Malware targeting ex-Soviet states has Russian hallmarks
August 15, 2014 Leave a comment
 By IAN ALLEN | intelNews.org
By IAN ALLEN | intelNews.org
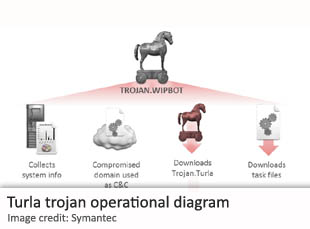
A malicious software that has infiltrated the computer systems of dozens of embassies belonging to former Eastern Bloc nations “has all the hallmarks of a nation-state” cyberespionage operation, according to researchers. Security firm Symantec said last week that the malware appears to be specifically targeting embassies of former communist nations located in China, Jordan, as well as in locations across Western Europe. In a report published on its website, Symantec said “only a nation state” was likely to have the funds and technical resources to create a malware of such complexity. Additionally, the malware seems to be designed “to go after explicit government networks that are not easy to find”, according to Symantec senior security researcher Vikram Thakur. The infiltration appears to occur in two stages. In the first stage, a computer is infected with a reconnaissance program, known as Wipbot. The initial infection usually occurs through a directed phishing attack or via a compromised website. The Wipbot then conducts an initial exploration of the infected system, collecting vital information about its identity, structure and contents. It then proceeds to compromise it only if it matches a specific Internet address that it is looking for. If a match is confirmed, the Wipbot then invites a second program into the compromised system, whose task is to expropriate data and exfiltrate it in batches that are camouflaged as Internet browser requests. Symantec researchers say that the technical similarities between the two programs are sufficient to justify the view that they were designed and developed by programmers working for the same government agency. Thakur said the structure of the malware is particularly creative; it uses Wipbot as an initial reconnaissance tool before delivering the exfiltration program if it judges that the compromised system is of high enough interest. The Symantec report adds that the malware in question is part of a four-year-long series of cyberespionage attacks that have systematically targeted government facilities belonging to former Communist Bloc states. In May of 2012, a similar malware was found to have infiltrated over 60 different computer systems belonging to a former Soviet Republic, including the office of the Prime Minister. A closely linked attack targeted another former communist state’s embassy in Paris, France, as well as its foreign and internal affairs ministries. The Symantec research points out that many of the malicious program’s core components were compiled in the UTC+4 time zone, which includes Russian cities such as Moscow and St. Petersburg.








Researchers uncover ‘ambitious’ Iranian hacker group that targets the Middle East
July 26, 2018 by Joseph Fitsanakis 1 Comment
In a report published on Wednesday, Symantec said that its security experts managed to obtain what appears to be Leafminer’s master list of targets. The list is written in the Farsi language and contains just over 800 organizations, which according to Symantec researchers is “an ambitious goal” for any cyber espionage group. The organizations listed on the target sheet come from a variety of sectors, including government, transportation, the financial sector, energy and telecommunications. But the majority of the group’s targets appear to be in the petrochemical and government sectors. Additionally, virtually all of Leafminer’s targets are located in the Middle East and North Africa, in countries such as Israel, Egypt, Bahrain, Qatar, Kuwait and the United Arab Emirates. Some of the group’s targets are located in Afghanistan and Azerbaijan.
Symantec said its researchers observed the Leafminer hackers execute attacks in real time on at least 40 targets in the Middle East, including on the website of an intelligence agency in Lebanon. According to the cyber security company, Leafminer uses a variety of hacking tools, including custom-designed malware and some publicly available software. The group’s operational sophistication is also varied, and ranges from complex, multilayered attacks to brute-force login attempts. Symantec said it concluded that the cyber espionage group originates from Iran because its master target list is written in Farsi and because Iran is virtually the only country in the Middle East that is missing from the target list. However, it said that it did not have sufficient evidence to link Leafminer to the Iranian government. In a separate development, Germany’s domestic intelligence agency, the Federal Office for the Protection of the Constitution (BfV), said this week in its annual report that the government of Iran has significantly expanded its cyber warfare capabilities and “poses a danger to German companies and research institutions”.
► Author: Joseph Fitsanakis | Date: 26 July 2018 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with computer hacking, cyberespionage, cybersecurity, Iran, Leafminer, News, Symantec Corporation