Ukraine, Russia, spied on Dutch investigators of MH17 plane disaster, TV report claims
June 28, 2018 1 Comment
 Dozens of Dutch security officers, legal experts, diplomats and other civil servants were systematically spied on by Ukrainian and Russian intelligence services while probing the aftermath of the MH17 disaster, according to a report on Dutch television. Malaysia Airlines Flight 17, a scheduled passenger flight from Amsterdam to Kuala Lumpur, was shot down over eastern Ukraine on July 17, 2014. All 283 passengers and 15 crew on board, 196 of them Dutch citizens, were killed. In the aftermath of the disaster, the Dutch Safety Board spearheaded the establishment of the multinational Joint Investigation Team (JIT), which is still engaged in a criminal probe aimed at identifying, arresting and convicting the culprits behind the unprovoked attack on Flight MH17. As part of the JIT, dozens of Dutch officials traveled to Ukraine to initiate the investigation into the plane crash and repatriate victims’ bodies and belongings. Their activities were conducted with the support of the Ukrainian government, which is party to the JIT.
Dozens of Dutch security officers, legal experts, diplomats and other civil servants were systematically spied on by Ukrainian and Russian intelligence services while probing the aftermath of the MH17 disaster, according to a report on Dutch television. Malaysia Airlines Flight 17, a scheduled passenger flight from Amsterdam to Kuala Lumpur, was shot down over eastern Ukraine on July 17, 2014. All 283 passengers and 15 crew on board, 196 of them Dutch citizens, were killed. In the aftermath of the disaster, the Dutch Safety Board spearheaded the establishment of the multinational Joint Investigation Team (JIT), which is still engaged in a criminal probe aimed at identifying, arresting and convicting the culprits behind the unprovoked attack on Flight MH17. As part of the JIT, dozens of Dutch officials traveled to Ukraine to initiate the investigation into the plane crash and repatriate victims’ bodies and belongings. Their activities were conducted with the support of the Ukrainian government, which is party to the JIT.
But on Tuesday, Holland’s RTL Niews broadcaster said that members of the Dutch JIT delegation were subjected to systematic and persistent spying by both Ukrainian and Russian government operatives. According to RTL, Dutch investigators found sophisticated eavesdropping devices in their hotel rooms in Ukraine, and believed that their electronic devices had been compromised. Citing “inside sources” from the Dutch government, the broadcaster said that, during their stay in Ukraine, members of the Dutch JIT delegation noticed that the microphones and cameras on their wireless electronic devices would turn on without being prompted. They also noticed that the devices would constantly try to connect to public WiFi networks without being prompted. Upon their return to Holland, Dutch officials had their wireless devices examined by Dutch government security experts. They were told that numerous malware were discovered on the devices.
RTL Niews said that the question of whether valuable information relating to the MH17 investigation was stolen by foreign spies remains unanswered. But it noted that the members of the Dutch JIT delegation were warned about possible espionage by foreign powers prior to traveling to Ukraine. During their stay there, they were not allowed to send messages in unencrypted format and were only permitted to hold sensitive conversations in especially designated rooms inside the Dutch embassy in Kiev. The Dutch government did not respond to questions submitted to it by RTL Niews. But it issued a statement saying that its security experts had briefed and trained the Dutch JIT delegation prior to its trip to Ukraine. Members of the delegation were told that foreign parties would seek to collect intelligence, because the MH17 investigation was taking place in a “conflict area with significant geopolitical interest” for many parties. They were therefore advised to “assume that they were being spied on [and] adjust [their] behavior accordingly” while in Ukraine, the Dutch government’s statement said.
► Author: Ian Allen | Date: 28 June 2018 | Permalink
 The Norwegian National Security Authority (NSM) has warned the country’s information technology firms to prioritize national security over cutting costs when outsourcing their operations abroad. The warning follows what has come to be known as the “Broadnet affair”, which, according to the Norwegian government, highlighted the dangers of extreme cost-cutting measures by Norway’s heavily privatized IT industry. The incident is named after Broadnet, Norway’s leading supplier of fiber-optic communications to the country’s industry and state sectors. Among Broadnet’s customers is Nødnett, an extensive digital network used by agencies and organizations that engage in rescue and emergency operations, including police and fire departments, as well as medical response agencies. Although 60% of the Nødnett network is owned by the Norwegian government, Broadnet is a member of the Nødnett consortium, and is thus supervised by Norway’s Ministry of Transport and Communications.
The Norwegian National Security Authority (NSM) has warned the country’s information technology firms to prioritize national security over cutting costs when outsourcing their operations abroad. The warning follows what has come to be known as the “Broadnet affair”, which, according to the Norwegian government, highlighted the dangers of extreme cost-cutting measures by Norway’s heavily privatized IT industry. The incident is named after Broadnet, Norway’s leading supplier of fiber-optic communications to the country’s industry and state sectors. Among Broadnet’s customers is Nødnett, an extensive digital network used by agencies and organizations that engage in rescue and emergency operations, including police and fire departments, as well as medical response agencies. Although 60% of the Nødnett network is owned by the Norwegian government, Broadnet is a member of the Nødnett consortium, and is thus supervised by Norway’s Ministry of Transport and Communications. Singaporean officials have dismissed reports that a promotional item given away for free during the June 12 summit between the leaders of the United States and North Korea contained an espionage device. Over 2500 reporters from nearly every country covered the meeting between US President Donald Trump and North Korean Supreme Leader Kim Jong-un. Upon arriving in Singapore’s Sentosa Island, where the summit took place, journalists were given a free promotional packet that included novelty items such as pens, notepads, a water bottle, and a USB fan. The USB fan consisted of blades connected to a miniature electric motor, which was in turn connected to a USB cable. The cable allowed the device to be powered by a computer or other electronic device with a built-in USB port.
Singaporean officials have dismissed reports that a promotional item given away for free during the June 12 summit between the leaders of the United States and North Korea contained an espionage device. Over 2500 reporters from nearly every country covered the meeting between US President Donald Trump and North Korean Supreme Leader Kim Jong-un. Upon arriving in Singapore’s Sentosa Island, where the summit took place, journalists were given a free promotional packet that included novelty items such as pens, notepads, a water bottle, and a USB fan. The USB fan consisted of blades connected to a miniature electric motor, which was in turn connected to a USB cable. The cable allowed the device to be powered by a computer or other electronic device with a built-in USB port. One of China’s most senior shipbuilding executives, who has not been seen in public for nearly two weeks, has been charged with giving secrets about China’s aircraft carriers to the United States. Sun Bo, 57, is general manager of the China Shipbuilding Industry Corporation (CSIC), China’s largest state-owned maritime manufacturer, which leads nearly every major shipbuilding project of the Chinese navy. Most notably, Sun headed the decade-long retrofitting of the Liaoning, a Soviet-built aircraft carrier that was commissioned to the Chinese Navy’s Surface Force after the collapse of the Soviet Union.
One of China’s most senior shipbuilding executives, who has not been seen in public for nearly two weeks, has been charged with giving secrets about China’s aircraft carriers to the United States. Sun Bo, 57, is general manager of the China Shipbuilding Industry Corporation (CSIC), China’s largest state-owned maritime manufacturer, which leads nearly every major shipbuilding project of the Chinese navy. Most notably, Sun headed the decade-long retrofitting of the Liaoning, a Soviet-built aircraft carrier that was commissioned to the Chinese Navy’s Surface Force after the collapse of the Soviet Union. The head of Germany’s domestic security agency has publicly blamed the Russian government for a large-scale cyberattack that has targeted German energy providers. The comments follow a June 13 announcement on the subject by Germany’s Federal Office for Information Security (BSI), which is charged with securing the German government’s electronic communications. According to the BSI, a widespread and systematic attack against Germany’s energy networks has been taking place for at least a year now. The attack, which the BSI codenamed BERSERK BEAR, consists of various efforts by hackers to compromise computer networks used by German companies that provide electricity and natural gas to consumers around the country.
The head of Germany’s domestic security agency has publicly blamed the Russian government for a large-scale cyberattack that has targeted German energy providers. The comments follow a June 13 announcement on the subject by Germany’s Federal Office for Information Security (BSI), which is charged with securing the German government’s electronic communications. According to the BSI, a widespread and systematic attack against Germany’s energy networks has been taking place for at least a year now. The attack, which the BSI codenamed BERSERK BEAR, consists of various efforts by hackers to compromise computer networks used by German companies that provide electricity and natural gas to consumers around the country. Israel has charged Gonen Segev, who served as the Jewish state’s Minister of Energy and Infrastructure, with spying for its archenemy, Iran. Segev, 62, was reportedly detained last month during a trip to Equatorial Guinea following a request by Israeli officials. He was then extradited to Israel and arrested as soon as he arrived in Tel Aviv last month, according to a statement by the Shin Bet, Israel’s domestic security service. On Monday it emerged that Israeli authorities had imposed a gag order on the case, forbidding Israeli media from reporting any information about it. The order appears to have now been lifted.
Israel has charged Gonen Segev, who served as the Jewish state’s Minister of Energy and Infrastructure, with spying for its archenemy, Iran. Segev, 62, was reportedly detained last month during a trip to Equatorial Guinea following a request by Israeli officials. He was then extradited to Israel and arrested as soon as he arrived in Tel Aviv last month, according to a statement by the Shin Bet, Israel’s domestic security service. On Monday it emerged that Israeli authorities had imposed a gag order on the case, forbidding Israeli media from reporting any information about it. The order appears to have now been lifted. German authorities have charged a Tunisian citizen with building a biological weapon, after finding significant quantities of the highly toxic substance ricin in his apartment. The 29-year-old man is referred to in public reports only as “Sief Allah H.”, in compliance with German law that forbids the naming of suspects until they are found guilty in court. German officials said last Thursday that the man remains in custody and has been charged with violating Germany’s War Weapons Control Act (known as Kriegswaffenkontrollgesetz) and “preparing a serious act of violence against the state”.
German authorities have charged a Tunisian citizen with building a biological weapon, after finding significant quantities of the highly toxic substance ricin in his apartment. The 29-year-old man is referred to in public reports only as “Sief Allah H.”, in compliance with German law that forbids the naming of suspects until they are found guilty in court. German officials said last Thursday that the man remains in custody and has been charged with violating Germany’s War Weapons Control Act (known as Kriegswaffenkontrollgesetz) and “preparing a serious act of violence against the state”. Belgium will investigate whether Spanish intelligence spied on Carles Puigdemont, the separatist Catalan leader who escaped to Brussels after launching an unsuccessful independence bid last year. Puigdemont, 56, served as president of the Spanish region of Catalonia from January 2016 until October 2017. He was forcibly removed from office by the Spanish government, after he led the government of Catalonia in a unilateral declaration of independence from Spain. As soon as the Catalan Parliament declared that the region was independent, Madrid dissolved it, imposed direct rule on the country’s easternmost province, and declared fresh elections.
Belgium will investigate whether Spanish intelligence spied on Carles Puigdemont, the separatist Catalan leader who escaped to Brussels after launching an unsuccessful independence bid last year. Puigdemont, 56, served as president of the Spanish region of Catalonia from January 2016 until October 2017. He was forcibly removed from office by the Spanish government, after he led the government of Catalonia in a unilateral declaration of independence from Spain. As soon as the Catalan Parliament declared that the region was independent, Madrid dissolved it, imposed direct rule on the country’s easternmost province, and declared fresh elections. The United States has for the first time imposed economic sanctions on a number of Russian companies, which it says helped the Kremlin spy on targets in North America and Western Europe. On Monday, the US Department of the Treasury said it would apply severe economic restrictions on a number of Russian firms that work closely with the Kremlin. One of the companies was
The United States has for the first time imposed economic sanctions on a number of Russian companies, which it says helped the Kremlin spy on targets in North America and Western Europe. On Monday, the US Department of the Treasury said it would apply severe economic restrictions on a number of Russian firms that work closely with the Kremlin. One of the companies was  A lengthy exposé by a leading American newsmagazine has claimed that Israel and the United Arab Emirates, two countries that officially have no relations, have been secretly collaborating for more than two decades. Their secret cooperation has been extremely tight and has included clandestine weapons sales and intelligence-sharing, according to the exposé, which was published on the website of The New Yorker on Monday and will feature in the magazine’s print edition on June 18. The lengthy piece, which deals with the changing geopolitics of the Middle East, is written by Adam Entous, national security correspondent for The Washington Post, who has previously reported for more than two decades for Reuters and The Wall Street Journal.
A lengthy exposé by a leading American newsmagazine has claimed that Israel and the United Arab Emirates, two countries that officially have no relations, have been secretly collaborating for more than two decades. Their secret cooperation has been extremely tight and has included clandestine weapons sales and intelligence-sharing, according to the exposé, which was published on the website of The New Yorker on Monday and will feature in the magazine’s print edition on June 18. The lengthy piece, which deals with the changing geopolitics of the Middle East, is written by Adam Entous, national security correspondent for The Washington Post, who has previously reported for more than two decades for Reuters and The Wall Street Journal.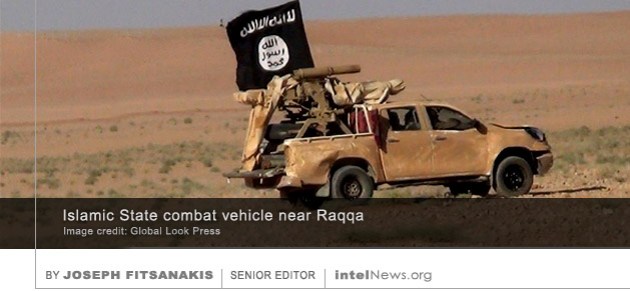 In a recent series of interviews to promote his new book, Anatomy of Terror, former FBI special agent and current counterterrorism expert Ali Soufan insists that the Islamic State remains potent and dangerous.
In a recent series of interviews to promote his new book, Anatomy of Terror, former FBI special agent and current counterterrorism expert Ali Soufan insists that the Islamic State remains potent and dangerous.  way out. The group’s meteoric rise marked a watershed moment in the modern history of militant Sunni Islam. Even if it is militarily annihilated —a prospect that is far from certain— its physical absence will in no way erase its impact and influence among its millions of supporters and sympathizers. In fact, experts warn that the group is —like al-Qaeda before it— proving to be resilient and able to withstand intense military pressure from its enemies. Currently, all signs show that the Islamic State is actively reorganizing under the command of its leader, Abu Bakr al-Baghdadi. The prolonged absence of the Iraqi-born al-Baghdadi has prompted wild speculation about this supposed demise or severe incapacitation. There are even some who
way out. The group’s meteoric rise marked a watershed moment in the modern history of militant Sunni Islam. Even if it is militarily annihilated —a prospect that is far from certain— its physical absence will in no way erase its impact and influence among its millions of supporters and sympathizers. In fact, experts warn that the group is —like al-Qaeda before it— proving to be resilient and able to withstand intense military pressure from its enemies. Currently, all signs show that the Islamic State is actively reorganizing under the command of its leader, Abu Bakr al-Baghdadi. The prolonged absence of the Iraqi-born al-Baghdadi has prompted wild speculation about this supposed demise or severe incapacitation. There are even some who  The majority of government-sponsored hacking now targets cell phones, not personal computers, according to researchers who say that political dissidents are especially targeted by totalitarian regimes around the world. Until 2015, most government-sponsored hacking operations were directed against the personal computers of targeted individuals. However, experts
The majority of government-sponsored hacking now targets cell phones, not personal computers, according to researchers who say that political dissidents are especially targeted by totalitarian regimes around the world. Until 2015, most government-sponsored hacking operations were directed against the personal computers of targeted individuals. However, experts  The United States has evacuated at least two more diplomatic personnel from its consulate in the Chinese city of Guangzhou, after they experienced “unusual acute auditory or sensory phenomena” and “unusual sounds or piercing noises”. The latest evacuations come two weeks after the US Department of State
The United States has evacuated at least two more diplomatic personnel from its consulate in the Chinese city of Guangzhou, after they experienced “unusual acute auditory or sensory phenomena” and “unusual sounds or piercing noises”. The latest evacuations come two weeks after the US Department of State  The online social media company Facebook shares data about its users with a Chinese telecommunications company that has been flagged in United States government reports as a threat to security. The New York Times
The online social media company Facebook shares data about its users with a Chinese telecommunications company that has been flagged in United States government reports as a threat to security. The New York Times 






More spies now in Brussels than Vienna, Austrian intelligence chief says
June 29, 2018 by Joseph Fitsanakis 2 Comments
Furthermore, Vienna hosts the headquarters of several important international agencies, including the Organization of Petroleum Exporting Countries (OPEC), the International Atomic Energy Agency (IAEA), and the Organization for Security and Co-Operation in Europe (OSCE). This gives dozens of countries the opportunity to station in Vienna large numbers of diplomats, in addition to those who staff their embassies there. Consequently, it is estimated that the Austrian capital today hosts nearly 20,000 foreign diplomats, which is a substantial number for such a small country with a permanent population of less than 9 million. Experts believe that around half of these foreign diplomats are in fact connected to a foreign intelligence agency.
But in a rare public appearance on Thursday, Peter Gridling, head of Austria’s main counterintelligence agency, said that Vienna no longer topped the list of preferred destinations for the world’s spies. Gridling heads the Vienna-based Federal Office for the Protection of the Constitution and Counterterrorism, known as BVT. He was speaking during the official presentation of the BVT’s annual Constitutional Protection Report for 2017, which was held at the headquarters of the Ministry of the Interior. Gridling told reporters that the number of foreign intelligence operatives pretending to be diplomats posted in the Austrian capital remained significant, and that Austria as a whole was still “a favored area of operations” by the world’s intelligence agencies. However, he added that Vienna had now been overtaken by the Belgian capital Brussels as the spy capital of Europe. Gridling said that, according to his agency’s calculations, there was now a greater density of spies in Brussels than in any other European capital.
Gridling thus appears to concur with numerous intelligence experts and practitioners, among them Alain Winants, former Director of Belgium’s State Security Service (SV/SE), who have claimed since 2009 that Brussels is home to more spies than any other city in the world. When asked to specify the number of foreign intelligence operatives that are active in Vienna, Gridling said it was “in the neighborhood of hundreds of people, but certainly fewer than 1,000”. The Austrian counterintelligence chief declined calls to provide further elaboration on the mater.
► Author: Joseph Fitsanakis | Date: 29 June 2018 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with Austria, Belgium, Brussels, BVT (Austria), espionage, News, Vienna