US considering drastic increase in intel-sharing with Saudi Arabia after drone attacks
September 17, 2019 1 Comment
 United States officials are considering increasing substantially America’s intelligence-sharing with Saudi Arabia following last weekend’s drone attacks that halved the Kingdom’s oil production and shook global markets. The attacks occurred in the early hours of Saturday, September 14, at two refineries located in eastern Saudi Arabia. The refineries are owned by Aramco, Saudi Arabia’s government-owned oil conglomerate, and are part of the world’s largest crude oil processing facility. The massive fires caused by the attacks were contained within hours and no casualties were reported. But the facilities had to cease operation so that repairs could be completed. This cut Saudi Arabia’s oil production by close to 50 percent, which amounted to a 5 percent reduction in global oil production. The impact on the world’s financial markets was immediate: by Monday morning, oil prices had seen their most significant one-day surge since the 1991 Gulf War.
United States officials are considering increasing substantially America’s intelligence-sharing with Saudi Arabia following last weekend’s drone attacks that halved the Kingdom’s oil production and shook global markets. The attacks occurred in the early hours of Saturday, September 14, at two refineries located in eastern Saudi Arabia. The refineries are owned by Aramco, Saudi Arabia’s government-owned oil conglomerate, and are part of the world’s largest crude oil processing facility. The massive fires caused by the attacks were contained within hours and no casualties were reported. But the facilities had to cease operation so that repairs could be completed. This cut Saudi Arabia’s oil production by close to 50 percent, which amounted to a 5 percent reduction in global oil production. The impact on the world’s financial markets was immediate: by Monday morning, oil prices had seen their most significant one-day surge since the 1991 Gulf War.
The Houthi movement, a collection of Yemeni Shiite militias supported by Iran, claimed responsibility for the attack. A Houthi movement spokesman said on Sunday that the attacks had been carried out with the use of modified commercially available drones. He also warned that Saudi Arabia would experience more attacks of this kind in the future. Iran has rejected accusations by American and some Saudi officials that it was responsible for the attacks.
On Monday the Reuters news agency reported that the US is considering the possibility of drastically increasing the volume and quality of intelligence it shares with Saudi Arabia. The move is allegedly intended as one in a series of measures to be taken by Washington in response to Saturday’s drone attacks. In the past, the US has been selective in how much intelligence it shares with the Saudis, who have been involved in an increasingly bloody civil war in Yemen since 2015. Washington is weary of being seen to have a decisive role in support of the Saudi-led military campaign in Yemen, in light of the criticism that the latter has drawn from numerous international bodies and governments around the world.
The US Congress has also condemned the Saudi campaign in an unusually bipartisan fashion, and has tried to stop President Donald Trump from providing material support to it. In May of this year, the US president defied Congress and signed two dozen arms sales agreements worth over $8 billion with the oil kingdom. The move upset many critics of Saudi Arabia in the Republican Party, who sharply criticized the Saudi government for killing journalist Jamal Khashoggi inside the Saudi consulate in Istanbul, Turkey, last year. A possible decision by Washington to increase its intelligence sharing with Saudi Arabia is bound to prompt a critical response from Congress, especially if it relates to the ongoing war in Yemen.
► Author: Joseph Fitsanakis | Date: 17 September 2019 | Permalink
 The Russian government reportedly fired a number of officials over the defection of a senior Kremlin aide, who alleged worked as an American spy. Meanwhile, Moscow has filed a search request with INTERPOL about the alleged defector’s whereabouts. News of the defection was
The Russian government reportedly fired a number of officials over the defection of a senior Kremlin aide, who alleged worked as an American spy. Meanwhile, Moscow has filed a search request with INTERPOL about the alleged defector’s whereabouts. News of the defection was  The intelligence services of Israel planted surveillance devices around the White House in an attempt to spy on United States President Donald Trump and his senior advisors, according to a report published on Thursday. The
The intelligence services of Israel planted surveillance devices around the White House in an attempt to spy on United States President Donald Trump and his senior advisors, according to a report published on Thursday. The 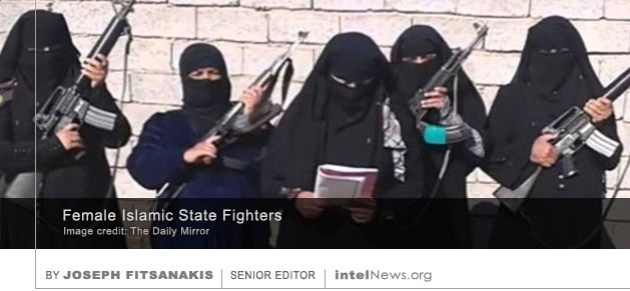 Tens of thousands of supporters of the Islamic State, many of them women and children, are re-radicalizing inside vast Kurdish-run prison camps with inadequate security and almost no infrastructure or provisions. In a
Tens of thousands of supporters of the Islamic State, many of them women and children, are re-radicalizing inside vast Kurdish-run prison camps with inadequate security and almost no infrastructure or provisions. In a 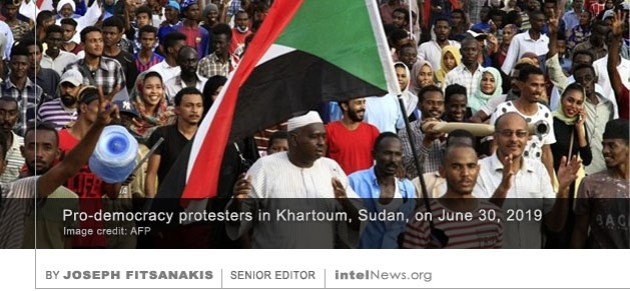 Facebook has shut down a well-funded online campaign to support Sudan’s military regime, which some say is part of wider efforts by Egypt, the United Arab Emirates and Saudi Arabia to stop democratic reforms in Sudan. The northeast African country has experienced civil unrest for more than a year. In February Sudan’s longtime strongman, Omar Hassan al-Bashir, fell from power after 30 years, following prolonged popular protests. But the new military junta that succeeded him launched a
Facebook has shut down a well-funded online campaign to support Sudan’s military regime, which some say is part of wider efforts by Egypt, the United Arab Emirates and Saudi Arabia to stop democratic reforms in Sudan. The northeast African country has experienced civil unrest for more than a year. In February Sudan’s longtime strongman, Omar Hassan al-Bashir, fell from power after 30 years, following prolonged popular protests. But the new military junta that succeeded him launched a  The United States Central Intelligence Agency has questioned the accuracy of a media report, which claimed that “repeated mishandling” of intelligence by President Donald Trump resulted in the exfiltration of a high-level source from Russia. According to the American news network CNN, the CIA carried out the exfiltration operation in 2017. Despite the success of the operation, the removal of the asset has left the US without this high-level source at a time when it is most needed, said CNN. The network
The United States Central Intelligence Agency has questioned the accuracy of a media report, which claimed that “repeated mishandling” of intelligence by President Donald Trump resulted in the exfiltration of a high-level source from Russia. According to the American news network CNN, the CIA carried out the exfiltration operation in 2017. Despite the success of the operation, the removal of the asset has left the US without this high-level source at a time when it is most needed, said CNN. The network  In an effort to remain relevant, al-Qaeda has shifted its strategic focus from Yemen to Syria but continues to pursue a globalist agenda by seeking ways to attack Western targets, according to an expert report. Following the meteoric rise of the Islamic State in 2014, al-Qaeda found it difficult to retain its title as the main representative of the worldwide Sunni insurgency. But in an
In an effort to remain relevant, al-Qaeda has shifted its strategic focus from Yemen to Syria but continues to pursue a globalist agenda by seeking ways to attack Western targets, according to an expert report. Following the meteoric rise of the Islamic State in 2014, al-Qaeda found it difficult to retain its title as the main representative of the worldwide Sunni insurgency. But in an  Italy has arrested a Russian business executive and former foreign ministry official who is wanted by the United States for carrying out espionage against an American aviation firm. Alexander Yuryevich Korshunov, 57, who is a former official in Russia’s Ministry of Foreign Affairs, was reportedly
Italy has arrested a Russian business executive and former foreign ministry official who is wanted by the United States for carrying out espionage against an American aviation firm. Alexander Yuryevich Korshunov, 57, who is a former official in Russia’s Ministry of Foreign Affairs, was reportedly 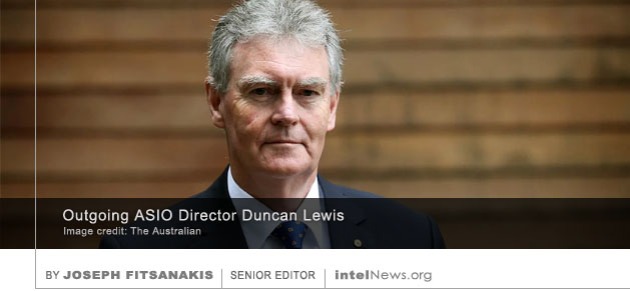 The director of Australia’s main national security agency has warned in a public speech that the threat from espionage —including cyber espionage— is greater than terrorism, and poses an “existential” danger to established states. Duncan Lewis was appointed director of the Australian Security Intelligence Organisation (ASIO) in 2014, having already served for more than four decades in the Australian military and civilian government sectors. On Wednesday, Lewis gave a rare
The director of Australia’s main national security agency has warned in a public speech that the threat from espionage —including cyber espionage— is greater than terrorism, and poses an “existential” danger to established states. Duncan Lewis was appointed director of the Australian Security Intelligence Organisation (ASIO) in 2014, having already served for more than four decades in the Australian military and civilian government sectors. On Wednesday, Lewis gave a rare  An Iranian engineer who was recruited by Dutch intelligence helped the United States and Israel infect computers used in Iran’s nuclear program with the Stuxnet cyber weapon, according to a new report.
An Iranian engineer who was recruited by Dutch intelligence helped the United States and Israel infect computers used in Iran’s nuclear program with the Stuxnet cyber weapon, according to a new report.  A Russian-backed development bank, which is
A Russian-backed development bank, which is 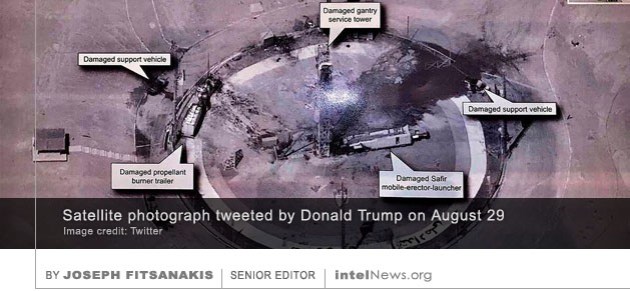 A tweet by United States President Donald Trump may have compromised secrets about America’s reconnaissance satellite capabilities, according to experts who analyzed it over the weekend. The American president posted a message about Iran’s space program on his personal Twitter account on Saturday, August 30. The message read: “The United States of America was not involved in the catastrophic accident during final launch preparations for the Safir SLV Launch at Semnan Launch Site One in Iran. I wish Iran best wishes and good luck in determining what happened at Site One”.
A tweet by United States President Donald Trump may have compromised secrets about America’s reconnaissance satellite capabilities, according to experts who analyzed it over the weekend. The American president posted a message about Iran’s space program on his personal Twitter account on Saturday, August 30. The message read: “The United States of America was not involved in the catastrophic accident during final launch preparations for the Safir SLV Launch at Semnan Launch Site One in Iran. I wish Iran best wishes and good luck in determining what happened at Site One”. The Islamic Revolutionary Guard Corps (IRGC) is still recovering from the damage it suffered by an offensive American cyber campaign against it that took place in June, according to sources. The attack allegedly degraded the IRGC’s ability to strike at oil tankers and other ships in the Persian Gulf. The New York Times
The Islamic Revolutionary Guard Corps (IRGC) is still recovering from the damage it suffered by an offensive American cyber campaign against it that took place in June, according to sources. The attack allegedly degraded the IRGC’s ability to strike at oil tankers and other ships in the Persian Gulf. The New York Times  In a move observers describe as unprecedented, a United States government regulator is preparing to recommend blocking the construction of an 8,000-mile long undersea cable linking America with China, allegedly due to national security concerns. Washington has never before halted the construction of undersea cables, which form the global backbone of the Internet by facilitating nearly 100% of Internet traffic. Much of the undersea cable network is in the process of being replaced by modern optical cables that can facilitate faster Internet-based communications than ever before.
In a move observers describe as unprecedented, a United States government regulator is preparing to recommend blocking the construction of an 8,000-mile long undersea cable linking America with China, allegedly due to national security concerns. Washington has never before halted the construction of undersea cables, which form the global backbone of the Internet by facilitating nearly 100% of Internet traffic. Much of the undersea cable network is in the process of being replaced by modern optical cables that can facilitate faster Internet-based communications than ever before.






Gas explosion reported at Russian research facility that houses Ebola and smallpox
September 18, 2019 by Ian Allen Leave a comment
Vector was founded in 1974 by the Soviet state to study mass infectious agents that could be used to build biological weapons. Today it remains as one of the world’s largest virology research centers, specializing in the treatment of some of the most lethal infectious diseases, such as Ebola, tularemia and swine flu. The Vector facility is believed to be one of two locations in the world that house live samples of the smallpox virus. The Centers for Disease Control and Prevention in the United States city of Atlanta is also believed to house samples of the virus.
According to a statement issued on Tuesday by the Russian state-owned news agency TASS, the Vector facility sustained an explosion on Monday afternoon local time. The explosion was reportedly caused by a gas canister used by workers who were carrying out repairs at a sanitary inspection room located on the fifth floor of the Vector facility. An employee suffered unspecified injuries as a result of the explosion, according to the statement. However, “no work with biological agents was being carried out in the [Vector] building” at the time of the explosion, so there was no need for a state of emergency, according to the statement. Russian media reported on Tuesday that Vector personnel were present on the site and that no biological threat alerts had been issued.
► Author: Ian Allen | Date: 18 September 2019 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with biomedical intelligence, biosecurity, Kotsovo (Russia), News, Novosibirsk, Russia, State Research Center of Virology and Biotechnology (Russia), Vector (Russia)