Poland to probe alleged ties between Jeffrey Epstein and Russian intelligence
February 6, 2026 4 Comments
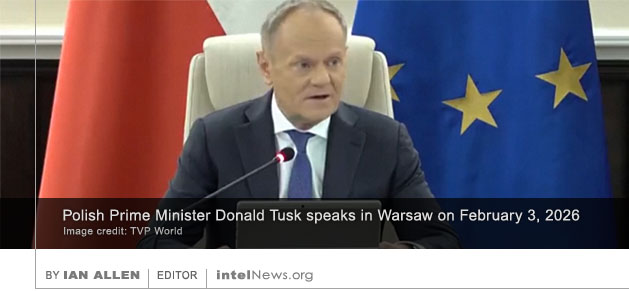
THE GOVERNMENT OF POLAND has announced plans to launch an investigation into the possibility that an international sex trafficking ring set up by the late financier and sex offender Jeffrey Epstein was a “honey trap” set up by Russian intelligence to entrap “the elites of the Western world,” according to Poland’s Prime Minister Donald Tusk.
Tusk announced the commencement of what he referred to as a “special investigation” at a press conference on Wednesday, following a senior-level government meeting. He told reporters that the investigation would be led by members of the Office of the Prime Minister in association with the Ministry of Justice and the Polish intelligence services.
In 2008 a Florida court convicted Epstein—a jet-setting financier with links to hundreds of prominent individuals in finance, politics, industry, and academia—for sex offences. The disgraced financier was found dead in his jail cell in 2019. Prosecutors in the United States say they have identified over 100 victims of Epstein’s sex-trafficking ring, but some estimates claim that as many as 1,000 other victims have yet to come forward.
At last week’s press conference, a stern-looking Tusk pointed to Epstein’s large fortune, describing it as “unexplained” and adding that it raised important questions about the late financier’s links with state actors. He reminded his audience that “a growing number of commentators and experts assume that it is highly probable that this pedophilia scandal was a premeditated operation by the Russian KGB”—a term still frequently used in Eastern European countries to refer to the post-Soviet intelligence community.
The operation may have been a “so-called ‘honey trap’, a sweet bait, a trap set for the elites of the Western world, primarily the United States,” Tusk said. The Polish prime minister then added: “I don’t need to tell you how serious the increasingly likely possibility that Russian intelligence services co-organized this operation is.” Among other things, it could “mean that they also possess compromising materials against many leaders still active today.” He added that investigators would systematically review and assess “every document currently available in the public domain.”
In a social media post later that day, Russian businessman Kirill Dimitriev, who last year was appointed by Russian President Vladimir Putin as Russia’s special presidential envoy on foreign investment and economic cooperation, dismissed the Polish government’s move. According to Dimitriev, all allegations about connections between Epstein and Russian intelligence are “lies” spread by “leftist elites.”
► Author: Ian Allen | Date: 06 February | Permalink
 A FORMER DEEP COVER Russian intelligence officer, whose cover was blown in 2010 when he was arrested in the United States, is spearheading efforts by the Kremlin to secure investments by India’s technology sector. The spy, Andrei Bezrukov, was recruited by the Soviet Committee for State Security (KGB) in the late 1970s or early 1980s—most likely alongside his wife, Elena Vavilova. For several years, the married couple lived in several countries, including Canada and France, before arriving in the United States in 1999 using fraudulently obtained Canadian passports.
A FORMER DEEP COVER Russian intelligence officer, whose cover was blown in 2010 when he was arrested in the United States, is spearheading efforts by the Kremlin to secure investments by India’s technology sector. The spy, Andrei Bezrukov, was recruited by the Soviet Committee for State Security (KGB) in the late 1970s or early 1980s—most likely alongside his wife, Elena Vavilova. For several years, the married couple lived in several countries, including Canada and France, before arriving in the United States in 1999 using fraudulently obtained Canadian passports. FRENCH AUTHORITIES HAVE ARRESTED three individuals and placed a fourth person under supervision after scrutinizing the operations of a humanitarian organization suspected of being a front for Russian intelligence. The arrests were
FRENCH AUTHORITIES HAVE ARRESTED three individuals and placed a fourth person under supervision after scrutinizing the operations of a humanitarian organization suspected of being a front for Russian intelligence. The arrests were 
 PROSECUTORS IN VIENNA HAVE charged a former intelligence officer with spying for Russia in a high-profile case that has had broad political ramifications in Austria and abroad. The criminal case centers on Egisto Ott, a former employee of Austria’s Federal Office for the Protection of the Constitution and Counterterrorism (BVT). The BVT operated as Austria’s primary domestic intelligence agency from 2002 until its dissolution in 2021.
PROSECUTORS IN VIENNA HAVE charged a former intelligence officer with spying for Russia in a high-profile case that has had broad political ramifications in Austria and abroad. The criminal case centers on Egisto Ott, a former employee of Austria’s Federal Office for the Protection of the Constitution and Counterterrorism (BVT). The BVT operated as Austria’s primary domestic intelligence agency from 2002 until its dissolution in 2021. A DISAFFECTED SOLDIER, WHO tried to commit espionage against New Zealand for a foreign government, has become the first convicted spy in the Pacific Island nation’s history. The only other time New Zealand prosecuted an individual for espionage was in 1974, when the government accused
A DISAFFECTED SOLDIER, WHO tried to commit espionage against New Zealand for a foreign government, has become the first convicted spy in the Pacific Island nation’s history. The only other time New Zealand prosecuted an individual for espionage was in 1974, when the government accused  THE MOSSAD, ISRAEL’S PRIMARY foreign-intelligence agency, played a crucial role in Israel’s most recent attack on Iran. It is clear that, without unique intelligence on key Iranian figures and nuclear sites, much of it gathered by the Mossad, the Israeli Air Force could not have been so precise and deadly against Iranian targets.
THE MOSSAD, ISRAEL’S PRIMARY foreign-intelligence agency, played a crucial role in Israel’s most recent attack on Iran. It is clear that, without unique intelligence on key Iranian figures and nuclear sites, much of it gathered by the Mossad, the Israeli Air Force could not have been so precise and deadly against Iranian targets. TWO RUSSIAN SPIES USED forged documents acquired in Brazil in order to live in Portugal for years and use it as a base from where to conduct espionage, according to an investigation by Portuguese counterintelligence. The spies were husband-and-wife team Vladimir Aleksandrovich Danilov and Yekaterina Leonidovna Danilova, both in their 30s.
TWO RUSSIAN SPIES USED forged documents acquired in Brazil in order to live in Portugal for years and use it as a base from where to conduct espionage, according to an investigation by Portuguese counterintelligence. The spies were husband-and-wife team Vladimir Aleksandrovich Danilov and Yekaterina Leonidovna Danilova, both in their 30s.  BRITAIN’S SECURITY AGENCIES HAVE reportedly warned civil servants and parliamentarians that public places located near government buildings may be bugged by foreign intelligence agencies. The warning covers the SW1 postcode district of southwest London, which encompasses the City of Westminster and includes the Houses of Parliament, the Office of the Prime Minister at 10 Downing Steet, and Whitehall. The latter is home to several ministries and departments, including the Foreign and Commonwealth Office, the Cabinet office, and the Ministry of Defense.
BRITAIN’S SECURITY AGENCIES HAVE reportedly warned civil servants and parliamentarians that public places located near government buildings may be bugged by foreign intelligence agencies. The warning covers the SW1 postcode district of southwest London, which encompasses the City of Westminster and includes the Houses of Parliament, the Office of the Prime Minister at 10 Downing Steet, and Whitehall. The latter is home to several ministries and departments, including the Foreign and Commonwealth Office, the Cabinet office, and the Ministry of Defense. FOUR TAIWANESE SOLDIERS WITH access to “extremely sensitive” secrets have received jail sentences for spying for Chinese intelligence, as Taiwanese authorities have warned of a sharp rise in Chinese espionage cases. Three of the soldiers had been detailed to the security of the Office of the President, while the fourth soldier was a member of staff at the Taiwanese Ministry of National Defense’s Information and Telecommunications Command.
FOUR TAIWANESE SOLDIERS WITH access to “extremely sensitive” secrets have received jail sentences for spying for Chinese intelligence, as Taiwanese authorities have warned of a sharp rise in Chinese espionage cases. Three of the soldiers had been detailed to the security of the Office of the President, while the fourth soldier was a member of staff at the Taiwanese Ministry of National Defense’s Information and Telecommunications Command. MUCH HAS HAPPENED IN the West and in China since Nick Eftimiades first published Chinese Espionage Operations in 1994. It was the first in-depth study of Chinese espionage operations, which for decades had been overshadowed by Soviet intelligence and their espionage operations.
MUCH HAS HAPPENED IN the West and in China since Nick Eftimiades first published Chinese Espionage Operations in 1994. It was the first in-depth study of Chinese espionage operations, which for decades had been overshadowed by Soviet intelligence and their espionage operations. LAST MONTH, ISRAEL ARRESTED two reservists following an investigation that lasted several months and centered on uncovering espionage for an Iranian state entity during wartime. The two reservists had completed their regular military service before joining the reserves.
LAST MONTH, ISRAEL ARRESTED two reservists following an investigation that lasted several months and centered on uncovering espionage for an Iranian state entity during wartime. The two reservists had completed their regular military service before joining the reserves. THE OFFICE OF THE Federal Prosecutor in Germany has charged three dual German-Russian citizens with acts of espionage on behalf of Russia, with the intent of harming the national security of the German state. In compliance with German privacy laws, the three espionage suspects have been publicly identified only by their first names and last name initials. They are: Dieter S., Alex D., and Alexander J.
THE OFFICE OF THE Federal Prosecutor in Germany has charged three dual German-Russian citizens with acts of espionage on behalf of Russia, with the intent of harming the national security of the German state. In compliance with German privacy laws, the three espionage suspects have been publicly identified only by their first names and last name initials. They are: Dieter S., Alex D., and Alexander J. RUSSIA’S NEED TO GATHER intelligence from Scandinavian targets has increased considerably since Finland and Sweden joined the North Atlantic Treaty Organization (NATO), prompting Moscow to seek nontraditional means of collecting intelligence, according to Finland’s spy agency. A new
RUSSIA’S NEED TO GATHER intelligence from Scandinavian targets has increased considerably since Finland and Sweden joined the North Atlantic Treaty Organization (NATO), prompting Moscow to seek nontraditional means of collecting intelligence, according to Finland’s spy agency. A new 






France arrests alleged Chinese spies living in small village—four arrests so far
February 11, 2026 by Joseph Fitsanakis 7 Comments
Two of the arrests took place on-site at a property in Camblanes-et-Meynac, a picturesque village located around 10 miles from Bordeaux in south-western France’s Gironde region. The property had reportedly been rented through the rental broker application Airbnb by two Chinese nationals who arrived in France in January. They are believed to have entered the country using work visas as engineers for a wireless telecommunications firm.
After settling in Camblanes-et-Meynac, the men erected a large parabolic antenna system in the garden of the rented property. The move reportedly alarmed locals, who noticed that their own Internet service experienced disruptions following the erection of the parabolic antenna system by the Chinese nationals. A local family proceeded to alert local authorities about the antenna.
According to reports the DGSI arrested two Chinese nationals aged 27 and 29, while also seizing a substantial quantity of computer and satellite equipment that was found on the property. Two other men reportedly “of Chinese origin” but based in France, were also arrested over the weekend. They were charged with providing assistance to the two residents of the Airbnb property by illegally importing the satellite equipment installed on the property. Their identities have not been released by the authorities.
The French prosecutor’s office stated that the suspects were engaged in efforts to “capture satellite data from the Starlink [mobile broadband] network”. They were also allegedly trying to intercept communications data from “vital entities” in the military realm and “retransmit them to their country of origin”, namely China, according to the statement. They are now in custody facing charges of “delivering information to a foreign power […] likely to damage the interests” of France—a standard phraseology used in the French legal code to describe foreign espionage.
France’s Gironde region has long been an epicenter of espionage by international actors due to its proximity to a growing number of facilities and restricted sites related to critical telecommunication, aerospace, and defense industries. Several small towns and villages in the area are in proximity to the industrial core of France’s defense, space and aeronautics operations.
► Author: Joseph Fitsanakis | Date: 11 February 2026 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with China, DGSI (France), espionage, France, News, SIGINT, Starlink, telecommunications