Iranian state-backed cyber spies becoming increasingly skilled, says report
September 21, 2017 Leave a comment
 A group of cyber spies with close links to the Iranian government is becoming increasingly competent and adept, and could soon bring down entire computer networks, according to a leading cyber security firm. The California-based cyber security company FireEye said that it has been monitoring the operations of the mysterious group of cyber spies since 2013. The company, whose clients include Sony Pictures, JP Morgan Chase and Target, said that the Iranian group appears to be especially interested in gathering secrets from aviation, aerospace and petrochemical companies.
A group of cyber spies with close links to the Iranian government is becoming increasingly competent and adept, and could soon bring down entire computer networks, according to a leading cyber security firm. The California-based cyber security company FireEye said that it has been monitoring the operations of the mysterious group of cyber spies since 2013. The company, whose clients include Sony Pictures, JP Morgan Chase and Target, said that the Iranian group appears to be especially interested in gathering secrets from aviation, aerospace and petrochemical companies.
In a detailed report published on Wednesday, FireEye said that the Iranian group has a very narrow target focus. Moreover, it attacks its targets —which are typically companies— in highly customizable ways. The latter includes the use of cleverly designed phishing tools that are designed to attract the attention of the company’s unsuspecting employees. So far, companies that have been targeted include Saudi petrochemical conglomerates, American aviation firms, as well as South Korean and other Southeast Asian companies that have aviation or energy holdings, said FireEye. The security company said it had codenamed the group “APT33”, which stands for “Advanced Persistent Threat #33”. It also said that APT33 was clearly distinct from other known Iranian hacker groups, because of the sophistication of its operations and the quality of its cyber weapons. The cyber security firm said that APT33 was the first Iranian hacker group to be included on a select list of the most capable cyber spy groups from around the world.
Some experts believe that APT33 is run by Iran’s Revolutionary Guard Corps, an irregular branch of the Iranian military, which is seen by many as a state within a state in post-1979 Iran. The FireEye report does not appear conclusive on this point. However, it notes that APT33 has built an offensive cyber arsenal “with potential destructive capabilities”, but that it currently appears to focus solely on intelligence collection, not sabotage or warfare.
► Author: Joseph Fitsanakis | Date: 21 September 2017 | Permalink
 North Korea’s intelligence establishment has shifted its attention from spying for political gain to spying for commercial advantage –primarily to secure funds for the cash-strapped country, according to a new report. Since the 1990s, the Democratic People’s Republic of Korea (DPRK) has used computer hacking in order to steal political and military secrets from its rivals. But there is increasing evidence that Pyongyang is now deploying armies of computer hackers in order to steal cash from foreign financial institutions and internet-based firms. This is the conclusion of a new report by the Financial Security Institute of South Korea, an agency that was set up by Seoul to safeguard the stability of the country’s financial sector.
North Korea’s intelligence establishment has shifted its attention from spying for political gain to spying for commercial advantage –primarily to secure funds for the cash-strapped country, according to a new report. Since the 1990s, the Democratic People’s Republic of Korea (DPRK) has used computer hacking in order to steal political and military secrets from its rivals. But there is increasing evidence that Pyongyang is now deploying armies of computer hackers in order to steal cash from foreign financial institutions and internet-based firms. This is the conclusion of a new report by the Financial Security Institute of South Korea, an agency that was set up by Seoul to safeguard the stability of the country’s financial sector. A cyber espionage group that has alarmed security researchers by its careful targeting of government agencies has links to the Iranian state, according to a new report. The existence of the group calling itself CopyKittens was first confirmed publicly in November of 2015. Since that time, forensic analyses of cyber attacks against various targets have indicated that the group has been active since at least early 2013. During that time, CopyKittens has carefully targeted agencies or officials working for Jordan, Saudi Arabia, Turkey, Israel, the United States, and Germany, among other countries. It has also targeted specific offices and officials working for the United Nations.
A cyber espionage group that has alarmed security researchers by its careful targeting of government agencies has links to the Iranian state, according to a new report. The existence of the group calling itself CopyKittens was first confirmed publicly in November of 2015. Since that time, forensic analyses of cyber attacks against various targets have indicated that the group has been active since at least early 2013. During that time, CopyKittens has carefully targeted agencies or officials working for Jordan, Saudi Arabia, Turkey, Israel, the United States, and Germany, among other countries. It has also targeted specific offices and officials working for the United Nations. The same group cyber-spies that attacked the campaign of French presidential candidate Emmanuel Macron is now attacking German institutions that are connected to the country’s ruling coalition parties, according to a report by a leading cyber-security firm. The Tokyo-based security software company Trend Micro published a 41-page report on Tuesday, in which it tracks and traces the attacks against French and German political targets over the past two years. The report, entitled
The same group cyber-spies that attacked the campaign of French presidential candidate Emmanuel Macron is now attacking German institutions that are connected to the country’s ruling coalition parties, according to a report by a leading cyber-security firm. The Tokyo-based security software company Trend Micro published a 41-page report on Tuesday, in which it tracks and traces the attacks against French and German political targets over the past two years. The report, entitled  Russian authorities say they prevented a large-scale cyber attack by “a foreign intelligence service”, which had been designed to destabilize the country’s financial system and subvert its economy. In an official
Russian authorities say they prevented a large-scale cyber attack by “a foreign intelligence service”, which had been designed to destabilize the country’s financial system and subvert its economy. In an official 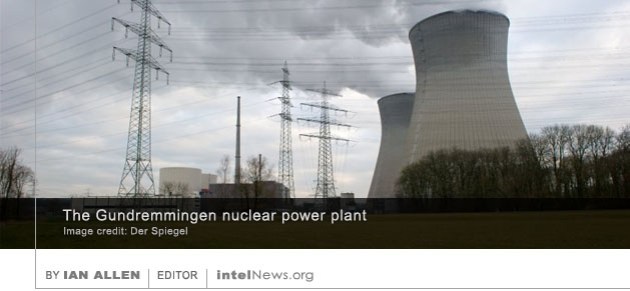 The computers of a nuclear power plant in southern Germany have been found to be infected with computer viruses that are designed to steal files and provide attackers with remote control of the system. The power plant, known as Gundremmingen, is located in Germany’s southern district of Günzburg, about 75 miles northwest of the city of Munich. The facility is owned and operated by RWE AG, Germany’s second-largest electricity producer, which is based in Essen, North Rhine-Westphalia. The company provides energy to over 30 million customers throughout Europe.
The computers of a nuclear power plant in southern Germany have been found to be infected with computer viruses that are designed to steal files and provide attackers with remote control of the system. The power plant, known as Gundremmingen, is located in Germany’s southern district of Günzburg, about 75 miles northwest of the city of Munich. The facility is owned and operated by RWE AG, Germany’s second-largest electricity producer, which is based in Essen, North Rhine-Westphalia. The company provides energy to over 30 million customers throughout Europe.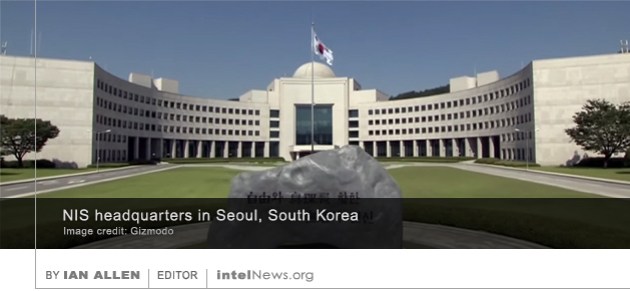 Dozens of cell phones belonging to senior government officials in South Korea were compromised by North Korean hackers who systematically targeted them with texts containing malicious codes, according to reports. The National Intelligence Service (NIS), South Korea’s primary intelligence agency, said the cell phone penetrations were part of a concerted campaign by North Korea to target smart phones belonging to South Korean senior government officials. Once they managed to compromise a cell phone, the hackers were able to access the call history stored on the device, the content of text messages exchanged with other users and, in some cases, the content of telephone calls placed on the compromised device. Moreover, according to the NIS, the hackers were able to access the contact lists stored on compromised cell phones, which means that more attacks may be taking place against cell phones belonging to South Korean government officials.
Dozens of cell phones belonging to senior government officials in South Korea were compromised by North Korean hackers who systematically targeted them with texts containing malicious codes, according to reports. The National Intelligence Service (NIS), South Korea’s primary intelligence agency, said the cell phone penetrations were part of a concerted campaign by North Korea to target smart phones belonging to South Korean senior government officials. Once they managed to compromise a cell phone, the hackers were able to access the call history stored on the device, the content of text messages exchanged with other users and, in some cases, the content of telephone calls placed on the compromised device. Moreover, according to the NIS, the hackers were able to access the contact lists stored on compromised cell phones, which means that more attacks may be taking place against cell phones belonging to South Korean government officials.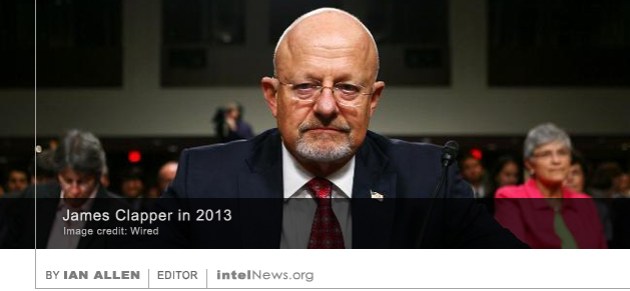 A member of a hacker group that took responsibility for breaking into the personal email account of the director of the Central Intelligence Agency last year has now hacked the email of the most senior intelligence official in the United States. In October 2015, the hacker group referred to by its members as “Crackas With Attitude” —CWA for short—
A member of a hacker group that took responsibility for breaking into the personal email account of the director of the Central Intelligence Agency last year has now hacked the email of the most senior intelligence official in the United States. In October 2015, the hacker group referred to by its members as “Crackas With Attitude” —CWA for short—  Two American firms contracted by the Department of Defense have settled a lawsuit accusing them of having hired Russian programmers based in Moscow to write computer code for classified systems. The hires allegedly occurred as part of a $613 million contract, which was awarded by the US Pentagon to Massachusetts-based Netcracker Technology Corporation and Virginia-based Computer Systems Corporation (CSC). The two companies were hired to write software for the US Defense Information Systems Agency (DISA), a Pentagon outfit that provides the US armed forces with secure real-time combat communications. But in 2011, contractor John C. Kingsley, who had a supervisory role in the project, notified the US government that the two companies had farmed out part of the contract’s coding duties to programmers in Moscow and other Russian cities.
Two American firms contracted by the Department of Defense have settled a lawsuit accusing them of having hired Russian programmers based in Moscow to write computer code for classified systems. The hires allegedly occurred as part of a $613 million contract, which was awarded by the US Pentagon to Massachusetts-based Netcracker Technology Corporation and Virginia-based Computer Systems Corporation (CSC). The two companies were hired to write software for the US Defense Information Systems Agency (DISA), a Pentagon outfit that provides the US armed forces with secure real-time combat communications. But in 2011, contractor John C. Kingsley, who had a supervisory role in the project, notified the US government that the two companies had farmed out part of the contract’s coding duties to programmers in Moscow and other Russian cities. A security firm with headquarters in Israel and the United States says it detected and neutralized an extensive cyber espionage program with direct ties to the government of Iran. The firm, called Check Point Software, which has offices in Tel Aviv and California, says it dubbed the cyber espionage program ROCKET KITTEN. In a
A security firm with headquarters in Israel and the United States says it detected and neutralized an extensive cyber espionage program with direct ties to the government of Iran. The firm, called Check Point Software, which has offices in Tel Aviv and California, says it dubbed the cyber espionage program ROCKET KITTEN. In a  The Central Intelligence Agency (CIA) pulled a number of officers from the United States embassy in Chinese capital Beijing, after a massive cyber hacking incident compromised an American federal database containing millions of personnel records. Up to 21 million individual files were
The Central Intelligence Agency (CIA) pulled a number of officers from the United States embassy in Chinese capital Beijing, after a massive cyber hacking incident compromised an American federal database containing millions of personnel records. Up to 21 million individual files were  A massive cyber hacking incident that compromised a United States federal database containing millions of personnel records also resulted in the theft of 5.6 million fingerprint records, American officials have said. Up to 21 million individual files were
A massive cyber hacking incident that compromised a United States federal database containing millions of personnel records also resulted in the theft of 5.6 million fingerprint records, American officials have said. Up to 21 million individual files were 






Israel reportedly behind discovery of Russian antivirus company’s spy links
October 11, 2017 by Joseph Fitsanakis 1 Comment
On Tuesday, The New York Times reported that the initial piece of intelligence that alerted the US government to the alleged links between Kaspersky Lab and Moscow was provided by Israel. The American paper said that Israeli cyber spies managed to hack into Kaspersky’s systems and confirm the heavy presence of Russian government operatives there. The Times’ report stated that the Israelis documented real-time cyber espionage operations by the Russians, which targeted the government computer systems of foreign governments, including the United States’. The Israeli spies then reportedly approached their American counterparts and told them that Kaspersky Lab software was being used by Russian intelligence services as a backdoor to millions of computers worldwide. The Israelis also concluded that Kaspersky’s antivirus software was used to illegally steal files from these computers, which were essentially infected by spy software operated by the Russian government.
It was following the tip by the Israelis that he Department of Homeland Security issued its memorandum saying that it was “concerned about the ties between certain Kaspersky [Lab] officials and Russian intelligence and other government agencies”. The memorandum resulted in a decision by the US government —overwhelmingly supported by Congress— to scrap all Kaspersky software from its computer systems. Kaspersky Lab has rejected allegations that it works with Russian intelligence. In a statement issued in May of this year, the company said it had “never helped, nor will help, any government in the world with its cyberespionage efforts”.
► Author: Joseph Fitsanakis | Date: 11 October 2017 | Pemalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with computer hacking, cybersecurity, Israel, Kaspersky Lab, News, Russia, United States, US Department of Homeland Security