Opinion: Fumbling Russian spies fail to stop ISIS-K attack, despite warnings from U.S.
March 25, 2024 7 Comments
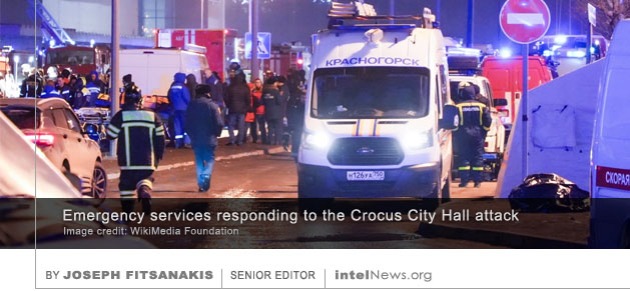 NO COUNTRY HAS BETTER intelligence on the Islamic State-Khorasan Province (known as ISIS-K) than the United States. American forces have faced ISIS-K almost from the moment the group was founded in 2015 in Pakistan, just a few miles from the Afghan border. It was there that a group of disaffected members of the Tehreek-e-Taliban-e-Pakistan (TTP, commonly referred to as the Pakistani Taliban) began turning their backs on al-Qaeda, which they saw as a failing brand, and joined the Islamic State of Iraq and Syria (ISIS).
NO COUNTRY HAS BETTER intelligence on the Islamic State-Khorasan Province (known as ISIS-K) than the United States. American forces have faced ISIS-K almost from the moment the group was founded in 2015 in Pakistan, just a few miles from the Afghan border. It was there that a group of disaffected members of the Tehreek-e-Taliban-e-Pakistan (TTP, commonly referred to as the Pakistani Taliban) began turning their backs on al-Qaeda, which they saw as a failing brand, and joined the Islamic State of Iraq and Syria (ISIS).
By 2017, ISIS-K had begun to draw to its ranks hundreds of fighters from central and south Asia, who were inspired by the group’s goal of establishing an Islamic caliphate in the lands of the greater Khorasan. The term refers to a historical region that extends from eastern Iran and Turkmenistan, to the mountains of Kyrgyzstan, containing all of present-day Afghanistan, most of Uzbekistan, and even some parts of the Russian Caucasus. Like the Islamic State of Iraq and Syria (ISIS) during its heyday, ISIS-K aspires to establish control over a territorially unified entity and then use perpetual war to expand its influence in central Asia and beyond.
Until 2021, the biggest obstacle to ISIS-K’s plan for regional domination was the U.S. By some accounts, American forces and Western-trained Afghan commando units had managed to eliminate more than half of ISIS-K’s 4,000-strong base in northeastern Afghanistan. Since the hurried U.S. withdrawal from the country in 2021 (which was marred by an ISIS-K suicide bombing that killed nearly 200 people, including 13 U.S. troops), ISIS-K has expanded its reach beyond all prior measure. The group has since claimed responsibility for attacks in Afghanistan, Pakistan, Iran, and now Russia, that have killed over 600 people and injured thousands.
A primary reason for the proliferation of ISIS-K’s terrorist activity is that the U.S., which has more intelligence than anyone on the group, issues warnings that are  not being taken into consideration by the group’s primary targets, namely Afghanistan, Iran, and Russia. Indeed, despite the Washington’s best efforts, its warnings about pending ISIS-K attacks have been ignored by the group’s primary targets. A few days after an ISIS-K attack killed nearly 100 people in Kerman, Iran, The Wall Street Journal claimed the U.S. government had provided Tehran with “a private warning” of an imminent terrorist threat from ISIS-K. If that is true, then the Iranians clearly did not heed Washington’s warning.
not being taken into consideration by the group’s primary targets, namely Afghanistan, Iran, and Russia. Indeed, despite the Washington’s best efforts, its warnings about pending ISIS-K attacks have been ignored by the group’s primary targets. A few days after an ISIS-K attack killed nearly 100 people in Kerman, Iran, The Wall Street Journal claimed the U.S. government had provided Tehran with “a private warning” of an imminent terrorist threat from ISIS-K. If that is true, then the Iranians clearly did not heed Washington’s warning.
It now appears that, once again, Washington had considerable intelligence insight into ISIS-K’s plans to strike inside Russia. On March 7, the U.S. embassy in Russia warned on its website that “extremists have imminent plans to target large gatherings in Moscow, to include concerts”. The warning provided no specifics. However, seeing how U.S. authorities issued private warnings to Iran, a country with which the U.S. has no diplomatic relations, then it is highly likely they provided similar information to Russia, which at least hosts American diplomats and intelligence officers on its soil. Yet, not only did the Russians ignore these warnings, but they openly dismissed them. Read more of this post
 THE GROWING LIST OF assassinations of prominent Russians and Ukrainian separatists shows that the Ukrainian intelligence services are using “liquidations” as a weapon of war, according to The Washington Post. Citing “current and former Ukrainian and United States officials”, the paper
THE GROWING LIST OF assassinations of prominent Russians and Ukrainian separatists shows that the Ukrainian intelligence services are using “liquidations” as a weapon of war, according to The Washington Post. Citing “current and former Ukrainian and United States officials”, the paper  Crimea, the local head of the domestic security agency, the Ukrainian Security Service (SBU) defected to Russia.
Crimea, the local head of the domestic security agency, the Ukrainian Security Service (SBU) defected to Russia. LAST WEEK, TWO SENIOR UNITED States intelligence officials shared rare insights on artificial intelligence, as they discussed some of the opportunities and threats of this new technological paradigm for their agencies. On Wednesday, Lakshmi Raman, Director of Artificial Intelligence at the Central Intelligence Agency, addressed the topic during an on-stage interview at Politico’s AI & Tech Summit in Washington, DC. On Thursday, the National Security Agency’s outgoing director, Army General Paul Nakasone, discussed the same subject at the National Press Club’s Headliners Luncheon in the US capital.
LAST WEEK, TWO SENIOR UNITED States intelligence officials shared rare insights on artificial intelligence, as they discussed some of the opportunities and threats of this new technological paradigm for their agencies. On Wednesday, Lakshmi Raman, Director of Artificial Intelligence at the Central Intelligence Agency, addressed the topic during an on-stage interview at Politico’s AI & Tech Summit in Washington, DC. On Thursday, the National Security Agency’s outgoing director, Army General Paul Nakasone, discussed the same subject at the National Press Club’s Headliners Luncheon in the US capital. FOR THE SECOND TIME in 10 days, the government of China has announced the arrest of a Chinese government employee on suspicion of spying for the United States Central Intelligence Agency (CIA). In a statement issued on Monday, China’s civilian intelligence agency, the Ministry of State Security (MSS), said it had launched an investigation into an official of a government ministry, who was allegedly caught conducting espionage on behalf of the CIA.
FOR THE SECOND TIME in 10 days, the government of China has announced the arrest of a Chinese government employee on suspicion of spying for the United States Central Intelligence Agency (CIA). In a statement issued on Monday, China’s civilian intelligence agency, the Ministry of State Security (MSS), said it had launched an investigation into an official of a government ministry, who was allegedly caught conducting espionage on behalf of the CIA. A CHINESE GOVERNMENT EMPLOYEE gave “core information” about China’s military to the United States, after he was recruited by a Central Intelligence Agency (CIA) officer in Italy, a Chinese state agency has said. The allegation was made in a statement that was issued on Friday by China’s civilian intelligence agency, the Ministry of State Security (MSS), on its WeChat social media account.
A CHINESE GOVERNMENT EMPLOYEE gave “core information” about China’s military to the United States, after he was recruited by a Central Intelligence Agency (CIA) officer in Italy, a Chinese state agency has said. The allegation was made in a statement that was issued on Friday by China’s civilian intelligence agency, the Ministry of State Security (MSS), on its WeChat social media account. THE BRAZILIAN GOVERNMENT IS blocking requests from the United States and Russia to extradite an alleged Russian deep-cover spy, whose forged Brazilian identity papers were discovered by Dutch counterintelligence. Sergey Cherkasov was
THE BRAZILIAN GOVERNMENT IS blocking requests from the United States and Russia to extradite an alleged Russian deep-cover spy, whose forged Brazilian identity papers were discovered by Dutch counterintelligence. Sergey Cherkasov was  THE RUSSIAN INTELLIGENCE SERVICES planned to assassinate a Russian former intelligence officer, who had defected to the United States and was living in an apartment complex in Florida, according to a new report. The alleged assassination plan is discussed in the forthcoming book Spies: The Epic Intelligence War Between East and West (Simon and Schuster), authored by Harvard University academic Calder Walton.
THE RUSSIAN INTELLIGENCE SERVICES planned to assassinate a Russian former intelligence officer, who had defected to the United States and was living in an apartment complex in Florida, according to a new report. The alleged assassination plan is discussed in the forthcoming book Spies: The Epic Intelligence War Between East and West (Simon and Schuster), authored by Harvard University academic Calder Walton. THE 49-PAGE GRAND JURY indictment, filed last week in Florida by the United States Department of Justice, contains 37 criminal charges against former president Donald Trump. The charges can be summarized into a two-fold accusation: Trump is alleged to have stolen more than 300 classified documents upon leaving the White House in January 2021. Moreover, he allegedly schemed with a group of advisors and aides in order to obstruct efforts by the government to retrieve the stolen documents. Both accusations are spelled out in stark detail in
THE 49-PAGE GRAND JURY indictment, filed last week in Florida by the United States Department of Justice, contains 37 criminal charges against former president Donald Trump. The charges can be summarized into a two-fold accusation: Trump is alleged to have stolen more than 300 classified documents upon leaving the White House in January 2021. Moreover, he allegedly schemed with a group of advisors and aides in order to obstruct efforts by the government to retrieve the stolen documents. Both accusations are spelled out in stark detail in  does it need to. Establishing a motive is not required in order to demonstrate the need for a trial, or indeed a conviction. Given the high stakes of this case, however, establishing a motive can provide much-needed clarity in the public sphere.
does it need to. Establishing a motive is not required in order to demonstrate the need for a trial, or indeed a conviction. Given the high stakes of this case, however, establishing a motive can provide much-needed clarity in the public sphere. his determination to keep them in close proximity to his office and sleeping quarters.
his determination to keep them in close proximity to his office and sleeping quarters. more pugilistic desires”, according to the paper. His attitude was not a show. It was sincere. Moreover, there is no reason to believe that it has subsided since his indictment.
more pugilistic desires”, according to the paper. His attitude was not a show. It was sincere. Moreover, there is no reason to believe that it has subsided since his indictment. The United States Department of Justice has
The United States Department of Justice has  RIVAL ONLINE CAMPAIGNS BY American and Russian intelligence agencies are encouraging each other’s citizens to contact them, share information and possibly even defect. At least three ads have been on social media, with the Federal Bureau of Investigation (FBI) issuing the earliest one in February of this year. The Central Intelligence Agency (CIA) and its Russian counterpart, the Foreign Intelligence Service (SVR), are now believed to have published similar ads.
RIVAL ONLINE CAMPAIGNS BY American and Russian intelligence agencies are encouraging each other’s citizens to contact them, share information and possibly even defect. At least three ads have been on social media, with the Federal Bureau of Investigation (FBI) issuing the earliest one in February of this year. The Central Intelligence Agency (CIA) and its Russian counterpart, the Foreign Intelligence Service (SVR), are now believed to have published similar ads. A CHINESE COURT HAS sentenced a United States passport holder to life in prison on espionage charges, following a brief closed-door trial. However, no information has been made available about the precise charges against him. Closed-door trials are frequent occurrences in Chinese courts, especially in cases relating to national security, which include charges of espionage against the state. However, life sentences are exceedingly rare for espionage cases.
A CHINESE COURT HAS sentenced a United States passport holder to life in prison on espionage charges, following a brief closed-door trial. However, no information has been made available about the precise charges against him. Closed-door trials are frequent occurrences in Chinese courts, especially in cases relating to national security, which include charges of espionage against the state. However, life sentences are exceedingly rare for espionage cases. AN ESPIONAGE TOOL DESCRIBED by Western officials as the most advanced in the Russian cyber-arsenal has been neutralized after a 20-year operation by intelligence agencies in the United States, Australia, Canada, the United Kingdom and New Zealand. The operation targeted
AN ESPIONAGE TOOL DESCRIBED by Western officials as the most advanced in the Russian cyber-arsenal has been neutralized after a 20-year operation by intelligence agencies in the United States, Australia, Canada, the United Kingdom and New Zealand. The operation targeted  A RUSSIAN INTELLIGENCE OPERATIVE, who lived in Maryland using forged Brazilian identity documents, has been charged with espionage and other crimes by the United States Department of Justice. Victor Muller Ferreira, a Brazilian national, was stopped from entering the Netherlands in June of last year, where he had intended to join the International Criminal Court (ICC) as an intern.
A RUSSIAN INTELLIGENCE OPERATIVE, who lived in Maryland using forged Brazilian identity documents, has been charged with espionage and other crimes by the United States Department of Justice. Victor Muller Ferreira, a Brazilian national, was stopped from entering the Netherlands in June of last year, where he had intended to join the International Criminal Court (ICC) as an intern. THE SPIRALING SOCIAL UNREST in Israel and the Palestinian Territories may harm longstanding intelligence-sharing agreements between Israel and its Western allies, including the United States, according to reports. Historically, intelligence-sharing partnerships between Israel and its closest ally, the United States, have tended to remain largely unaffected by regional upheavals. This time, however, some Israeli officials are concerned that the Israeli-American intelligence relationship is “under a question mark and under great tension”.
THE SPIRALING SOCIAL UNREST in Israel and the Palestinian Territories may harm longstanding intelligence-sharing agreements between Israel and its Western allies, including the United States, according to reports. Historically, intelligence-sharing partnerships between Israel and its closest ally, the United States, have tended to remain largely unaffected by regional upheavals. This time, however, some Israeli officials are concerned that the Israeli-American intelligence relationship is “under a question mark and under great tension”.





