FBI examining FaceApp over potential counterintelligence concerns
December 3, 2019 1 Comment
 The United States Federal Bureau of Investigation says it is examining possible counterintelligence threats in connection with the popular online application FaceApp, which is headquartered in Russia. The application first made its appearance in January of 2017 and quickly became popular among smartphone users around the world. It allows users to upload a photograph of their face and then edit it with the help of artificial-intelligence software. The software can change the user’s photograph to make it look younger or older, or make it look as if it is from the opposite gender. The result can be impressively realistic and life-like.
The United States Federal Bureau of Investigation says it is examining possible counterintelligence threats in connection with the popular online application FaceApp, which is headquartered in Russia. The application first made its appearance in January of 2017 and quickly became popular among smartphone users around the world. It allows users to upload a photograph of their face and then edit it with the help of artificial-intelligence software. The software can change the user’s photograph to make it look younger or older, or make it look as if it is from the opposite gender. The result can be impressively realistic and life-like.
The St. Petersburgh-based company behind FaceApp, Wireless Lab, claims that the photos of users are uploaded to cloud servers situated in New Zealand, Australia and Singapore. They are then deleted within two days from the moment they are uploaded by users, without ever being transferred to servers located in the territory of Russia. But the FBI does not seem to believe these assurances. In a letter sent late last month to the Minority Leader of the US Senate, Charles Schumer (D-NY), the Bureau said it was examining FaceApp as part of its counterintelligence mission.
In the letter, which was published on Monday, Jill Tyson, Assistant Director of the FBI’s Office of Congressional Affairs, said the fact that Wireless Lab is based in Russia raised a number of counterintelligence concerns. These relate to the types of data Wireless Lab collects on its customers and the privacy policies that apply to Russian Internet companies. According to Tyson, the Russian Federal Security Service (FSB) has the right to “remotely access all communications and servers on Russian networks without making a request” to network providers. He added that, if the FBI found that FaceApp was involved in activities meant to interfere with upcoming elections in the United States, the Bureau would investigate the matter further, and possibly involve the Foreign Influence Task Force, an FBI-led body that was established after the 2016 US presidential elections.
The FBI’s letter was written in response to an earlier letter sent to the Bureau by Senator Schumer in July, which expressed concerns about potential threats posed by FaceApp to the privacy of American Internet users and to the nations’ security as a whole.
► Author: Joseph Fitsanakis | Date: 03 December 2019 | Permalink
 The European multinational aerospace corporation Airbus has fired 16 of its employees for illegally possessing classified documents belonging to the German military. The Netherlands-registered aviation company, one of the world’s largest, has been cooperating with an investigation into the incident. The probe has been led by German authorities since September of 2018.
The European multinational aerospace corporation Airbus has fired 16 of its employees for illegally possessing classified documents belonging to the German military. The Netherlands-registered aviation company, one of the world’s largest, has been cooperating with an investigation into the incident. The probe has been led by German authorities since September of 2018.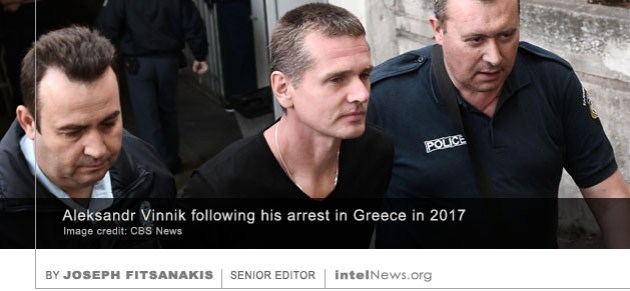 An intense fight between the United States and Russia over the extradition of a Russian cryptocurrency tycoon being held in Greece, is raising questions about the possible use of cryptocurrencies by spies. The tycoon in question is Aleksandr Vinnik, 39, who in 2011 co-founded BTC-e, an international cryptocurrency-trading platform. BTC-e allowed users to buy or sell several popular cryptocurrencies, including bitcoin and litecoin, using Russian rubles, United States dollars, or European Union euro currencies. Although headquartered in Russia, BTC-e’s servers were located in Bulgaria, while its operations were conducted through its offshore components in Cyprus and the Seychelles.
An intense fight between the United States and Russia over the extradition of a Russian cryptocurrency tycoon being held in Greece, is raising questions about the possible use of cryptocurrencies by spies. The tycoon in question is Aleksandr Vinnik, 39, who in 2011 co-founded BTC-e, an international cryptocurrency-trading platform. BTC-e allowed users to buy or sell several popular cryptocurrencies, including bitcoin and litecoin, using Russian rubles, United States dollars, or European Union euro currencies. Although headquartered in Russia, BTC-e’s servers were located in Bulgaria, while its operations were conducted through its offshore components in Cyprus and the Seychelles. As the Australian government has launched an official investigation into the claims made by a self-styled Chinese intelligence defector, some skeptics have begun to cast doubts about his revelations. The claims of Wang “William” Liqiang have dominated news headlines in Australia for over a week. The 26-year-old from China’s eastern Fujian province reportedly defected to Australia in October, while visiting his wife and newborn son in Sydney. He is currently reported to be in a safe house belonging to the Australian Security Intelligence Organization (ASIO).
As the Australian government has launched an official investigation into the claims made by a self-styled Chinese intelligence defector, some skeptics have begun to cast doubts about his revelations. The claims of Wang “William” Liqiang have dominated news headlines in Australia for over a week. The 26-year-old from China’s eastern Fujian province reportedly defected to Australia in October, while visiting his wife and newborn son in Sydney. He is currently reported to be in a safe house belonging to the Australian Security Intelligence Organization (ASIO). The law enforcement agency of the European Union, in cooperation with the popular online messaging service Telegram, has culled thousands of Islamic State online accounts in what it described as “a day of action”. The operation was coordinated by the European Union Agency for Law Enforcement Cooperation, better known as Europol. The agency coordinated its activities with the popular instant-messaging service Telegram, which the Islamic State has used as its main platform of mass communication since 2014.
The law enforcement agency of the European Union, in cooperation with the popular online messaging service Telegram, has culled thousands of Islamic State online accounts in what it described as “a day of action”. The operation was coordinated by the European Union Agency for Law Enforcement Cooperation, better known as Europol. The agency coordinated its activities with the popular instant-messaging service Telegram, which the Islamic State has used as its main platform of mass communication since 2014. A Chinese intelligence defector has reportedly given the Australian government information about entire networks of Chinese undercover spies in Hong Kong, Taiwan and Australia, according to reports. The story of Wang “William” Liqiang, made headlines all over Australia during the weekend, culminating in an entire
A Chinese intelligence defector has reportedly given the Australian government information about entire networks of Chinese undercover spies in Hong Kong, Taiwan and Australia, according to reports. The story of Wang “William” Liqiang, made headlines all over Australia during the weekend, culminating in an entire  South Korea appears determined to reject calls from the United States to maintain an intelligence-sharing agreement with Japan, as relations between Seoul, Tokyo and Washington continue to experience tensions. The South Korean government has been issuing warnings since August that it will
South Korea appears determined to reject calls from the United States to maintain an intelligence-sharing agreement with Japan, as relations between Seoul, Tokyo and Washington continue to experience tensions. The South Korean government has been issuing warnings since August that it will  Turkish authorities have charged a lawyer working for the German embassy in Ankara with espionage, further-straining the already tense relationship between the two North Atlantic Treaty Organization allies. German newsmagazine Der Spiegel, which
Turkish authorities have charged a lawyer working for the German embassy in Ankara with espionage, further-straining the already tense relationship between the two North Atlantic Treaty Organization allies. German newsmagazine Der Spiegel, which 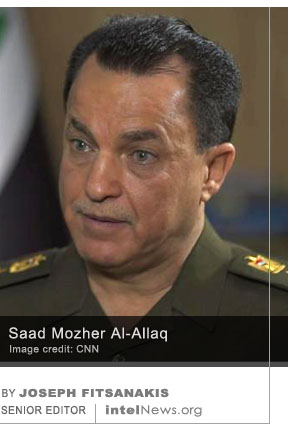 In a rare interview, the head of Iraq’s military intelligence has warned of an impending “catastrophe” as the Islamic State continues to edge ever-closer to rebuilding its networks of fighters and supporters in the Middle East. Lieutenant General Saad Mozher Al-Allaq, head of Iraq’s Military Intelligence Directorate, gave a rare
In a rare interview, the head of Iraq’s military intelligence has warned of an impending “catastrophe” as the Islamic State continues to edge ever-closer to rebuilding its networks of fighters and supporters in the Middle East. Lieutenant General Saad Mozher Al-Allaq, head of Iraq’s Military Intelligence Directorate, gave a rare  A rare three-way spy-swap has reportedly taken place between Russia and two North Atlantic Treaty Organization (NATO) members, Lithuania and Norway. Rumors of a possible exchange of imprisoned spies between the three countries first
A rare three-way spy-swap has reportedly taken place between Russia and two North Atlantic Treaty Organization (NATO) members, Lithuania and Norway. Rumors of a possible exchange of imprisoned spies between the three countries first 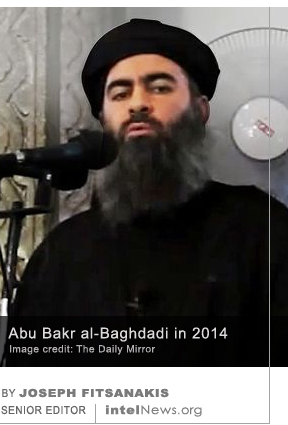 The Islamic State’s Syrian hideout that housed the group’s leader until his demise on October 26, was equipped with a frequently used internet connection, according to Arab media reports. Abu Bakr al-Baghdaid, the self-proclaimed caliph of the Islamic State, was killed by United States soldiers in Barisha, a village in the Syrian province of Idlib, which is located
The Islamic State’s Syrian hideout that housed the group’s leader until his demise on October 26, was equipped with a frequently used internet connection, according to Arab media reports. Abu Bakr al-Baghdaid, the self-proclaimed caliph of the Islamic State, was killed by United States soldiers in Barisha, a village in the Syrian province of Idlib, which is located  The former director of Venezuela’s military spy agency, who is wanted in the United States for drug trafficking, reportedly disappeared in Spain as authorities there were attempting to extradite him to Washington. Hugo Carvajal is a retired general and former diplomat, who was a member of the late Venezuelan President Hugo Chávez’s inner circle. From 2004 to 2011, under Chávez’s tutelage, Carvajal headed the Directorate General of Military Counterintelligence (DGCIM).
The former director of Venezuela’s military spy agency, who is wanted in the United States for drug trafficking, reportedly disappeared in Spain as authorities there were attempting to extradite him to Washington. Hugo Carvajal is a retired general and former diplomat, who was a member of the late Venezuelan President Hugo Chávez’s inner circle. From 2004 to 2011, under Chávez’s tutelage, Carvajal headed the Directorate General of Military Counterintelligence (DGCIM). A data dump of unprecedented scale includes usernames, IP addresses and even the content of thousands of private chat logs stolen from an influential neo-Nazi website that is now defunct. The data belonged to IronMarch, which was founded in 2011 by Alexander Mukhitdinov, a Russian far-right activist using the online nom-de-guerre “Slavros”. In the nearly six years of its existence, the website featured some of the most extreme and uncompromising far-right content on the World Wide Web.
A data dump of unprecedented scale includes usernames, IP addresses and even the content of thousands of private chat logs stolen from an influential neo-Nazi website that is now defunct. The data belonged to IronMarch, which was founded in 2011 by Alexander Mukhitdinov, a Russian far-right activist using the online nom-de-guerre “Slavros”. In the nearly six years of its existence, the website featured some of the most extreme and uncompromising far-right content on the World Wide Web. Authorities in Turkey were concerned that Russia might bomb the presidential palace in Ankara in 2015, to retaliate against the downing of a Russian fighter jet by the Turkish military, according to an intelligence report. On November 25 of that year, a Russian Sukhoi Su-24M attack bomber was shot down by a Turkish F-16 fighter jet over the Syrian-Turkish border. Ankara claimed that the Russian aircraft had violated Turkish airspace for longer than five minutes and had failed to respond to 10 warning messages communicated by radio. By the time the Russian plane was fired upon it was nearly 1.5 miles inside Turkish airspace, according to Turkey’s Ministry of Defense. But the Kremlin claimed that the downed aircraft had been flying a mile south of the Turkish border when it was shot down.
Authorities in Turkey were concerned that Russia might bomb the presidential palace in Ankara in 2015, to retaliate against the downing of a Russian fighter jet by the Turkish military, according to an intelligence report. On November 25 of that year, a Russian Sukhoi Su-24M attack bomber was shot down by a Turkish F-16 fighter jet over the Syrian-Turkish border. Ankara claimed that the Russian aircraft had violated Turkish airspace for longer than five minutes and had failed to respond to 10 warning messages communicated by radio. By the time the Russian plane was fired upon it was nearly 1.5 miles inside Turkish airspace, according to Turkey’s Ministry of Defense. But the Kremlin claimed that the downed aircraft had been flying a mile south of the Turkish border when it was shot down.






Switzerland claims embassy worker was abducted by Sri Lankan security officers
December 4, 2019 by Joseph Fitsanakis Leave a comment
The men eventually forced the Swiss embassy employee, who is a Sri Lankan national, to unlock her personal cell phone. According to Swiss government officials, they appeared to be looking for information about a senior Sri Lankan police detective who recently fled to Switzerland with his family and was granted political asylum. Some Sri Lankan media identified the man as Nishantha Silva, a police detective who until recently headed the Sri Lankan Criminal Intelligence Division’s Organized Crime Investigation Unit.
Silva is one of hundreds of members of Sri Lanka’s public sector who have fled abroad following the election of President Gotabaya Rajapaksa last month. The Rajapaksa family is one of the most powerful in the country, and has a long history of influencing Sri Lankan politics. Hours after assuming power, the ultra-nationalist Rajapaksa pledged to “hunt down” the leadership of the police and security services who investigated his family after 2015, when the Rajapaksas were ousted from the government. Hundreds of police and security officers have since been arrested or summarily fired.
On Tuesday, a Swiss Foreign Ministry spokesman told The New York Times that the Swiss government had verified the details of the abduction of its embassy worker. The spokesman added that the employee was forced to disclose “embassy-related information” after she was “threatened at length” by the men. The latter released her after warning her that she would be killed if she spoke to anyone about her ordeal.
On Monday, a spokesman for President Rajapaksa told reporters in Colombo that the Sri Lankan government questioned the accuracy of the Swiss embassy worker’s account of her abduction. Later, however, the Sri Lankan government announced that it had launched an investigation into the allegations. It now appears that the Sri Lankan government is preventing the embassy worker from leaving the country while the investigation into her claims is underway.
► Author: Joseph Fitsanakis | Date: 04 December 2019 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with abductions, diplomatic security, Gotabaya Rajapaksa, News, Sri Lanka, Swiss embassy in Sri Lanka, Switzerland