Austria: Arrest raises broader questions about counterintelligence capabilities
April 10, 2024 5 Comments
 ON GOOD FRIDAY, MARCH 29, Egisto Ott, a former member of Austria’s now-dissolved domestic intelligence agency, the Federal Office for the Protection of the Constitution and Counterterrorism (BVT), was arrested in his house in Carinthia, Austria’s southernmost state. Ott had frequently been at the center of media attention in the past year, in connection with the network surrounding the fugitive financier and alleged spy Jan Maršálek, as well as alleged misconduct relating to carrying out illegal investigations of persons. Ott also seems to have been involved in an alleged attempt to create an intelligence unit, or even an entire shadow intelligence service, embedded inside Austria’s foreign ministry. Now the veteran police and intelligence officer stands accused by the state attorney of abusing his authority and of being part of an “intelligence activity to the disadvantage of Austria” —the only form of spying that is illegal under § 256 of the Austrian criminal code.
ON GOOD FRIDAY, MARCH 29, Egisto Ott, a former member of Austria’s now-dissolved domestic intelligence agency, the Federal Office for the Protection of the Constitution and Counterterrorism (BVT), was arrested in his house in Carinthia, Austria’s southernmost state. Ott had frequently been at the center of media attention in the past year, in connection with the network surrounding the fugitive financier and alleged spy Jan Maršálek, as well as alleged misconduct relating to carrying out illegal investigations of persons. Ott also seems to have been involved in an alleged attempt to create an intelligence unit, or even an entire shadow intelligence service, embedded inside Austria’s foreign ministry. Now the veteran police and intelligence officer stands accused by the state attorney of abusing his authority and of being part of an “intelligence activity to the disadvantage of Austria” —the only form of spying that is illegal under § 256 of the Austrian criminal code.
Ott’s arrest came several years after intelligence was first shared with Austria by Western partner services —allegedly the Central Intelligence Agency— that reportedly date from as early as November 2017. Back then, Ott allegedly received classified material from his service’s email address to his personal Gmail account. However, Peter Gridling, director of the BVT from 2008 until its dissolution in 2021, stated in a recent interview that the ensuing investigations did not yield actionable results that could be used in criminal proceedings. This statement is highly interesting, as Gridling filed accusations about Ott with the State Prosecutor’s Office himself, and would hardly have done unless he had access to hard evidence. Ott was consequently removed from the BVT and placed in Police Academy Austria (SIAK), which is responsible for training police officers and conducts research related to police and domestic security.
Nevertheless, according to media reporting, Ott seems to have kept and illegally used certain forms of identification that presented him as a police officer. He is also alleged to have maintained access to several police databases and to have retained his network of trusted informants that provided him with intelligence.  These included contacts in friendly foreign police services, whom Ott knew from his time as a liaison officer in Italy and Turkey. According to Gridling, these contacts were unaware that Ott had been removed from the BVT under suspicion of being unreliable and potentially even working for Russia. They therefore continued to help him when asked. Ott allegedly deceived his contacts by claiming that he needed information on cases relating to different kinds of extremism. As it turned out, according to the leaked arrest warrant, several of the individuals referred to by Ott as “suspects” in terrorism investigations were in fact Russian dissidents or intelligence defectors who were living as protected persons in Austria and elsewhere outside Russia.
These included contacts in friendly foreign police services, whom Ott knew from his time as a liaison officer in Italy and Turkey. According to Gridling, these contacts were unaware that Ott had been removed from the BVT under suspicion of being unreliable and potentially even working for Russia. They therefore continued to help him when asked. Ott allegedly deceived his contacts by claiming that he needed information on cases relating to different kinds of extremism. As it turned out, according to the leaked arrest warrant, several of the individuals referred to by Ott as “suspects” in terrorism investigations were in fact Russian dissidents or intelligence defectors who were living as protected persons in Austria and elsewhere outside Russia.
It appears highly probable that Ott also had people inside the Austrian bureaucracy, including former colleagues in the BVT, who continued to provide him with information and assistance, even after the first allegations against him arose in 2017. As of now, at least one other officer from LVT Vienna (the state unit of the BVT) has been found to have illegally provided Ott with Information. It is likely, given the publicly available descriptions of Ott’s activities, that other individuals may be implicated. It also remains to be seen whether individuals involved in this case were able to join the BVT’s successor agency, the new Directorate of State Protection and Intelligence (DSN). Read more of this post
 AGENTS OF THE CUBAN government have “penetrated virtually every segment of the United States national security structure,” enabling Havana to share actionable intelligence with Russia and China, according to a new report. Citing former United States and Cuban intelligence officers, The Wall Street Journal
AGENTS OF THE CUBAN government have “penetrated virtually every segment of the United States national security structure,” enabling Havana to share actionable intelligence with Russia and China, according to a new report. Citing former United States and Cuban intelligence officers, The Wall Street Journal  AN AFGHAN-BORN MAN, who became a naturalized British citizen and worked for British intelligence for over a decade, is attempting to regain his British citizenship, which was revoked after he was accused of being a Russian spy. The man, who is identified in court documents only as “C2”, was born in Afghanistan and grew up under the Soviet occupation in the 1980s. When the Soviets withdrew from Afghanistan he left the country alongside the Russian forces and resettled in Russia, where he attended university and married a Russian woman.
AN AFGHAN-BORN MAN, who became a naturalized British citizen and worked for British intelligence for over a decade, is attempting to regain his British citizenship, which was revoked after he was accused of being a Russian spy. The man, who is identified in court documents only as “C2”, was born in Afghanistan and grew up under the Soviet occupation in the 1980s. When the Soviets withdrew from Afghanistan he left the country alongside the Russian forces and resettled in Russia, where he attended university and married a Russian woman. BEIJING HAS ACCUSED “FOREIGN governments” of collecting data on China through hundreds of fake meteorological stations that have been illegally installed throughout Chinese territory. The announcement appears to form part of a broader “people’s anti-espionage war” that the Communist Party of China
BEIJING HAS ACCUSED “FOREIGN governments” of collecting data on China through hundreds of fake meteorological stations that have been illegally installed throughout Chinese territory. The announcement appears to form part of a broader “people’s anti-espionage war” that the Communist Party of China 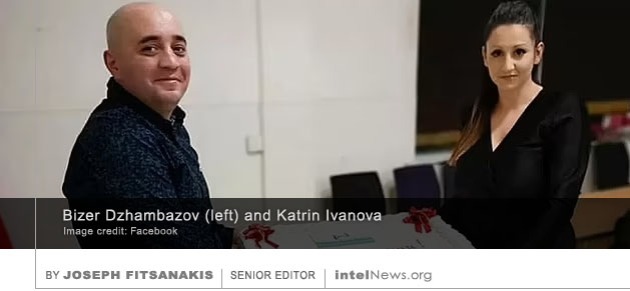 AUTHORITIES IN BRITAIN HAVE charged three Bulgarian nationals with spying for Russia, as part of “a major national security investigation” that led to at least five arrests as early as last February. Two of the Bulgarians appear to be legally married. They have been identified as Bizer Dzhambazov, 41, and Katrin Ivanova, 31, who live in Harrow, a northwestern borrow of Greater London. The third Bulgarian, Orlin Roussev, 45, was arrested in Great Yarmouth, a seaside town in the east coast identity dof England. None of the suspect appears to have a formal diplomatic connection to either Bulgaria or Russia.
AUTHORITIES IN BRITAIN HAVE charged three Bulgarian nationals with spying for Russia, as part of “a major national security investigation” that led to at least five arrests as early as last February. Two of the Bulgarians appear to be legally married. They have been identified as Bizer Dzhambazov, 41, and Katrin Ivanova, 31, who live in Harrow, a northwestern borrow of Greater London. The third Bulgarian, Orlin Roussev, 45, was arrested in Great Yarmouth, a seaside town in the east coast identity dof England. None of the suspect appears to have a formal diplomatic connection to either Bulgaria or Russia. AUTHORITIES IN BRAZIL HAVE launched a nationwide probe into the abuse of the country’s citizenship documentation system by Russian spies, who are allegedly using it to build forged identities.
AUTHORITIES IN BRAZIL HAVE launched a nationwide probe into the abuse of the country’s citizenship documentation system by Russian spies, who are allegedly using it to build forged identities.  INTENSIFYING COMPETITION BETWEEN THE superpowers has turned Switzerland into an espionage battlefield, with more foreign spies being active there than in most other European countries, according to a new report. The
INTENSIFYING COMPETITION BETWEEN THE superpowers has turned Switzerland into an espionage battlefield, with more foreign spies being active there than in most other European countries, according to a new report. The  A CHINESE COURT HAS sentenced a United States passport holder to life in prison on espionage charges, following a brief closed-door trial. However, no information has been made available about the precise charges against him. Closed-door trials are frequent occurrences in Chinese courts, especially in cases relating to national security, which include charges of espionage against the state. However, life sentences are exceedingly rare for espionage cases.
A CHINESE COURT HAS sentenced a United States passport holder to life in prison on espionage charges, following a brief closed-door trial. However, no information has been made available about the precise charges against him. Closed-door trials are frequent occurrences in Chinese courts, especially in cases relating to national security, which include charges of espionage against the state. However, life sentences are exceedingly rare for espionage cases. SOUTH KOREAN PROSECUTORS have charged four senior members of one of the country’s largest trade unions with espionage on behalf of North Korea. The move, which is seen as highly controversial by South Korea’s liberal opposition, has come a few months after the conservative administration of President Yoon Suk Yeol
SOUTH KOREAN PROSECUTORS have charged four senior members of one of the country’s largest trade unions with espionage on behalf of North Korea. The move, which is seen as highly controversial by South Korea’s liberal opposition, has come a few months after the conservative administration of President Yoon Suk Yeol  AUTHORITIES IN POLAND HAVE seized an abandoned school building in the Polish capital Warsaw, allegedly because it was being used as a base for espionage activities by the Russian government. Following the seizure of the building complex, Russian officials issued stern but vague warnings, saying that action will be taken in response to what they termed as an “act of provocation” by the Polish government.
AUTHORITIES IN POLAND HAVE seized an abandoned school building in the Polish capital Warsaw, allegedly because it was being used as a base for espionage activities by the Russian government. Following the seizure of the building complex, Russian officials issued stern but vague warnings, saying that action will be taken in response to what they termed as an “act of provocation” by the Polish government. AN AUSTRALIAN BUSINESSMAN, WHO has worked in China for over two decades, is facing up to 15 years in prison for allegedly selling secrets to two foreign intelligence officers. The businessman, Alexander Csergo, 55, grew up in Sydney, but moved to China in 2002 and currently works for a digital solutions firm in Shanghai. According to
AN AUSTRALIAN BUSINESSMAN, WHO has worked in China for over two decades, is facing up to 15 years in prison for allegedly selling secrets to two foreign intelligence officers. The businessman, Alexander Csergo, 55, grew up in Sydney, but moved to China in 2002 and currently works for a digital solutions firm in Shanghai. According to 
 RUSSIA’S ABILITY TO CONDUCT human intelligence operations in Europe has suffered greater damage in recent years than at any time since 1991, according to some experts. These setbacks have partly been caused by what The Washington Post refers to in a
RUSSIA’S ABILITY TO CONDUCT human intelligence operations in Europe has suffered greater damage in recent years than at any time since 1991, according to some experts. These setbacks have partly been caused by what The Washington Post refers to in a  TENSION IS MOUNTING BETWEEN the government and opposition forces in South Korea, as the conservative administration of President Yoon Suk Yeol appears to be behind an effort to probe alleged links between senior liberal political figures and North Korean intelligence. The effort, which some commentators
TENSION IS MOUNTING BETWEEN the government and opposition forces in South Korea, as the conservative administration of President Yoon Suk Yeol appears to be behind an effort to probe alleged links between senior liberal political figures and North Korean intelligence. The effort, which some commentators  A BOOK BY A former Central Intelligence Agency (CIA) case officer, which alleges that a senior Agency official sabotaged American counterintelligence efforts on orders from Moscow, has prompted a series of fiery exchanges by retired CIA personnel. The primary figures in the dispute are the book’s author, Robert Baer, and Paul J. Redmond, who served as the CIA’s Associate Deputy Director of Operations for Counterintelligence.
A BOOK BY A former Central Intelligence Agency (CIA) case officer, which alleges that a senior Agency official sabotaged American counterintelligence efforts on orders from Moscow, has prompted a series of fiery exchanges by retired CIA personnel. The primary figures in the dispute are the book’s author, Robert Baer, and Paul J. Redmond, who served as the CIA’s Associate Deputy Director of Operations for Counterintelligence.





