Finnish intelligence identifies Chinese state-linked group behind cyber-attack
March 19, 2021 3 Comments

FINLAND’S INTELLIGENCE AGENCY HAS identified a hacker group with ties to the Chinese state as the culprit of an attack of “exceptional” magnitude and intensity that targeted the Finnish Parliament last year. The attack was reported in December 2020, but had been going on for several weeks prior to being discovered by the information security department of the Eduskunta (Parliament of Finland).
Finland’s National Bureau of Investigation (NIB) said at the time that the attack had compromised parts of the Parliament’s internal communication system, including a number of Parliamentary email accounts. Some of these accounts belonged to members of Parliament, while others belonged to members of staff, according to the NIB.
Little became known about the attack in the months after the incident was first reported by Finnish media. But on Thursday the Finnish Security and Intelligence Service (SUPO) issued a press release about the incident. It said that the attack was likely part of a state-sponsored cyber espionage operation. It also identified those responsible for the attack as Advanced Persistent Threat (APT) 31. The SUPO report did not name the state that sponsored the attack. However, several private computer security firms have linked APT31 with the Chinese government.
The SUPO report stated that the attack on the Finnish Parliament was neither random nor experimental. On the contrary, it was aimed at acquiring specific information stored at the Parliament’s computer servers. Although the motive for the attack is still being investigated, it is possible that it was part of an effort “to gather intelligence to benefit a foreign state or to harm Finland’s interests”, said SUPO. The spy agency added that it would not provide further details about the case while it remains the subject a criminal investigation.
► Author: Joseph Fitsanakis | Date: 19 March 2021 | Permalink
 A WEB SERVER BASED in Holland and owned by a company registered in Cyprus is being used by the Iranian government to spy on its critics abroad, according to Dutch public radio. The information about Iranian espionage was
A WEB SERVER BASED in Holland and owned by a company registered in Cyprus is being used by the Iranian government to spy on its critics abroad, according to Dutch public radio. The information about Iranian espionage was 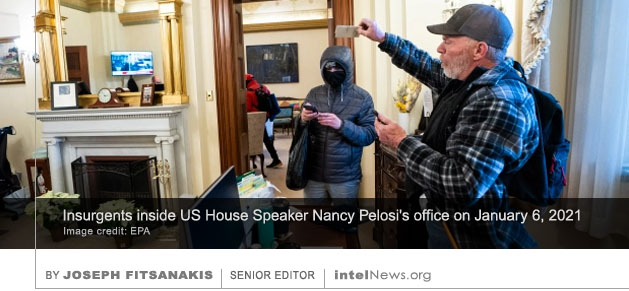 THE INSURGENTS WHO STORMED the United States Capitol Building Complex on January 6 may have unwittingly provided cover for teams of foreign spies, who could have stolen or compromised sensitive electronic equipment. This largely neglected security-related aspect of the attack is discussed in an
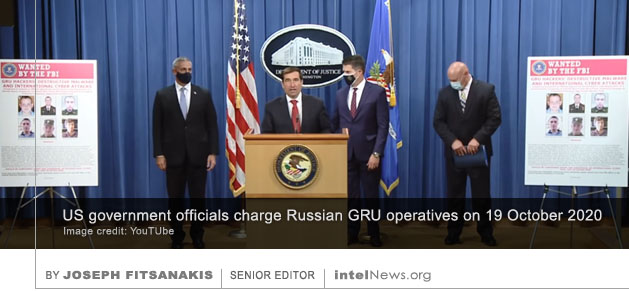
THE INSURGENTS WHO STORMED the United States Capitol Building Complex on January 6 may have unwittingly provided cover for teams of foreign spies, who could have stolen or compromised sensitive electronic equipment. This largely neglected security-related aspect of the attack is discussed in an  A large-scale cyberespionage attack targeting United States government computer systems, which some experts
A large-scale cyberespionage attack targeting United States government computer systems, which some experts 

 Belarus experienced large-scale cyberattacks that crippled many government websites, while parts of the Internet were inoperative during a national election on Sunday, as large-scale demonstrations
Belarus experienced large-scale cyberattacks that crippled many government websites, while parts of the Internet were inoperative during a national election on Sunday, as large-scale demonstrations  Computer hackers working for North Korea launched cyberattacks against carefully selected officials of national delegations belonging to the United Nations Security Council, according to a soon-to-be released report. The report is expected to be submitted early next month to the UN Security Council Sanctions Committee on North Korea.
Computer hackers working for North Korea launched cyberattacks against carefully selected officials of national delegations belonging to the United Nations Security Council, according to a soon-to-be released report. The report is expected to be submitted early next month to the UN Security Council Sanctions Committee on North Korea.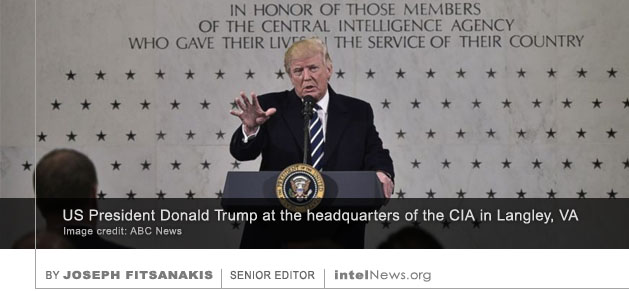 The United States Central Intelligence Agency was secretly authorized by the White House in 2018 to drastically expand its offensive cyber operation program —a development that some experts describe as a significant development for the secretive spy agency. However, the move has reportedly not pleased the Department of Defense, which sees itself as the primary conduit of American offensive operations in cyberspace.
The United States Central Intelligence Agency was secretly authorized by the White House in 2018 to drastically expand its offensive cyber operation program —a development that some experts describe as a significant development for the secretive spy agency. However, the move has reportedly not pleased the Department of Defense, which sees itself as the primary conduit of American offensive operations in cyberspace. A cyberattack, coupled with a disinformation campaign, targeted the computer systems of the United States Department of Health and Human Services (HHS), in what officials believe was an effort to undermine America’s response to the coronavirus pandemic.
A cyberattack, coupled with a disinformation campaign, targeted the computer systems of the United States Department of Health and Human Services (HHS), in what officials believe was an effort to undermine America’s response to the coronavirus pandemic. A leading Chinese cybersecurity firm has accused the United States Central Intelligence Agency of using sophisticated malicious software to hack into computers belonging to the Chinese government and private sector for over a decade.
A leading Chinese cybersecurity firm has accused the United States Central Intelligence Agency of using sophisticated malicious software to hack into computers belonging to the Chinese government and private sector for over a decade. A data dump of unprecedented scale includes usernames, IP addresses and even the content of thousands of private chat logs stolen from an influential neo-Nazi website that is now defunct. The data belonged to IronMarch, which was founded in 2011 by Alexander Mukhitdinov, a Russian far-right activist using the online nom-de-guerre “Slavros”. In the nearly six years of its existence, the website featured some of the most extreme and uncompromising far-right content on the World Wide Web.
A data dump of unprecedented scale includes usernames, IP addresses and even the content of thousands of private chat logs stolen from an influential neo-Nazi website that is now defunct. The data belonged to IronMarch, which was founded in 2011 by Alexander Mukhitdinov, a Russian far-right activist using the online nom-de-guerre “Slavros”. In the nearly six years of its existence, the website featured some of the most extreme and uncompromising far-right content on the World Wide Web.






Chinese hackers used Facebook to target Uighur activists with malware
March 25, 2021 by Joseph Fitsanakis 4 Comments
CHINESE HACKERS USED FAKE Facebook accounts to target individual activists in the expatriate Uighur community and infect their personal communications devices with malware, according to Facebook. The social media company said on Wednesday that the coordinated operation targeted approximately 500 Uighur activists living in the United States, Canada, Australia, Syria, Turkey and Kazakhstan.
At least 12 million Uighurs, most of them Muslims, live in China’s Xinjiang region, which is among the most impoverished in the country. The Chinese state is currently engaged in a campaign to quell separatist tendencies among some Uighurs, while forcibly integrating the region’s population into mainstream culture through a state-run program of forcible assimilation. It is believed that at least a million Uighurs are currently living in detention camps run by the Communist Party of China, ostensibly for “re-education”. Meanwhile, thousands of Uighur expatriates, most of whom live in Kazakhstan and Turkey, are engaged in a concerted campaign aimed at airing human-rights violations occurring in the Chinese detention camps throughout Xinjiang.
According to Facebook, Chinese hackers set up around 100 accounts of fake personas claiming to be journalists with an interest in reporting on human rights, or pro-Uighur activists. They then befriended actual Uighur activists on Facebook and directed them to fake websites that were designed to resemble popular Uighur news agencies and pro-activist websites. However, these websites were carriers of malware, which infected the personal communications devices of those who visited them. Some Facebook users were also directed to fake smartphone application stores, from where they downloaded Uighur-themed applications that contained malware.
Facebook said it was able to detect and disrupt the fake account network, which has now been neutralized. It also said it was able to block all fake domains associated with the hacker group, and notified users who were targeted by the hackers. It added that its security experts were not able to discern direct connections between the hackers an the Chinese state.
► Author: Joseph Fitsanakis | Date: 25 March 2021 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with China, computer hacking, Facebook, News, separatism, social networking, Uighurs