Sophistication of Hamas official’s killing points to Mossad, say sources
March 28, 2017 4 Comments
 The sophistication behind the killing of a senior Hamas official, who was assassinated in his home in the Gaza Strip on Friday evening, points almost certainly to Israel, according to observers. Mazen Faqha, 38, helped plan several lethal operations by the Palestinian militant group, including a 2002 suicide bombing that killed nine and wounded over 50. Following an extensive manhunt, Israeli authorities arrested Faqha in the West Bank and in 2003 convicted him to nine life sentences. But in 2011, Faqha was among 1,027 Palestinian and Arab-Israeli prisoners that Israel released in exchange for Gilad Shalit, a soldier in the Israel Defense Forces, who was held prisoner by Hamas. Since that time, Faqha had lived in the Gaza Strip, the Hamas-controlled Palestinian enclave that has been under strict Israeli blockade since 2006.
The sophistication behind the killing of a senior Hamas official, who was assassinated in his home in the Gaza Strip on Friday evening, points almost certainly to Israel, according to observers. Mazen Faqha, 38, helped plan several lethal operations by the Palestinian militant group, including a 2002 suicide bombing that killed nine and wounded over 50. Following an extensive manhunt, Israeli authorities arrested Faqha in the West Bank and in 2003 convicted him to nine life sentences. But in 2011, Faqha was among 1,027 Palestinian and Arab-Israeli prisoners that Israel released in exchange for Gilad Shalit, a soldier in the Israel Defense Forces, who was held prisoner by Hamas. Since that time, Faqha had lived in the Gaza Strip, the Hamas-controlled Palestinian enclave that has been under strict Israeli blockade since 2006.
Last Friday, March 24, Faqha was found dead inside the garage of his apartment block in Tel el-Hawa, a densely populated neighborhood in southwestern Gaza City. Initial reports stated that the Hamas official had been shot dead by a team of assailants outside his home. But subsequent accounts revealed that several gunmen were waiting for Faqha inside the car garage located on the bottom floor of the building that houses his apartment. It now appears that the assailants had been hiding in the garage for several hours before Faqha entered it with his car. Minutes earlier, his wife and young daughter had exited the car and made their way to the front door of their apartment. As soon as Faqha drove his car to the garage and closed the garage’s electric door, the gunmen shot him four times in the head from point-blank range and vanished. There was hardly a sound, because the assailants used weapons equipped with silencers. Faqha’s body was not discovered until 7:30 in the evening, a full 90 minutes after he was shot dead. His wife apparently thought that he was talking to their neighbors.
Investigators who are looking into Faqha’s murder say that his killers were intimately familiar with the architectural details of the apartment building where he lived, and had studied his daily routine. They also made sure to leave no traces behind. Consequently, their identity remains a mystery despite the presence of security cameras around the building. Hamas security officials say they believe that Faqha’s killers entered and exited the Gaza Strip by boat. The Palestinian militant group lost little time in blaming the murder on the Mossad, Israel’s primary external intelligence agency, which has targeted several Hamas officials for assassination in the past. Khalil al-Haya, Hamas’ second-in-command in the Gaza Strip said that Israel was the only beneficiary of Faqha’s demise. Khaled Mashal, who chairs Hamas’ Political Bureau, said Israel had “changed the rules of the game” by killing Faqha, adding that Hamas would “accept the challenge”. There has been no official comment from Israel in regards to Faqha’s killing.
► Author: Joseph Fitsanakis | Date: 28 March 2017 | Permalink | Research credit: SF
 Comments made by a senior American intelligence official on Tuesday appeared to suggest that the North Korean government was behind an attempt to steal nearly $1 billion from a Bangladeshi bank last year. The heist took place in February of 2016, when a computer malware was used to issue several requests to transfer funds from Bangladesh Bank —the state-owned central bank of Bangladesh— using the SWIFT network. The hackers were able to transfer five separate sums of $101 million each to a linked Bangladesh Bank account at New York’s Federal Reserve Bank. However, when further requests were issued, Federal Reserve Bank employees contacted Bangladesh Bank and blocked further transactions. Eventually, most of the transferred funds, which neared $1 billion, were recovered; but the hackers managed to get away with approximately $81 million worth of funds.
Comments made by a senior American intelligence official on Tuesday appeared to suggest that the North Korean government was behind an attempt to steal nearly $1 billion from a Bangladeshi bank last year. The heist took place in February of 2016, when a computer malware was used to issue several requests to transfer funds from Bangladesh Bank —the state-owned central bank of Bangladesh— using the SWIFT network. The hackers were able to transfer five separate sums of $101 million each to a linked Bangladesh Bank account at New York’s Federal Reserve Bank. However, when further requests were issued, Federal Reserve Bank employees contacted Bangladesh Bank and blocked further transactions. Eventually, most of the transferred funds, which neared $1 billion, were recovered; but the hackers managed to get away with approximately $81 million worth of funds. An Israeli military official has repeated claims in the Arab media that the Lebanese Shiite group Hezbollah killed its own military commander in Syria, following a dispute with Iran. Mustafa Amine Badreddine, 55, an expert in explosives and former bomb-maker, was a senior military commander in the military wing of Hezbollah. He rose through the ranks of the organization to become a trusted adviser to Hezbollah’s Secretary General, Hassan Nasrallah. In 2011, the Special Tribunal for Lebanon, set up by the United Nations, charged Badreddine with organizing the assassination of Lebanese Prime Minister Rafik Hariri. Hariri was killed with over 20 other people in a massive bomb blast in Beirut, in February of 2005.
An Israeli military official has repeated claims in the Arab media that the Lebanese Shiite group Hezbollah killed its own military commander in Syria, following a dispute with Iran. Mustafa Amine Badreddine, 55, an expert in explosives and former bomb-maker, was a senior military commander in the military wing of Hezbollah. He rose through the ranks of the organization to become a trusted adviser to Hezbollah’s Secretary General, Hassan Nasrallah. In 2011, the Special Tribunal for Lebanon, set up by the United Nations, charged Badreddine with organizing the assassination of Lebanese Prime Minister Rafik Hariri. Hariri was killed with over 20 other people in a massive bomb blast in Beirut, in February of 2005.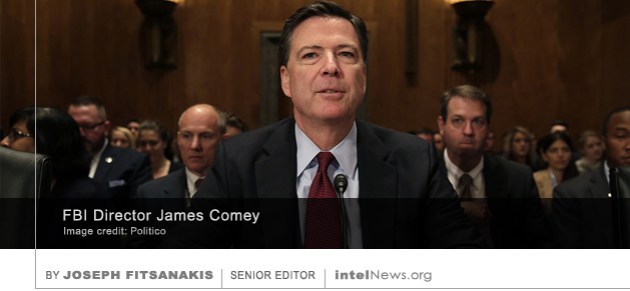 Monday’s official announcement that an investigation is underway into alleged Russian involvement in the 2016 United States presidential election was an important moment in American political history. It exposed the chaotic state of American politics and added yet another layer of complexity in an already intricate affair, from which the country’s institutions will find it difficult to recover for years to come. This is regardless of the outcome of the investigation, which is being conducted by the Federal Bureau of Investigation. Even if it fails to produce a ‘smoking gun’, the very fact that the country’s chief counterintelligence agency is examining the possibility that a US president was elected with help from Russia, is an astonishing development without parallel in modern American history.
Monday’s official announcement that an investigation is underway into alleged Russian involvement in the 2016 United States presidential election was an important moment in American political history. It exposed the chaotic state of American politics and added yet another layer of complexity in an already intricate affair, from which the country’s institutions will find it difficult to recover for years to come. This is regardless of the outcome of the investigation, which is being conducted by the Federal Bureau of Investigation. Even if it fails to produce a ‘smoking gun’, the very fact that the country’s chief counterintelligence agency is examining the possibility that a US president was elected with help from Russia, is an astonishing development without parallel in modern American history.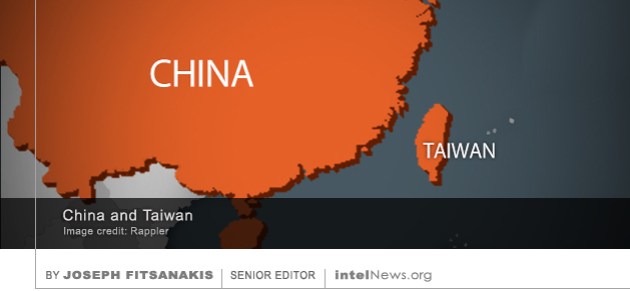 A Taiwanese government official has alleged that China maintains an army of more than 5,000 spies in Taiwan, many of whom have infiltrated the highest levels of government and industry. The allegation came after two sensational arrests were made in Taiwan last week, of people accused of spying for Beijing. Taiwanese counterintelligence officers reportedly arrested a bodyguard of Annette Lu, Taiwan’s former vice president. The bodyguard, who has been identified in Taiwanese media as Wang Hong-ju, has been charged with receiving payments from his Chinese intelligence handler in return for providing information about Mrs. Lu. This incident followed another arrest, made earlier in the week, this time of a Chinese man who is believed to have initially come to Taiwan as a student. Zhou Hong-xu is
A Taiwanese government official has alleged that China maintains an army of more than 5,000 spies in Taiwan, many of whom have infiltrated the highest levels of government and industry. The allegation came after two sensational arrests were made in Taiwan last week, of people accused of spying for Beijing. Taiwanese counterintelligence officers reportedly arrested a bodyguard of Annette Lu, Taiwan’s former vice president. The bodyguard, who has been identified in Taiwanese media as Wang Hong-ju, has been charged with receiving payments from his Chinese intelligence handler in return for providing information about Mrs. Lu. This incident followed another arrest, made earlier in the week, this time of a Chinese man who is believed to have initially come to Taiwan as a student. Zhou Hong-xu is  Russia may have become the latest country to deploy special forces soldiers in Libya, according to news reports citing anonymous United States officials. Late on Tuesday, the Reuters news agency
Russia may have become the latest country to deploy special forces soldiers in Libya, according to news reports citing anonymous United States officials. Late on Tuesday, the Reuters news agency  United States President Donald Trump has reportedly authorized the Central Intelligence Agency to bring back the routine use of lethal airstrikes by unmanned aerial vehicles (UAVs), which his predecessor, Barack Obama, curtailed in 2013. Washington began employing limited strikes by UAVs, otherwise known as drones, in the early 1990s, during the administration of President Bill Clinton. But it was under the Obama administration that the use of drone strikes reached an all-time high, with hundreds of such attacks documented after 2008. It is believed that Obama used this remote attack method to combat the Taliban and al-Qaeda, while at the same time keeping his promise of bringing back American troops from the Middle East and Central Asia. However, in 2013 the US president severely curtailed the controversial program, which some say damaged America’s image by inflicting civilian casualties.
United States President Donald Trump has reportedly authorized the Central Intelligence Agency to bring back the routine use of lethal airstrikes by unmanned aerial vehicles (UAVs), which his predecessor, Barack Obama, curtailed in 2013. Washington began employing limited strikes by UAVs, otherwise known as drones, in the early 1990s, during the administration of President Bill Clinton. But it was under the Obama administration that the use of drone strikes reached an all-time high, with hundreds of such attacks documented after 2008. It is believed that Obama used this remote attack method to combat the Taliban and al-Qaeda, while at the same time keeping his promise of bringing back American troops from the Middle East and Central Asia. However, in 2013 the US president severely curtailed the controversial program, which some say damaged America’s image by inflicting civilian casualties. Boris Johnson, the British foreign secretary has said in an interview that Russian spies may have orchestrated last year’s failed attempt to kill the then-prime minister of Montenegro, Milo Dukanović. Mr. Johnson, a senior figure in the Conservative Party of the United Kingdom, was a major contender for the prime minister’s position in 2016, after the administration of David Cameron collapsed under the weight of the Brexit vote result. Speaking on Sunday morning to reporter Robert Peston, of Britain’s ITV television network, Mr. Johnson said that the West should “engage” with Russia, but warned that it should also “beware” of Moscow’s “dirty tricks” in Europe and the United States.
Boris Johnson, the British foreign secretary has said in an interview that Russian spies may have orchestrated last year’s failed attempt to kill the then-prime minister of Montenegro, Milo Dukanović. Mr. Johnson, a senior figure in the Conservative Party of the United Kingdom, was a major contender for the prime minister’s position in 2016, after the administration of David Cameron collapsed under the weight of the Brexit vote result. Speaking on Sunday morning to reporter Robert Peston, of Britain’s ITV television network, Mr. Johnson said that the West should “engage” with Russia, but warned that it should also “beware” of Moscow’s “dirty tricks” in Europe and the United States.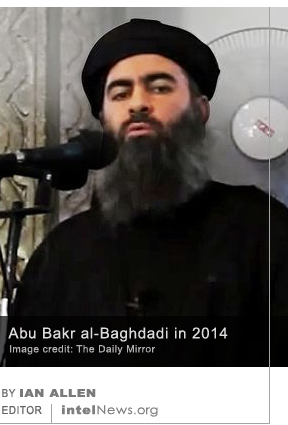 The leader of the Islamic State has abandoned the city of Mosul and is hiding in the desert zone of western Iraq, according to intelligence sources. Meanwhile Mosul, once the most populous city under the Islamic State’s control, is now reportedly being defended by a diminishing cadre of fewer than 3,000 Sunni militants, who are facing a 110,000-strong invading army.
The leader of the Islamic State has abandoned the city of Mosul and is hiding in the desert zone of western Iraq, according to intelligence sources. Meanwhile Mosul, once the most populous city under the Islamic State’s control, is now reportedly being defended by a diminishing cadre of fewer than 3,000 Sunni militants, who are facing a 110,000-strong invading army. The United States federal government has launched a criminal investigation into the public disclosure of thousands of documents that purportedly belong to the Central Intelligence Agency. The documents were
The United States federal government has launched a criminal investigation into the public disclosure of thousands of documents that purportedly belong to the Central Intelligence Agency. The documents were 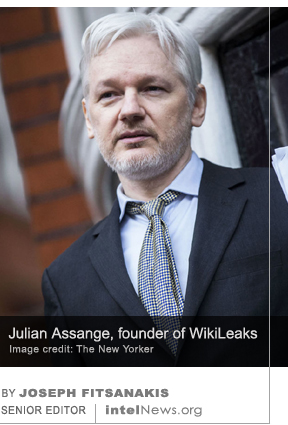 Thousands of documents belonging to the United States Central Intelligence Agency, which were released on Tuesday by the international anti-secrecy website WikiLeaks, are almost certainly genuine. They reveal an entire universe of technical intelligence collection methods used by the CIA to extract information from digital applications and electronic devices, ranging from flash drives to smart screen televisions. WikiLeaks named the collection
Thousands of documents belonging to the United States Central Intelligence Agency, which were released on Tuesday by the international anti-secrecy website WikiLeaks, are almost certainly genuine. They reveal an entire universe of technical intelligence collection methods used by the CIA to extract information from digital applications and electronic devices, ranging from flash drives to smart screen televisions. WikiLeaks named the collection  The sensational assassination of Kim Jong-nam, half-brother of North Korea’s Supreme Leader Kim Jong-un, on February 13, revealed much about the current operational mindset of Pyongyang. But it also brought to light the shady network of front companies set up by the North Korean regime to facilitate the country’s illicit financial activities around the world. This extensive network permits Pyongyang to evade international sanctions against it, and to coordinate the activities of hundreds of clandestine operatives around the world. Through these activities, the reclusive country has been able to develop its weapons of mass destruction program unabated, despite concerted efforts by the United Nations to prevent it from doing so.
The sensational assassination of Kim Jong-nam, half-brother of North Korea’s Supreme Leader Kim Jong-un, on February 13, revealed much about the current operational mindset of Pyongyang. But it also brought to light the shady network of front companies set up by the North Korean regime to facilitate the country’s illicit financial activities around the world. This extensive network permits Pyongyang to evade international sanctions against it, and to coordinate the activities of hundreds of clandestine operatives around the world. Through these activities, the reclusive country has been able to develop its weapons of mass destruction program unabated, despite concerted efforts by the United Nations to prevent it from doing so.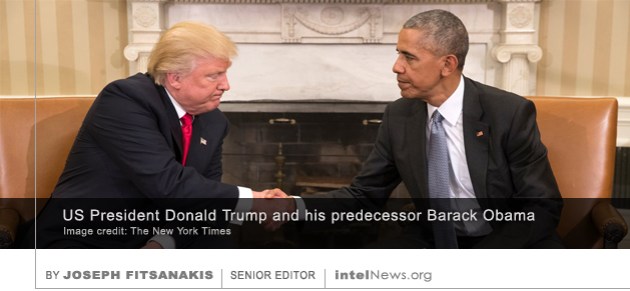 The absurdity of American politics reached new heights over the weekend, as President Donald Trump dramatically alleged on Twitter that his predecessor, Barack Obama, wiretapped his telephones last year. Even for a highly impulsive public figure known for his sensational and often-unsubstantiated allegations, Mr. Trump’s latest claims prompted a new sense of abnormality and astonishment in Washington. If the president is unable to prove his dramatic claims, his reliability will be further-eroded, and what little is left of his relationship with the American intelligence and national-security communities will disintegrate. If his allegations are proven, they will cause a scandal of unprecedented proportions from which American political institutions —including the presidency— will find it difficult to recover.
The absurdity of American politics reached new heights over the weekend, as President Donald Trump dramatically alleged on Twitter that his predecessor, Barack Obama, wiretapped his telephones last year. Even for a highly impulsive public figure known for his sensational and often-unsubstantiated allegations, Mr. Trump’s latest claims prompted a new sense of abnormality and astonishment in Washington. If the president is unable to prove his dramatic claims, his reliability will be further-eroded, and what little is left of his relationship with the American intelligence and national-security communities will disintegrate. If his allegations are proven, they will cause a scandal of unprecedented proportions from which American political institutions —including the presidency— will find it difficult to recover. order at the highest levels of the American government, Mr. Trump’s claims cannot possibly be true. American presidents have not been legally allowed to order wiretaps since 1978, when the Foreign Intelligence Surveillance Act (FISA) was established. Prompted by the abuse of executive power revealed through the Watergate scandal, FISA forces government agencies to seek the approval of specially mandated judges before installing wiretaps. If an agency like the Federal Bureau of Investigation (FBI) wants to wiretap an individual or group suspected of acting as agents of a foreign power, it must convince one of 11 federal district judges who rotate on the FISA court that the case warrants a wiretap order. Thus, before authorizing the wiretap, a FISA judge must be convinced by examining the available evidence presented before him or her.
order at the highest levels of the American government, Mr. Trump’s claims cannot possibly be true. American presidents have not been legally allowed to order wiretaps since 1978, when the Foreign Intelligence Surveillance Act (FISA) was established. Prompted by the abuse of executive power revealed through the Watergate scandal, FISA forces government agencies to seek the approval of specially mandated judges before installing wiretaps. If an agency like the Federal Bureau of Investigation (FBI) wants to wiretap an individual or group suspected of acting as agents of a foreign power, it must convince one of 11 federal district judges who rotate on the FISA court that the case warrants a wiretap order. Thus, before authorizing the wiretap, a FISA judge must be convinced by examining the available evidence presented before him or her. Britain’s primary external-intelligence agency will revert to old-fashioned ways of recruiting employees, including the co-called “tap on the shoulder” method, according to its director. Known informally as MI6, the Secret Intelligence Service (SIS) was founded in 1908 to protect Britain’s national security by collecting intelligence from foreign sources. However, the agency has had difficulty recruiting a diverse group of people, and many still view it as a professional destination for a small wealthy elite, drawn primarily from Britain’s most prestigious universities such as Oxford and Cambridge.
Britain’s primary external-intelligence agency will revert to old-fashioned ways of recruiting employees, including the co-called “tap on the shoulder” method, according to its director. Known informally as MI6, the Secret Intelligence Service (SIS) was founded in 1908 to protect Britain’s national security by collecting intelligence from foreign sources. However, the agency has had difficulty recruiting a diverse group of people, and many still view it as a professional destination for a small wealthy elite, drawn primarily from Britain’s most prestigious universities such as Oxford and Cambridge.






Germany publicly rejects Turkish spies’ request to monitor dissidents
March 29, 2017 by Joseph Fitsanakis Leave a comment
Since the end of the failed coup, the Turkish state has initiated a nationwide political crackdown against alleged supporters of the coup. Over 100,000 people have been fired from their jobs, while hundreds of thousands have been demoted, censured or warned. Another 41,000 are believed to be in prison, charged with supporting the failed coup or being members of the Gülen network. But many observers in Europe view the coup as a catalyst that was exploited by the government in Ankara neutralize its political opponents.
On Monday, Germany’s Süddeutsche Zeitung newspaper claimed that Turkey’s National Intelligence Organization, known as MİT, gave its German counterpart a list containing the names hundreds of Turks living in Germany, and asked him to spy on them. According to the newspaper, the list was given by MİT chief Hakan Fidan to Bruno Kahl, head of the Bundesnachrichtendienst, Germany’s Federal Intelligence Service, known as BND. The two men allegedly met at a security conference held in Munich last February. The Süddeutsche Zeitung claims that the list given to Kahl included 300 individuals and approximately 200 groups and organizations that the MİT wanted the BND to monitor.
But instead of spying on these targets, the BND wrote to them and warned them that the Turkish state was after them. The German spy agency also warned them to stay away from any contact with Turkish authorities in Germany and to refrain from traveling to Turkey. On Tuesday, Germany’s Interior Minister, Thomas De Maiziere, confirmed the Süddeutsche Zeitung article and warned Turkey to respect Germany’s territorial sovereignty. “Here German jurisdiction applies”, said De Maiziere, “and citizens will not be spied on by foreign countries”.
► Author: Joseph Fitsanakis | Date: 29 March 2017 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with 2016 Turkish coup d'état attempt, BND, Bruno Kahl, Germany, Hakan Fidan, immigration intelligence, MİT (Turkey), News, Turkey