German government to hire 600 new officers to help monitor far-right activity
December 18, 2019 Leave a comment
 The German government has announced plans to hire hundreds of new police and intelligence officers, in order to step up its monitoring of violent far-right groups in the country. The announcement came at a press conference hosted on Tuesday in Berlin by Horst Seehofer, Germany’s Interior Minister.
The German government has announced plans to hire hundreds of new police and intelligence officers, in order to step up its monitoring of violent far-right groups in the country. The announcement came at a press conference hosted on Tuesday in Berlin by Horst Seehofer, Germany’s Interior Minister.
Seehofer told reporters that the Federal Office for the Protection of the Constitution —BfV, Germany’s domestic intelligence and counterterrorism agency— would hire 300 new officers whose job will be to focus on domestic far-right extremism. The German Federal Criminal Police Office will hire an additional 300 offers for the same purpose, added Seehofer. With these additional 600 officers, federal authorities will be able to increase their monitoring of far-right political groups, football fan clubs, far-right websites, and other hubs of far-right activity, said the minister.
German authorities estimate that there are 12,000 committed far-right extremists in the country who are willing and able to carry out violent attacks inside Germany or abroad. However, nearly 50 percent of actual attacks by adherents of far-right ideologies that have taken place in Germany in recent years have been carried out by individuals who were not on the radar of the police and intelligence services.
In addition to hiring 300 new intelligence officers, the BfV will set up a new “Central Office for Far Right Extremism in Public Service”, whose task will be to uncover adherents of far-right ideologies working in government agencies. The new office will concentrate its investigations on the police, the military and other government bodies.
During his press conference on Tuesday, Minister Seehofer stressed that the intensification of investigations into far-right terrorism would not happen at the expense of probing political violence from the far left and Islamist extremists.
► Author: Joseph Fitsanakis | Date: 18 December 2019 | Permalink
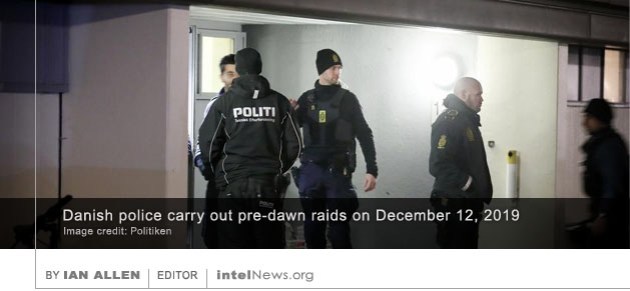 Last Thursday Danish authorities arrested 22 terrorism suspects in early morning raids across the country. Reports from Israel suggest that the raids were carried out following a tip from Israeli intelligence. The 22 suspects include men and women. Danish police said they were involved in the final stages of a plot to carry out attacks “in Denmark or abroad”, but have provided no specific information, except to say that the attacks were “thwarted” while they were well underway.
Last Thursday Danish authorities arrested 22 terrorism suspects in early morning raids across the country. Reports from Israel suggest that the raids were carried out following a tip from Israeli intelligence. The 22 suspects include men and women. Danish police said they were involved in the final stages of a plot to carry out attacks “in Denmark or abroad”, but have provided no specific information, except to say that the attacks were “thwarted” while they were well underway. The United States quietly expelled two Chinese diplomats in October of this year, a move that neither Washington nor Beijing chose to make public, according to a report published on Sunday. If true, the incident would signify the first known expulsions of Chinese diplomatic personnel from the US since 1987.
The United States quietly expelled two Chinese diplomats in October of this year, a move that neither Washington nor Beijing chose to make public, according to a report published on Sunday. If true, the incident would signify the first known expulsions of Chinese diplomatic personnel from the US since 1987.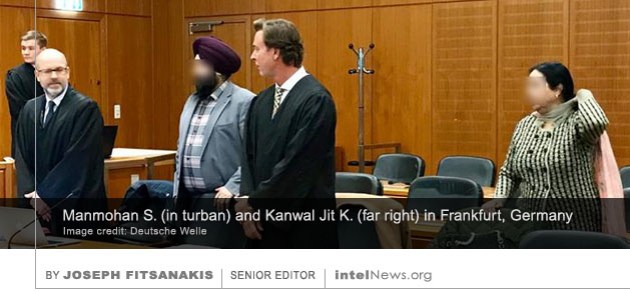 A court in Frankfurt has found a married couple guilty of spying in Germany on behalf of India’s external intelligence service. Due to Germany’s strict privacy laws, the couple have been identified only as 50-year-old Manmohan S. and his wife, Kanwal Jit K., who is 51.
A court in Frankfurt has found a married couple guilty of spying in Germany on behalf of India’s external intelligence service. Due to Germany’s strict privacy laws, the couple have been identified only as 50-year-old Manmohan S. and his wife, Kanwal Jit K., who is 51. One of Belgium’s leading universities has decided to shut down a research institute funded by the Chinese government, after the Belgian intelligence service accused its director of spying on behalf of Beijing. The news was
One of Belgium’s leading universities has decided to shut down a research institute funded by the Chinese government, after the Belgian intelligence service accused its director of spying on behalf of Beijing. The news was  Victor Ivanovich Sheymov, who is often referred to as one of the most important intelligence defectors of the Cold War, has reportedly died in the American state of Virginia. He was one of the most senior officials in the Soviet Union’s Committee for State Security (KGB) to ever defect to the West, and revealed important KGB secrets to the United States.
Victor Ivanovich Sheymov, who is often referred to as one of the most important intelligence defectors of the Cold War, has reportedly died in the American state of Virginia. He was one of the most senior officials in the Soviet Union’s Committee for State Security (KGB) to ever defect to the West, and revealed important KGB secrets to the United States. An unprecedented closed-door trial of a man identified only as “Witness J”, who was convicted earlier this year of a crime that cannot be revealed, has raised questions about the relationship between security and the law in Australia. The man, who is also known as “Prisoner 123458”, was sentenced to a jail sentence in February of this year. His sentencing came following a closed-door hearing, which was
An unprecedented closed-door trial of a man identified only as “Witness J”, who was convicted earlier this year of a crime that cannot be revealed, has raised questions about the relationship between security and the law in Australia. The man, who is also known as “Prisoner 123458”, was sentenced to a jail sentence in February of this year. His sentencing came following a closed-door hearing, which was  A court in Estonia has ordered the release of a former senior defense official who spied on the North Atlantic Treaty Organization for Russia, causing what experts
A court in Estonia has ordered the release of a former senior defense official who spied on the North Atlantic Treaty Organization for Russia, causing what experts  An elite group Russian military intelligence officers, who have participated in assassinations across Europe, have been using resorts in the French Alps as logistical and supply bases, according to a new report. The report concerns Unit 29155 of the Main Directorate of the General Staff of the Russian Armed Forces, commonly known as GRU.
An elite group Russian military intelligence officers, who have participated in assassinations across Europe, have been using resorts in the French Alps as logistical and supply bases, according to a new report. The report concerns Unit 29155 of the Main Directorate of the General Staff of the Russian Armed Forces, commonly known as GRU.  Switzerland has filed a formal complaint after an employee of the Swiss embassy in Sri Lanka was allegedly abducted by men who forced her to divulge sensitive information about the embassy and its activities. The Swiss Ministry of Foreign Affairs
Switzerland has filed a formal complaint after an employee of the Swiss embassy in Sri Lanka was allegedly abducted by men who forced her to divulge sensitive information about the embassy and its activities. The Swiss Ministry of Foreign Affairs  The United States Federal Bureau of Investigation says it is examining possible counterintelligence threats in connection with the popular online application FaceApp, which is headquartered in Russia. The application first made its appearance in January of 2017 and quickly became popular among smartphone users around the world. It allows users to upload a photograph of their face and then edit it with the help of artificial-intelligence software. The software can change the user’s photograph to make it look younger or older, or make it look as if it is from the opposite gender. The result can be impressively realistic and life-like.
The United States Federal Bureau of Investigation says it is examining possible counterintelligence threats in connection with the popular online application FaceApp, which is headquartered in Russia. The application first made its appearance in January of 2017 and quickly became popular among smartphone users around the world. It allows users to upload a photograph of their face and then edit it with the help of artificial-intelligence software. The software can change the user’s photograph to make it look younger or older, or make it look as if it is from the opposite gender. The result can be impressively realistic and life-like. The European multinational aerospace corporation Airbus has fired 16 of its employees for illegally possessing classified documents belonging to the German military. The Netherlands-registered aviation company, one of the world’s largest, has been cooperating with an investigation into the incident. The probe has been led by German authorities since September of 2018.
The European multinational aerospace corporation Airbus has fired 16 of its employees for illegally possessing classified documents belonging to the German military. The Netherlands-registered aviation company, one of the world’s largest, has been cooperating with an investigation into the incident. The probe has been led by German authorities since September of 2018.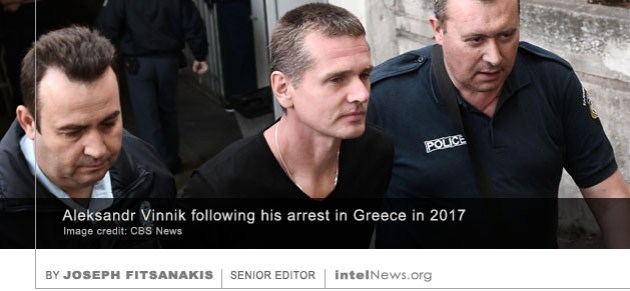 An intense fight between the United States and Russia over the extradition of a Russian cryptocurrency tycoon being held in Greece, is raising questions about the possible use of cryptocurrencies by spies. The tycoon in question is Aleksandr Vinnik, 39, who in 2011 co-founded BTC-e, an international cryptocurrency-trading platform. BTC-e allowed users to buy or sell several popular cryptocurrencies, including bitcoin and litecoin, using Russian rubles, United States dollars, or European Union euro currencies. Although headquartered in Russia, BTC-e’s servers were located in Bulgaria, while its operations were conducted through its offshore components in Cyprus and the Seychelles.
An intense fight between the United States and Russia over the extradition of a Russian cryptocurrency tycoon being held in Greece, is raising questions about the possible use of cryptocurrencies by spies. The tycoon in question is Aleksandr Vinnik, 39, who in 2011 co-founded BTC-e, an international cryptocurrency-trading platform. BTC-e allowed users to buy or sell several popular cryptocurrencies, including bitcoin and litecoin, using Russian rubles, United States dollars, or European Union euro currencies. Although headquartered in Russia, BTC-e’s servers were located in Bulgaria, while its operations were conducted through its offshore components in Cyprus and the Seychelles. As the Australian government has launched an official investigation into the claims made by a self-styled Chinese intelligence defector, some skeptics have begun to cast doubts about his revelations. The claims of Wang “William” Liqiang have dominated news headlines in Australia for over a week. The 26-year-old from China’s eastern Fujian province reportedly defected to Australia in October, while visiting his wife and newborn son in Sydney. He is currently reported to be in a safe house belonging to the Australian Security Intelligence Organization (ASIO).
As the Australian government has launched an official investigation into the claims made by a self-styled Chinese intelligence defector, some skeptics have begun to cast doubts about his revelations. The claims of Wang “William” Liqiang have dominated news headlines in Australia for over a week. The 26-year-old from China’s eastern Fujian province reportedly defected to Australia in October, while visiting his wife and newborn son in Sydney. He is currently reported to be in a safe house belonging to the Australian Security Intelligence Organization (ASIO).






Allegations of espionage rock Credit Suisse, as more employees come forward
December 19, 2019 by Joseph Fitsanakis 1 Comment
In October of this year, two senior Credit Suisse executives resigned amidst a high-stakes espionage scandal, which may have prompted a suicide. The alleged target of the espionage was Iqbal Khan, the former Chief Executive Officer (CEO) of Credit Suisse’s wealth-management division. Khan alleged that he was spied on by private investigators, paid for by Credit Suisse, after leaving the firm. One of the private investigators involved in the case, described as “an external security expert” who mediated between Credit Suisse and the investigation firm, committed suicide.
At the time, Credit Suisse described the surveillance on Khan as “strictly an isolated incident”. However, on December 11, The Wall Street Journal published allegations by another Credit Suisse executive, Colleen Graham, who said that she had been spied on after leaving her job at the firm. She alleged that she underwent three days of intensive surveillance by persons unknown in July of 2017. Credit Suisse was dismissive of Graham’s claims, saying that they were baseless.
But on Wednesday the firm announced the launching of a new probe after a third employee, who used to work directly under Credit Suisse Chief Executive Officer Tidjane Thiam, alleged that he too had been spied on. The allegations were made by Peter Goerke, and were the subject of a headline article by the respected Swiss daily Neue Zürcher Zeitung. The article was accompanied by documents and photographs submitted by Goerke, which are said to support his claims.
There are now concerns that spying on former and current employees may have been a standard operating procedure at Credit Suisse. In an article published on Wednesday, The Wall Street Journal said that the alleged incidents “highlight the ethical and reputational pitfalls companies encounter when they physically monitor employees”.
► Author: Joseph Fitsanakis | Date: 19 December 2019 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with banking sector, Colleen Graham, corporate espionage, Credit Suisse, Investigo, News, Peter Goerke, Switzerland