Egyptian branch of ISIS declares war on Hamas as tensions rise in Sinai
January 12, 2018 1 Comment
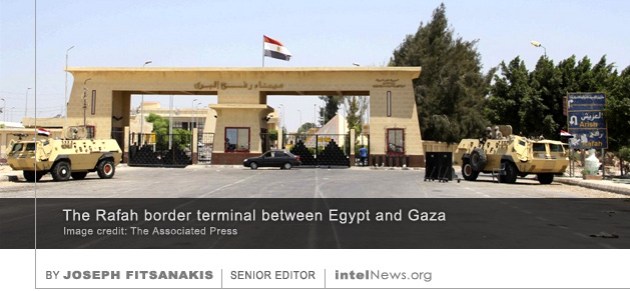 The Islamic State in Egypt’s Sinai Province has declared war on the Palestinian militant group Hamas, in a move that experts say will furhter-complicate an already volatile security situation in eastern Egypt. Many observers see the group, Wilayat Sinai, as the strongest international arm of the Islamic State of Iraq and Syria (ISIS). Known officially as ISIS – Sinai Province, Wilayat Sinai was behind the 2015 downing of Metrojet Flight 9268, which killed all 224 passengers and crew onboard, most of them Russians. The same group killed 311 people at a Sufi mosque in November of last year, in what has become known as the worst terrorist attack in Egypt’s modern history.
The Islamic State in Egypt’s Sinai Province has declared war on the Palestinian militant group Hamas, in a move that experts say will furhter-complicate an already volatile security situation in eastern Egypt. Many observers see the group, Wilayat Sinai, as the strongest international arm of the Islamic State of Iraq and Syria (ISIS). Known officially as ISIS – Sinai Province, Wilayat Sinai was behind the 2015 downing of Metrojet Flight 9268, which killed all 224 passengers and crew onboard, most of them Russians. The same group killed 311 people at a Sufi mosque in November of last year, in what has become known as the worst terrorist attack in Egypt’s modern history.
Israeli sources claim that, in the past, Wilayat Sinai has had limited cooperation with Hamas, the militant group that controls the Gaza Strip, a coastal section of the Palestinian territories that borders with Egypt’s Sinai Province. The two organizations are believed to have engaged in limited cross-border arms-smuggling, while some injured Wilayat Sinai fighters have been treated in Gaza Strip hospitals. But the two groups have major ideological differences that contribute to their increasingly tense relationship. The Islamic State objects to participation in democratic elections, which it sees as efforts to place human will above divine law. It has thus condemned Hamas’ decision to participate in the 2006 elections in the Palestinian territories. Additionally, even though it promotes Sunni Islam, Hamas is far less strict in its religious approach than the Islamic State, and does not impose Sharia (Islamic law based on the Quran) in the territory it controls. Furthermore, Hamas suppresses Saudi-inspired Wahhabism and its security forces often arrest ISIS and al-Qaeda sympathizers in the Gaza Strip. In the past month, ISIS accused Hamas of having failed to prevent America’s formal recognition of Jerusalem as the capital of Israel. Additionally, ISIS is opposed to the support that Hamas receives from Iran, a Shiite nation that ISIS regards as heretical.
There are reports that Hamas has been quietly collaborating with Egypt and even Israel in recent months, in order to combat the rise of ISIS in the region. For several months now, the Palestinian group has exercised stricter control over its seven-mile-long border with Egypt. It has rebuilt border barriers that had previously been destroyed and has installed security fences and a digital surveillance system. It has also launched a public-relations effort to shame the families of young men from Gaza who have joined ISIS forces in Sinai. In response to these moves, Wilayat Sinai has publicly urged its supporters to kill members of Hamas and attack the group’s security installations and public buildings. The ISIS-affiliated group has also urged its members to eliminate members of the small Shiite Muslim community in the Gaza strip. According to experts, the decision by Wilayat Sinai to declare war on Hamas means that the group has now virtually surrounded itself with adversaries. The move may also increase informal collaboration between Hamas and the Israeli government, say observers.
► Author: Joseph Fitsanakis | Date: 12 January 2018 | Permalink
 Pakistan said on Tuesday that it had suspended military and intelligence cooperation with the United States in the wake of Washington’s decision to stop security assistance to Pakistan. On Tuesday, Pakistan’s Minister of Defense, Khurram Dastgir Khan, said that his country had terminated all cooperation with the US in the areas of defense and intelligence. He said that the move was a response to the announcement by US President Donald Trump last week that Washington would stop providing security assistance to Pakistan. American officials stated that the change in policy took place because Pakistan had allegedly deceived America in the global war on terrorism. On Thursday last week, the President Trump
Pakistan said on Tuesday that it had suspended military and intelligence cooperation with the United States in the wake of Washington’s decision to stop security assistance to Pakistan. On Tuesday, Pakistan’s Minister of Defense, Khurram Dastgir Khan, said that his country had terminated all cooperation with the US in the areas of defense and intelligence. He said that the move was a response to the announcement by US President Donald Trump last week that Washington would stop providing security assistance to Pakistan. American officials stated that the change in policy took place because Pakistan had allegedly deceived America in the global war on terrorism. On Thursday last week, the President Trump  A man who attended the “Unite the Right” rally in Charlottesville, Virginia, with members of a neo-Nazi organization, has been charged with terrorism offences after he tried to derail a passenger train. Taylor M. Wilson, of St. Charles, Missouri, was arrested by federal law enforcement officials on October 22, after he
A man who attended the “Unite the Right” rally in Charlottesville, Virginia, with members of a neo-Nazi organization, has been charged with terrorism offences after he tried to derail a passenger train. Taylor M. Wilson, of St. Charles, Missouri, was arrested by federal law enforcement officials on October 22, after he  South Korea’s disgraced former president, Park Geun-hye, has been charged with accepting bribes amounting to millions of dollars from the country’s spy agency, according to reports. Park made history in 2013, by becoming the first woman president in South Korean history. However, almost as soon as she assumed office, her administration became embroiled in successive corruption scandals. By 2016, Park’s presidency had been brought to a standstill due to mass protests urging her removal from power, while increasing numbers of officials and administrators were refusing to work with her. She was eventually impeached in 2017, after the Constitutional Court of Korea found that she had violated the country’s laws by promoting the interests of personal friends and private corporations in return for cash and favors. She is currently in custody awaiting trial for 18 different charges, including abuse of power, coercion, blackmail and bribery.
South Korea’s disgraced former president, Park Geun-hye, has been charged with accepting bribes amounting to millions of dollars from the country’s spy agency, according to reports. Park made history in 2013, by becoming the first woman president in South Korean history. However, almost as soon as she assumed office, her administration became embroiled in successive corruption scandals. By 2016, Park’s presidency had been brought to a standstill due to mass protests urging her removal from power, while increasing numbers of officials and administrators were refusing to work with her. She was eventually impeached in 2017, after the Constitutional Court of Korea found that she had violated the country’s laws by promoting the interests of personal friends and private corporations in return for cash and favors. She is currently in custody awaiting trial for 18 different charges, including abuse of power, coercion, blackmail and bribery.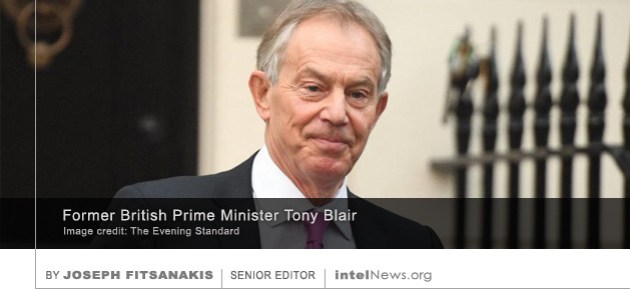 A spokesman for Tony Blair has dismissed as “categorically absurd” allegations that the former British Prime Minister warned the White House that President Donald Trump was targeted by British spy agencies. The claims are made in the book Fire and Fury: Inside the Trump White House, which is due to be published next week. Its author, Michael Wolf, says he based the information in the book on more than 200 interviews that he held with President Trump and members of his inner circle during the past year.
A spokesman for Tony Blair has dismissed as “categorically absurd” allegations that the former British Prime Minister warned the White House that President Donald Trump was targeted by British spy agencies. The claims are made in the book Fire and Fury: Inside the Trump White House, which is due to be published next week. Its author, Michael Wolf, says he based the information in the book on more than 200 interviews that he held with President Trump and members of his inner circle during the past year. Since 2008, when we launched intelNews, it has been our
Since 2008, when we launched intelNews, it has been our  04. Unprecedented security changes are taking place in Saudi Arabia. Analysts agree that the Kingdom of Saudi Arabia is undergoing its most important political changes in generations. On November 4, 2017, nearly 50 senior Saudi officials, including at least 11 princes, some of them among the world’s wealthiest people, were suddenly
04. Unprecedented security changes are taking place in Saudi Arabia. Analysts agree that the Kingdom of Saudi Arabia is undergoing its most important political changes in generations. On November 4, 2017, nearly 50 senior Saudi officials, including at least 11 princes, some of them among the world’s wealthiest people, were suddenly  taking place in the intelligence infrastructure of South Korea, which are arguably as important as developments north of the 38th parallel. In June, the new center-left government of President Moon Jae-in
taking place in the intelligence infrastructure of South Korea, which are arguably as important as developments north of the 38th parallel. In June, the new center-left government of President Moon Jae-in  assist policy-makers, including the president. So when the CIA and the FBI conclude that the Russian government launched an extensive and sophisticated campaign to undermine the 2016 US presidential election, one expects the president to take that advisement under serious consideration. However, the US leader has openly dismissed the conclusions of his own Intelligence Community and has
assist policy-makers, including the president. So when the CIA and the FBI conclude that the Russian government launched an extensive and sophisticated campaign to undermine the 2016 US presidential election, one expects the president to take that advisement under serious consideration. However, the US leader has openly dismissed the conclusions of his own Intelligence Community and has  Since 2008, when we launched intelNews, it has been our
Since 2008, when we launched intelNews, it has been our  as a result of “acute poisoning from an undefined substance”, according to his doctors. Also in February, Kim Jong-nam, half-brother of North Korean Supreme Leader Kim Jong-un, was killed in an
as a result of “acute poisoning from an undefined substance”, according to his doctors. Also in February, Kim Jong-nam, half-brother of North Korean Supreme Leader Kim Jong-un, was killed in an  support for the rebels could backfire by causing the suddenly unemployed fighters to join jihadist organizations. In August, there were reports that US troops
support for the rebels could backfire by causing the suddenly unemployed fighters to join jihadist organizations. In August, there were reports that US troops  Since 2008, when we launched intelNews, it has been our
Since 2008, when we launched intelNews, it has been our  10.
10.  the alleged device may have been deployed by an intelligence service of a third country —possibly Russia— without the knowledge of the Cuban authorities. In October, the White House expelled 15 Cuban diplomats from the US in response to the incident. But the question of what harmed the health of at least 20 employees at the US embassy in Havana remains largely unanswered.
the alleged device may have been deployed by an intelligence service of a third country —possibly Russia— without the knowledge of the Cuban authorities. In October, the White House expelled 15 Cuban diplomats from the US in response to the incident. But the question of what harmed the health of at least 20 employees at the US embassy in Havana remains largely unanswered. A North Korean nuclear scientist who defected to China but was involuntarily sent back to North Korea in November reportedly killed himself in his North Korean cell hours before he was due to be interrogated. Information about the scientist’s alleged suicide was issued on Thursday by Radio Free Asia (RFA), a multilingual news service based in Washington, DC, which is funded by the United States government. The service said its reporters spoke to an anonymous source in North Hamgyong province, North Korea’s northernmost region that borders China. The source identified the late scientist as Hyun Cheol Huh, but cautioned that this may not be his real name, because the North Korean security services are known to “use […] fake names when referring to important persons” in their custody.
A North Korean nuclear scientist who defected to China but was involuntarily sent back to North Korea in November reportedly killed himself in his North Korean cell hours before he was due to be interrogated. Information about the scientist’s alleged suicide was issued on Thursday by Radio Free Asia (RFA), a multilingual news service based in Washington, DC, which is funded by the United States government. The service said its reporters spoke to an anonymous source in North Hamgyong province, North Korea’s northernmost region that borders China. The source identified the late scientist as Hyun Cheol Huh, but cautioned that this may not be his real name, because the North Korean security services are known to “use […] fake names when referring to important persons” in their custody. The Government Communications Headquarters (GCHQ), one of Britain’s most powerful intelligence agencies, says it plans to accelerate its vetting process because it is losing top recruits to the private sector. Founded in 1919 and headquartered in Cheltenham, England, the GCHQ is tasked with communications interception. It also provides information assurance to both civilian and military components of the British state. It primarily hires people with technical expertise in communications hardware and software. But in the past fiscal year, the agency fell notably short of its recruitment target, according to a new government report published this week.
The Government Communications Headquarters (GCHQ), one of Britain’s most powerful intelligence agencies, says it plans to accelerate its vetting process because it is losing top recruits to the private sector. Founded in 1919 and headquartered in Cheltenham, England, the GCHQ is tasked with communications interception. It also provides information assurance to both civilian and military components of the British state. It primarily hires people with technical expertise in communications hardware and software. But in the past fiscal year, the agency fell notably short of its recruitment target, according to a new government report published this week.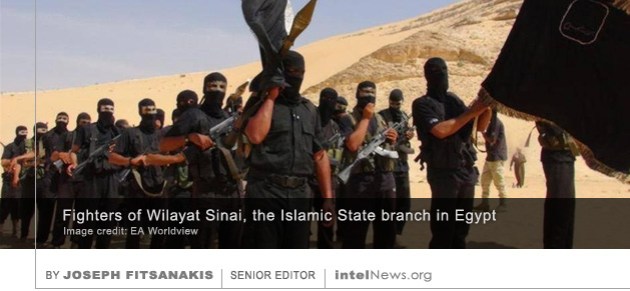 Through a series of meticulously planned terrorist strikes and assassinations, Wilayat Sinai has emerged as the strongest international arm of the Islamic State of Iraq and Syria (ISIS), according to some experts. Known officially as ISIS – Sinai Province, Wilayat Sinai claimed responsibility for the October 2015 downing of Metrojet Flight 9268. All 224 passengers and crew, most of them Russians, died when the plane blew up in midair over Egypt’s Sinai Peninsula. The incident marked the worst aviation disaster in Russian history. The same group, Wilayat Sinai, was behind last month’s attack on the Al Rawda Sufi mosque in bir al-Abed, Egypt. The massacre resulted in the deaths of 311 people, making it the worst terrorist attack in the history of modern Egypt.
Through a series of meticulously planned terrorist strikes and assassinations, Wilayat Sinai has emerged as the strongest international arm of the Islamic State of Iraq and Syria (ISIS), according to some experts. Known officially as ISIS – Sinai Province, Wilayat Sinai claimed responsibility for the October 2015 downing of Metrojet Flight 9268. All 224 passengers and crew, most of them Russians, died when the plane blew up in midair over Egypt’s Sinai Peninsula. The incident marked the worst aviation disaster in Russian history. The same group, Wilayat Sinai, was behind last month’s attack on the Al Rawda Sufi mosque in bir al-Abed, Egypt. The massacre resulted in the deaths of 311 people, making it the worst terrorist attack in the history of modern Egypt. The Russian hacker group that targeted the United States presidential election in 2016 also attacked hundreds of reporters around the world, most of them Americans, an Associated Press investigation shows. The group is often referred to in cyber security circles as Fancy Bear, but is also known as Pawn Storm, Sednit, APT28, Sofacy, and STRONTIUM. It has been linked to a long-lasting series or coordinated attacks against at least 150 senior figures in the US Democratic Party. The attacks occurred in the run-up to last year’s presidential elections in the US, which resulted in a victory for Donald Trump. The hacker group’s targets included Democratic Party presidential candidate Hillary Clinton and her campaign chairman John Podesta. But its hackers also went after senior US diplomatic and intelligence officials, as well as foreign officials in countries like Canada and the Ukraine.
The Russian hacker group that targeted the United States presidential election in 2016 also attacked hundreds of reporters around the world, most of them Americans, an Associated Press investigation shows. The group is often referred to in cyber security circles as Fancy Bear, but is also known as Pawn Storm, Sednit, APT28, Sofacy, and STRONTIUM. It has been linked to a long-lasting series or coordinated attacks against at least 150 senior figures in the US Democratic Party. The attacks occurred in the run-up to last year’s presidential elections in the US, which resulted in a victory for Donald Trump. The hacker group’s targets included Democratic Party presidential candidate Hillary Clinton and her campaign chairman John Podesta. But its hackers also went after senior US diplomatic and intelligence officials, as well as foreign officials in countries like Canada and the Ukraine. Dozens of Western former spies, most of them Americans, are being hired by the United Arab Emirates, whose ruling family is trying to create a new spy service modeled after the United States Central Intelligence Agency.
Dozens of Western former spies, most of them Americans, are being hired by the United Arab Emirates, whose ruling family is trying to create a new spy service modeled after the United States Central Intelligence Agency.  Ukraine’s counterintelligence agency has arrested the principal translator of the country’s prime minister, accusing him of spying for Russia. The translator has been identified as Stanislav Yezhov, who has served as a translator for two consecutive Ukrainian prime ministers. As part of his job, Yezhov has been present at nearly all high-level meetings between Ukraine’s Prime Minister, Volodymyr Groysman, and foreign leaders since 2016, when Groysman assumed his executive post. In the last year alone, Yezhov accompanied the Ukrainian prime minister during official trips to Washington, London and Berlin. Before translating for Groysman, Yezhov is thought to have served as an interpreter for Viktor Yanukovych, Ukraine’s former President. Yanukovych, a pro-Russian politician, occupied that office from 2010 until his ousting from power in 2014, as a result of the 2014 Ukrainian revolution.
Ukraine’s counterintelligence agency has arrested the principal translator of the country’s prime minister, accusing him of spying for Russia. The translator has been identified as Stanislav Yezhov, who has served as a translator for two consecutive Ukrainian prime ministers. As part of his job, Yezhov has been present at nearly all high-level meetings between Ukraine’s Prime Minister, Volodymyr Groysman, and foreign leaders since 2016, when Groysman assumed his executive post. In the last year alone, Yezhov accompanied the Ukrainian prime minister during official trips to Washington, London and Berlin. Before translating for Groysman, Yezhov is thought to have served as an interpreter for Viktor Yanukovych, Ukraine’s former President. Yanukovych, a pro-Russian politician, occupied that office from 2010 until his ousting from power in 2014, as a result of the 2014 Ukrainian revolution.






Russian-trained Serb separatists are forming paramilitary group in Bosnia
January 15, 2018 by Joseph Fitsanakis 1 Comment
The rally was held despite an earlier decision by the Constitutional Court of Bosnia and Herzegovina, which ruled that military-style marches by separatist organizations were unconstitutional. According to Žurnal, the rally was organized by Srbska čast (Serbian Honor), a militia made up of hardline Serb separatists. The group strongly supports Milorad Dodik, a Serb nationalist who has served as president of Republika Srpska since 2010. The investigative news site said that several members of Srbska čast’s were trained by Russian paramilitary instructors in the Russian-Serbian Humanitarian Center, a Russian-funded disaster relief center based in southern Serbia, which Western officials claim is really an intelligence base. Žurnal also said that one of Srbska čast’s leading figures, Bojan Stojković, a former commando, was trained in military schools in Russia and has been decorated by the Russian military.
Friday’s report by the investigative news outlet quoted extensively from a leaked report by Bosnia and Herzegovnia’s intelligence agency. The report allegedly states that Srbska čast leaders, including Stojković, met secretly with Dodik and discussed the formation of a new, heavily armed paramilitary unit, which will operate as an extrajudicial force in support of Dodik’s administration in Republika Srpska. One quote from the document said that the paramilitary force would engage in “possible intervention if the opposition [i.e. those opposed to Dodik] seeks to obstruct the functioning of the authorities” in the Republika Srpska. Bosnia and Herzegovina has been seeking to join the North Atlantic Treaty Organization since 2006. The country has gone through a series of stages in negotiations with NATO and ratified a membership action plan in 2010. Bosnia’s application is heavily supported by Turkey, NATO’s only predominantly Muslim member state, but is fiercely opposed by Russia and by the Balkan country’s Serb minority.
► Author: Joseph Fitsanakis | Date: 15 January 2018 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with Banja Luka (Bosnia), Bojan Stojković, Bosnia and Herzegovina, Bosnian Serbs, Dragan Mektić, Milorad Dodik, NATO, News, Russia, Russian-Serbian Humanitarian Center, separatism, Serbian Honor