Researchers uncover secretive Russian spy unit by studying its commemorative badges
July 21, 2025 2 Comments
 A GROUP OF RESEARCHERS in Finland have managed to outline the structure and geographic footprint of a highly secretive Russian signals intelligence (SIGINT) unit by studying commemorative badges issued by the Russian government. The research group, known as CheckFirst, specializes in open-source (OSINT) investigative reporting and works to combat online disinformation.
A GROUP OF RESEARCHERS in Finland have managed to outline the structure and geographic footprint of a highly secretive Russian signals intelligence (SIGINT) unit by studying commemorative badges issued by the Russian government. The research group, known as CheckFirst, specializes in open-source (OSINT) investigative reporting and works to combat online disinformation.
Earlier this month, CheckFirst published its latest report titled “OSINT & Phaleristics: Unveiling FSB’s 16th Center SIGINT Capabilities”. The 36-page report focuses on the study of Russian government-issued commemorative badges—also known as challenge coins—relating to Center 16 (16-й Центр). Also known as Military Unit 71330, Center 16 is a secretive SIGINT unit that houses most of the cyber espionage capabilities of Russia’s Federal Security Service (FSB).
Challenge coins are custom-made medallions given by military, intelligence, and government agencies to recognize service, commemorate achievements, or build morale. Originating in the United States military during World War I, and popularized during the Vietnam War, challenge coins are routinely exchanged in ceremonies or offered to personnel as tokens of camaraderie and loyalty within a specific unit or mission.
Often regarded as collectors’ items, challenge coins from various agencies are often resold on websites such as eBay, or displayed online on websites maintained by private collectors. CheckFirst researchers tracked down several versions of Center 16 challenge coins found on a variety of publicly available websites, as well as on the websites of Russian challenge coin manufacturers, such as GosZnak, SpetsZnak, or Breget.
Based on this OSINT methodology, CheckFirst researchers were able to identify 10 distinct directorates within Center 16, which specialize on various aspects of defensive and offensive cyber espionage. Previously only a single Center 16 directorate had been identified in the unclassified domain. Moreover, by examining geographic indicators found on several of challenge coins, such as maps or coordinates, CheckFirst researchers were able to partly map out the geographic structure of Center 16, locating nearly a dozen interception facilities throughout Russia.
► Author: Joseph Fitsanakis | Date: 21 July 2025 | Permalink
 AN ESPIONAGE TOOL DESCRIBED by Western officials as the most advanced in the Russian cyber-arsenal has been neutralized after a 20-year operation by intelligence agencies in the United States, Australia, Canada, the United Kingdom and New Zealand. The operation targeted
AN ESPIONAGE TOOL DESCRIBED by Western officials as the most advanced in the Russian cyber-arsenal has been neutralized after a 20-year operation by intelligence agencies in the United States, Australia, Canada, the United Kingdom and New Zealand. The operation targeted  Three former employees of American spy agencies, who helped the United Arab Emirates hack targets around the world, including United States citizens, have agreed to cooperate with the investigation into their activities. The US Department of Justice said on Tuesday that it had reached a “deferred prosecution agreement” with the three Americans, Ryan Adams, Marc Baier and Daniel Gericke. At least two of them are believed to have worked for the US National Security Agency before transferring their skills to the private sector.
Three former employees of American spy agencies, who helped the United Arab Emirates hack targets around the world, including United States citizens, have agreed to cooperate with the investigation into their activities. The US Department of Justice said on Tuesday that it had reached a “deferred prosecution agreement” with the three Americans, Ryan Adams, Marc Baier and Daniel Gericke. At least two of them are believed to have worked for the US National Security Agency before transferring their skills to the private sector.
 MICHELLE OBAMA HAD SOME of her personal emails intercepted by a group of American cyber-spies who were working for the government of the United Arab Emirates (UAE), according to a new book. The book, This Is How They Tell Me the World Ends, is written by Nicole Perlroth, who covers cybersecurity-related topics for The New York Times. It tackles what the author describes as the global “cyber-weapons arms race” and its impact on international security.
MICHELLE OBAMA HAD SOME of her personal emails intercepted by a group of American cyber-spies who were working for the government of the United Arab Emirates (UAE), according to a new book. The book, This Is How They Tell Me the World Ends, is written by Nicole Perlroth, who covers cybersecurity-related topics for The New York Times. It tackles what the author describes as the global “cyber-weapons arms race” and its impact on international security.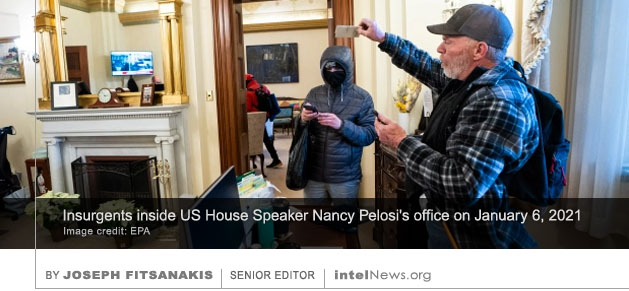 THE INSURGENTS WHO STORMED the United States Capitol Building Complex on January 6 may have unwittingly provided cover for teams of foreign spies, who could have stolen or compromised sensitive electronic equipment. This largely neglected security-related aspect of the attack is discussed in an
THE INSURGENTS WHO STORMED the United States Capitol Building Complex on January 6 may have unwittingly provided cover for teams of foreign spies, who could have stolen or compromised sensitive electronic equipment. This largely neglected security-related aspect of the attack is discussed in an  A large-scale cyberespionage attack targeting United States government computer systems, which some experts
A large-scale cyberespionage attack targeting United States government computer systems, which some experts  Cybersecurity researchers have uncovered what is believed to be the first-ever case of hackers using LinkedIn to infect the computers of targeted users with viruses, according to a new report. The hackers appear to have been sponsored by government and to have targeted employees of carefully selected military contractors in central Europe, according to sources.
Cybersecurity researchers have uncovered what is believed to be the first-ever case of hackers using LinkedIn to infect the computers of targeted users with viruses, according to a new report. The hackers appear to have been sponsored by government and to have targeted employees of carefully selected military contractors in central Europe, according to sources. Complacency and substandard security by the United States Central Intelligence Agency were behind the Vault 7 leak of 2017, which ranks as the greatest data loss in the agency’s history, according to an internal report. The Vault 7 data loss was particularly shocking, given that the CIA should have taken precautions following numerous leaks of classified government information in years prior to 2017, according to the report.
Complacency and substandard security by the United States Central Intelligence Agency were behind the Vault 7 leak of 2017, which ranks as the greatest data loss in the agency’s history, according to an internal report. The Vault 7 data loss was particularly shocking, given that the CIA should have taken precautions following numerous leaks of classified government information in years prior to 2017, according to the report. The United States Department of Defense has barred its employees from using Zoom, a popular video teleconferencing application, due to concerns that foreign spies may be using the software to collect intelligence. The Pentagon made the announcement less than a day after the US Senate advised its members to refrain from using Zoom. The video teleconferencing software is owned by Zoom Video Communications, Inc., a NASDAQ-trading software firm headquartered in Jan Jose, California. It has become popular in recent weeks, due to the increasing reliance on telework resulting from the effects of the COVID-19 pandemic.
The United States Department of Defense has barred its employees from using Zoom, a popular video teleconferencing application, due to concerns that foreign spies may be using the software to collect intelligence. The Pentagon made the announcement less than a day after the US Senate advised its members to refrain from using Zoom. The video teleconferencing software is owned by Zoom Video Communications, Inc., a NASDAQ-trading software firm headquartered in Jan Jose, California. It has become popular in recent weeks, due to the increasing reliance on telework resulting from the effects of the COVID-19 pandemic. A leading Chinese cybersecurity firm has accused the United States Central Intelligence Agency of using sophisticated malicious software to hack into computers belonging to the Chinese government and private sector for over a decade.
A leading Chinese cybersecurity firm has accused the United States Central Intelligence Agency of using sophisticated malicious software to hack into computers belonging to the Chinese government and private sector for over a decade. One of the United Nations’ most sensitive computer systems was targeted in a highly sophisticated cyber-espionage operation that appears to have been sponsored by a state, according to a leaked study. The study was leaked to the media earlier this week, and was reported by the Associated Press on Wednesday.
One of the United Nations’ most sensitive computer systems was targeted in a highly sophisticated cyber-espionage operation that appears to have been sponsored by a state, according to a leaked study. The study was leaked to the media earlier this week, and was reported by the Associated Press on Wednesday. The director of Australia’s main national security agency has warned in a public speech that the threat from espionage —including cyber espionage— is greater than terrorism, and poses an “existential” danger to established states. Duncan Lewis was appointed director of the Australian Security Intelligence Organisation (ASIO) in 2014, having already served for more than four decades in the Australian military and civilian government sectors. On Wednesday, Lewis gave a rare
The director of Australia’s main national security agency has warned in a public speech that the threat from espionage —including cyber espionage— is greater than terrorism, and poses an “existential” danger to established states. Duncan Lewis was appointed director of the Australian Security Intelligence Organisation (ASIO) in 2014, having already served for more than four decades in the Australian military and civilian government sectors. On Wednesday, Lewis gave a rare 






Russian hacker group using Internet service providers to spy on foreign embassies
August 2, 2025 by Joseph Fitsanakis 3 Comments
Turla began its attempt to compromise a host of Russian internet service providers in February, according to Microsoft’s report. The group’s apparent goal has been to gain access to the software that enables Russian security agencies to legally intercept internet traffic, following the issuance of warrants by judges. This software is governed by Russia’s System for Operative Investigative Activities (SORM), which became law in 1995, under the presidency of Boris Yeltsin. All local, state, and federal government agencies in Russia use the SORM system to facilitate court-authorized telecommunications surveillance.
According to Microsoft, targeted Internet users receive an error message prompting them to update their browser’s cryptographic certificate. Consent by the user results in the targeted computer downloading and installing a malware. Termed ApolloShadow by Microsoft, the malware is disguised as a security update from Kaspersky, Russia’s most widely known antivirus software provider. Once installed the malware gives the hackers access to the content of the targeted user’s secure communications.
The Microsoft report states that, although Turla has been involved in prior attacks against diplomatic targets in Russia and abroad, this is the first time that the hacker group has been confirmed to have the capability to attack its targets at the Internet Service Provider (ISP) level. In doing so, Turla has been able to incorporate Russia’s domestic telecommunications infrastructure into its attack tool-kit, the report states. The report does not name the diplomatic facilities or the countries whose diplomats have been targeted by Turla hackers. But it warns that all “diplomatic personnel using local [internet service providers] or telecommunications services in Russia are highly likely targets” of the group.
► Author: Joseph Fitsanakis | Date: 02 August 2025 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with ApolloShadow, computer hacking, cyberespionage, diplomatic security, Moscow, News, Russia, Secret Blizzard, Snake malware, SORM (Russia), System for Operative Investigative Activities (Russia), Turla