German intelligence agencies discuss ongoing espionage and hybrid challenges
May 6, 2024 Leave a comment
 THE 5TH SYMPOSIUM ON the Law of Intelligence Services (Symposium zum Recht der Nachrichtendienste) took place in Berlin, Germany, on March 21-22. In view of the public criticism that German intelligence agencies have faced in recent times, it was probably a relief for their officials to be able to talk more-or-less among themselves for once.
THE 5TH SYMPOSIUM ON the Law of Intelligence Services (Symposium zum Recht der Nachrichtendienste) took place in Berlin, Germany, on March 21-22. In view of the public criticism that German intelligence agencies have faced in recent times, it was probably a relief for their officials to be able to talk more-or-less among themselves for once.
The event (see agenda in .pdf) was organized by the Federal Ministry of the Interior and the Federal Chancellery Office. This year’s topic was: “Intelligence Agencies and Armed Conflicts”. It included the tried and tested mix of academics —predominantly legal scholars—, practitioners and heads of various government authorities. The majority of the external experts discussed the complicated and, in Germany, arduous parliamentary procedures that would arise in the event of a war.
In view of the controls increasingly being placed on German intelligence agencies by various bodies and authorities —which were also represented at the symposium— a certain discrepancy became apparent repeatedly in the presentations: How can the German intelligence agencies react adequately and quickly to hybrid threats when these types of threat do not concern themselves with administrative-legal subtleties and parliamentary procedures? Although the concept of hybrid threats was generally taken for granted and therefore hardly discussed in terms of content, those present agreed at a minimum that disinformation is part of it. All the more worrying was the statement by one speaker who explained that there was no official definition of disinformation within the German security authorities’ legal codes.
In the discussion, the panel moderated by Center for Intelligence Service Training and Further Education (ZNAF), the common training and study location of the Federal Intelligence Service (BND) and the Federal Office for the Protection of the Constitution (BfV), clearly stood out and underscored that this relatively new institution has made a name for itself in the academic intelligence landscape since its establishment in 2019.
However, the symposium also showed that the German security bureaucracy tends to reach its limits when it comes to current developments in the unconventional domain. This was demonstrated, for example, by a speaker’s demand that hybrid risks ought to be assigned to a “state area of responsibility”. The problem, however, lies precisely in the statelessness of hybrid risks. The existing regulations are also proving to be counterproductive, in view of the challenges: there would simply be highly heterogeneous participants in the so-called Cyber Defense Centre, which would also include police authorities. However, due to the strict separation in the legal domain, personal data cannot simply be passed on from the BND to the Federal Police, for example. Read more of this post
 SEVERAL CASES OF CHINESE espionage have been
SEVERAL CASES OF CHINESE espionage have been  AUTHORITIES IN GERMANY HAVE arrested a sixth person in less than a month, in connection with three separate cases of espionage orchestrated by Russian or Chinese intelligence. Last Tuesday, police in the east German city of Dresden arrested an assistant to a leading politician of the far-right Alternative für Deutschland party (AfD). The assistant, who is a dual German-Chinese citizen, is accused of spying for Chinese intelligence, while the far-right politician who employed him is also being investigated, according to reports.
AUTHORITIES IN GERMANY HAVE arrested a sixth person in less than a month, in connection with three separate cases of espionage orchestrated by Russian or Chinese intelligence. Last Tuesday, police in the east German city of Dresden arrested an assistant to a leading politician of the far-right Alternative für Deutschland party (AfD). The assistant, who is a dual German-Chinese citizen, is accused of spying for Chinese intelligence, while the far-right politician who employed him is also being investigated, according to reports. THE TARGETED KILLING OF Hassan Mahdawi, a high-ranking member of Iran’s Islamic Revolutionary Guards Corps (IRGC) and the commander of the Quds Force in Syria and Lebanon, was carried out by Israel on April 1, 2024. The actual assassination was based on precise operational intelligence, while Israel’s assessment of Iran’s response was wrong.
THE TARGETED KILLING OF Hassan Mahdawi, a high-ranking member of Iran’s Islamic Revolutionary Guards Corps (IRGC) and the commander of the Quds Force in Syria and Lebanon, was carried out by Israel on April 1, 2024. The actual assassination was based on precise operational intelligence, while Israel’s assessment of Iran’s response was wrong. AUTHORITIES IN GERMANY and Poland have charged three individuals with working on behalf of Russian military intelligence in planning acts of sabotage and assassination on European soil. One of the plots allegedly involved an effort to assassinate Ukrainian President Volodymyr Zelenskyy. Another aimed to sabotage commercial airport facilities that are being managed by the United States military.
AUTHORITIES IN GERMANY and Poland have charged three individuals with working on behalf of Russian military intelligence in planning acts of sabotage and assassination on European soil. One of the plots allegedly involved an effort to assassinate Ukrainian President Volodymyr Zelenskyy. Another aimed to sabotage commercial airport facilities that are being managed by the United States military. ON GOOD FRIDAY, MARCH 29, Egisto Ott, a former member of Austria’s now-dissolved domestic intelligence agency, the Federal Office for the Protection of the Constitution and Counterterrorism (BVT), was arrested in his house in Carinthia, Austria’s southernmost state. Ott had frequently been at the center of media attention in the past year, in connection with the network surrounding the fugitive
ON GOOD FRIDAY, MARCH 29, Egisto Ott, a former member of Austria’s now-dissolved domestic intelligence agency, the Federal Office for the Protection of the Constitution and Counterterrorism (BVT), was arrested in his house in Carinthia, Austria’s southernmost state. Ott had frequently been at the center of media attention in the past year, in connection with the network surrounding the fugitive  These included contacts in friendly foreign police services, whom Ott knew from his time as a liaison officer in Italy and Turkey. According to Gridling, these contacts were unaware that Ott had been removed from the BVT under suspicion of being unreliable and potentially even working for Russia. They therefore continued to help him when asked. Ott allegedly deceived his contacts by claiming that he needed information on cases relating to different kinds of extremism. As it turned out, according to the leaked arrest warrant, several of the individuals referred to by Ott as “suspects” in terrorism investigations were in fact Russian dissidents or intelligence defectors who were living as protected persons in Austria and elsewhere outside Russia.
These included contacts in friendly foreign police services, whom Ott knew from his time as a liaison officer in Italy and Turkey. According to Gridling, these contacts were unaware that Ott had been removed from the BVT under suspicion of being unreliable and potentially even working for Russia. They therefore continued to help him when asked. Ott allegedly deceived his contacts by claiming that he needed information on cases relating to different kinds of extremism. As it turned out, according to the leaked arrest warrant, several of the individuals referred to by Ott as “suspects” in terrorism investigations were in fact Russian dissidents or intelligence defectors who were living as protected persons in Austria and elsewhere outside Russia. ON MARCH 23, CHANNEL 12 of Israeli television aired a remarkable interview with Sassi Elya, the former director of technology at the Israel Security Agency (ISA). Better known by the acronyms Shin Bet or Shabak, the ISA is Israel’s domestic security service. The interview had initially been scheduled for broadcast as part of the evening news on October 7, 2023. However, its airing was canceled due to the attack on Israel by Hamas, which occurred that morning.
ON MARCH 23, CHANNEL 12 of Israeli television aired a remarkable interview with Sassi Elya, the former director of technology at the Israel Security Agency (ISA). Better known by the acronyms Shin Bet or Shabak, the ISA is Israel’s domestic security service. The interview had initially been scheduled for broadcast as part of the evening news on October 7, 2023. However, its airing was canceled due to the attack on Israel by Hamas, which occurred that morning. NO COUNTRY HAS BETTER intelligence on the Islamic State-Khorasan Province (known as ISIS-K) than the United States. American forces have faced ISIS-K almost from the moment the group was founded in 2015 in Pakistan, just a few miles from the Afghan border. It was there that a group of disaffected members of the Tehreek-e-Taliban-e-Pakistan (TTP, commonly referred to as the Pakistani Taliban) began turning their backs on al-Qaeda, which they saw as a failing brand, and joined the Islamic State of Iraq and Syria (ISIS).
NO COUNTRY HAS BETTER intelligence on the Islamic State-Khorasan Province (known as ISIS-K) than the United States. American forces have faced ISIS-K almost from the moment the group was founded in 2015 in Pakistan, just a few miles from the Afghan border. It was there that a group of disaffected members of the Tehreek-e-Taliban-e-Pakistan (TTP, commonly referred to as the Pakistani Taliban) began turning their backs on al-Qaeda, which they saw as a failing brand, and joined the Islamic State of Iraq and Syria (ISIS). not being taken into consideration by the group’s primary targets, namely Afghanistan, Iran, and Russia. Indeed, despite the Washington’s best efforts, its warnings about pending ISIS-K attacks have been ignored by the group’s primary targets. A few days after an ISIS-K attack killed nearly 100 people in Kerman, Iran, The Wall Street Journal
not being taken into consideration by the group’s primary targets, namely Afghanistan, Iran, and Russia. Indeed, despite the Washington’s best efforts, its warnings about pending ISIS-K attacks have been ignored by the group’s primary targets. A few days after an ISIS-K attack killed nearly 100 people in Kerman, Iran, The Wall Street Journal  FEW THINGS ARE AS valuable in the field of intelligence studies as delving into historical case work. Indeed, the study of intelligence history is indispensable for anyone wishing to engage in the contemporary setting of this often esoteric -yet critical- field. As an academic specializing in intelligence, I find Bill Mills’
FEW THINGS ARE AS valuable in the field of intelligence studies as delving into historical case work. Indeed, the study of intelligence history is indispensable for anyone wishing to engage in the contemporary setting of this often esoteric -yet critical- field. As an academic specializing in intelligence, I find Bill Mills’  AGENTS OF THE CUBAN government have “penetrated virtually every segment of the United States national security structure,” enabling Havana to share actionable intelligence with Russia and China, according to a new report. Citing former United States and Cuban intelligence officers, The Wall Street Journal
AGENTS OF THE CUBAN government have “penetrated virtually every segment of the United States national security structure,” enabling Havana to share actionable intelligence with Russia and China, according to a new report. Citing former United States and Cuban intelligence officers, The Wall Street Journal  SINCE OCTOBER 7, 2024, when Israel was caught off guard by a sudden and highly damaging attack from Hamas, more information has surfaced regarding why there was no prior warning about the attack and the failures of Israeli intelligence in this regard.
SINCE OCTOBER 7, 2024, when Israel was caught off guard by a sudden and highly damaging attack from Hamas, more information has surfaced regarding why there was no prior warning about the attack and the failures of Israeli intelligence in this regard. capabilities. Another important insight is that the counterintelligence structures inside Hamas were successful in preventing Israeli intelligence from recruiting agents who were close enough to Sinwar to be able to alert Israel about the impending attack. Furthermore, Israel’s collection and analysis of signals intelligence was unproductive, possibly because Hamas was successful in countering Israel’s ability to produce effective intelligence from signals intercepts.
capabilities. Another important insight is that the counterintelligence structures inside Hamas were successful in preventing Israeli intelligence from recruiting agents who were close enough to Sinwar to be able to alert Israel about the impending attack. Furthermore, Israel’s collection and analysis of signals intelligence was unproductive, possibly because Hamas was successful in countering Israel’s ability to produce effective intelligence from signals intercepts.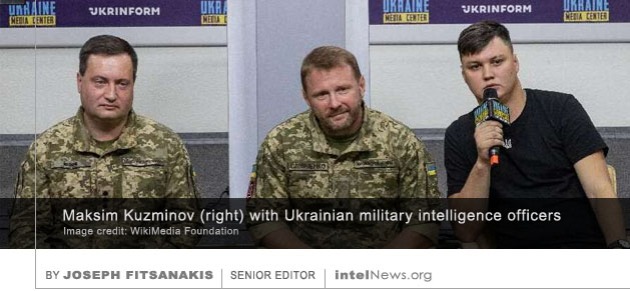 THE RUSSIAN INTELLIGENCE SERVICES have been “bolstering the[ir] architecture” aimed at stopping potential defectors and “liquidating” those who have already defected and are living in exile, according to a new report. In a
THE RUSSIAN INTELLIGENCE SERVICES have been “bolstering the[ir] architecture” aimed at stopping potential defectors and “liquidating” those who have already defected and are living in exile, according to a new report. In a  A RETIRED SENIOR MOSSAD official has alleged that Israeli Prime Minister Benjamin Netanyahu repeatedly ignored, and even frustrated, efforts to stop the flow of hundreds of millions of dollars to Hamas. This inaction may have enabled the Palestinian militant group to plan, organize and execute Operation Al-Aqsa Flood, which killed over 1400 Israelis on October 7, 2023, and sparked the current war between Israel and Hamas.
A RETIRED SENIOR MOSSAD official has alleged that Israeli Prime Minister Benjamin Netanyahu repeatedly ignored, and even frustrated, efforts to stop the flow of hundreds of millions of dollars to Hamas. This inaction may have enabled the Palestinian militant group to plan, organize and execute Operation Al-Aqsa Flood, which killed over 1400 Israelis on October 7, 2023, and sparked the current war between Israel and Hamas. AUTHORITIES IN IRELAND ARE systematically “freezing” applications for Russian diplomatic visas from Moscow over concerns that the Kremlin is using its embassy in Dublin as a base for espionage activities. In 2018, the Irish government introduced emergency legislation that canceled a previously approved expansion of the Russian diplomatic compound in the Irish capital, allegedly due to concerns about espionage activities by Russian diplomats. Three years later,
AUTHORITIES IN IRELAND ARE systematically “freezing” applications for Russian diplomatic visas from Moscow over concerns that the Kremlin is using its embassy in Dublin as a base for espionage activities. In 2018, the Irish government introduced emergency legislation that canceled a previously approved expansion of the Russian diplomatic compound in the Irish capital, allegedly due to concerns about espionage activities by Russian diplomats. Three years later,  AN AFGHAN-BORN MAN, who became a naturalized British citizen and worked for British intelligence for over a decade, is attempting to regain his British citizenship, which was revoked after he was accused of being a Russian spy. The man, who is identified in court documents only as “C2”, was born in Afghanistan and grew up under the Soviet occupation in the 1980s. When the Soviets withdrew from Afghanistan he left the country alongside the Russian forces and resettled in Russia, where he attended university and married a Russian woman.
AN AFGHAN-BORN MAN, who became a naturalized British citizen and worked for British intelligence for over a decade, is attempting to regain his British citizenship, which was revoked after he was accused of being a Russian spy. The man, who is identified in court documents only as “C2”, was born in Afghanistan and grew up under the Soviet occupation in the 1980s. When the Soviets withdrew from Afghanistan he left the country alongside the Russian forces and resettled in Russia, where he attended university and married a Russian woman.





