligence collection campaign using mobile phones, which targeted diplomats from India, Israel and Australia, as well as from North Atlantic Treaty Organization (NATO) member countries such as the United States and Britain. Others targeted in the operation include officials from Iraq, Iran and the United Arab Emirates. News of the alleged spy operation was published earlier this month by Lookout Mobile Security, a security software company based in the United States. An joint operation conducted by American and Iraqi intelligence officers employed a popular messaging app on the phone of a captured Islamic State commander to apprehend four very senior figures in the organization, according to reports. The Reuters news agency
An joint operation conducted by American and Iraqi intelligence officers employed a popular messaging app on the phone of a captured Islamic State commander to apprehend four very senior figures in the organization, according to reports. The Reuters news agency 





