CIA names first woman to lead Directorate of Operations
December 11, 2018 2 Comments
 In a surprising departure from established practice, the United States Central Intelligence Agency has publicized the name of its incoming head of operations. Beth Kimber, a 34-year veteran of the Agency, will become the first woman in the CIA’s 70-year history to lead the Directorate of Operations. Officers in the Directorate of Operations, formerly known as the National Clandestine Service, spend their careers recruiting foreign agents to spy for the United States, while also carrying out covert operations around the world. This is also the first time that the CIA has chosen to publicly identify its Deputy Director for Operations —Kimber’s official title, abbreviated as DDO. Previous DDO have been undercover officers whose namse have remained undisclosed. Kimber’s promotion was announced on December 7 by Brittany Bramell, the CIA’s Director of Public Affairs.
In a surprising departure from established practice, the United States Central Intelligence Agency has publicized the name of its incoming head of operations. Beth Kimber, a 34-year veteran of the Agency, will become the first woman in the CIA’s 70-year history to lead the Directorate of Operations. Officers in the Directorate of Operations, formerly known as the National Clandestine Service, spend their careers recruiting foreign agents to spy for the United States, while also carrying out covert operations around the world. This is also the first time that the CIA has chosen to publicly identify its Deputy Director for Operations —Kimber’s official title, abbreviated as DDO. Previous DDO have been undercover officers whose namse have remained undisclosed. Kimber’s promotion was announced on December 7 by Brittany Bramell, the CIA’s Director of Public Affairs.
Little is known about Kimber, who spent much of her career as a case officer before joining the CIA’s senior intelligence staff. She is a graduate of Hamilton College, a private, liberal arts college situated in upstate New York, and spent much of her early career with the CIA as a case officer in Western Europe. She is also believed to have led the “Russia Group”, a network of intelligence planners in the CIA’s Directorate of Operations that manage a broad spectrum of espionage operations targeting the Russian spy services. She has also served as deputy director of the National Clandestine Service, before it was renamed to Directorate of Operations. Newsweek intelligence correspondent Jeff Stein wrote about Kimber in 2014, but did not name her, as she was still serving in an undercover capacity.
For a few months this year, Kimber served as the CIA’s acting deputy director while Congress considered President Donald Trump’s nomination of Gina Haspel’s for the Agency’s director position. Kimber’s most recent prior post in the CIA was head of the Agency’s Europe and Eurasia Mission Center. Kimber is the third woman to assume a central role in the CIA in the past six months. In May of this year, Gina Haspel, a 33-year veteran of the CIA, became the Agency’s first female director. In August, Haspel picked Sonya Holt, a 34-year CIA veteran, to serve as the Agency’s chief diversity and inclusion officer. On Friday, the American news network CBS cited “people familiar with the shift”, who said that the outgoing DDO “will take another role within the agency” and is expected to remain undercover.
► Author: Joseph Fitsanakis | Date: 11 December 2018 | Permalink
 A Russian former police officer, who is serving a prison sentence in Russia for having spied for the United States Central Intelligence Agency, has written an open letter to President Donald Trump, asking to be freed. Yevgeny A. Chistov was arrested by the Russian Federal Security Service (FSB) in 2014 on charges of spying for Washington. During his trial, he admitted having been recruited by the CIA when he worked as an officer in the police, Russia’s federal law-enforcement agency, which operates under the Ministry of Internal Affairs. Russian state prosecutors accused him of having established contact with the CIA in 2011. In 2015, he was
A Russian former police officer, who is serving a prison sentence in Russia for having spied for the United States Central Intelligence Agency, has written an open letter to President Donald Trump, asking to be freed. Yevgeny A. Chistov was arrested by the Russian Federal Security Service (FSB) in 2014 on charges of spying for Washington. During his trial, he admitted having been recruited by the CIA when he worked as an officer in the police, Russia’s federal law-enforcement agency, which operates under the Ministry of Internal Affairs. Russian state prosecutors accused him of having established contact with the CIA in 2011. In 2015, he was  A report from the United States Department of Defense warns that the Islamic State is swiftly returning to its insurgent roots, as observers in Iraq and Syria caution that the group is witnessing a revival. It has been four years since the Islamic State —known then as the Islamic State of Iraq and Syria, or ISIS— conquered much of eastern Syria and more than a third of Iraq’s territory. But by the end of 2017, virtually the entirety of ISIS’ self-styled ‘caliphate’ had been obliterated by an ‘unholy alliance’ of US-backed Iraqi government forces, Iranian-supported Shiite militias, Kurdish guerillas and Western airpower.
A report from the United States Department of Defense warns that the Islamic State is swiftly returning to its insurgent roots, as observers in Iraq and Syria caution that the group is witnessing a revival. It has been four years since the Islamic State —known then as the Islamic State of Iraq and Syria, or ISIS— conquered much of eastern Syria and more than a third of Iraq’s territory. But by the end of 2017, virtually the entirety of ISIS’ self-styled ‘caliphate’ had been obliterated by an ‘unholy alliance’ of US-backed Iraqi government forces, Iranian-supported Shiite militias, Kurdish guerillas and Western airpower. The daughter of the founder of Huawei Technologies, one of the world’s leading telecommunications hardware manufacturers, has been arrested in Canada, reportedly at the request of the United States. Meng Wanzhou (pictured, also known as Sabrina Meng) serves as Huawei’s deputy chair and chief financial officer. She is the daughter of Ren Zhengfei a former officer in the Chinese People’s Liberation Army, who established the company in 1988 and has since amassed a personal fortune estimated at $3.5 billion. By virtue of her family background and position in Huawei, Meng is often
The daughter of the founder of Huawei Technologies, one of the world’s leading telecommunications hardware manufacturers, has been arrested in Canada, reportedly at the request of the United States. Meng Wanzhou (pictured, also known as Sabrina Meng) serves as Huawei’s deputy chair and chief financial officer. She is the daughter of Ren Zhengfei a former officer in the Chinese People’s Liberation Army, who established the company in 1988 and has since amassed a personal fortune estimated at $3.5 billion. By virtue of her family background and position in Huawei, Meng is often  The main domestic intelligence agency of the Czech Republic has accused Russia of “the most serious wave of cyberespionage” to target the country in recent years. The claim was made on Monday in Prague by the Security Information Service (BIS), the primary domestic national intelligence agency of the Czech Republic. Details of the alleged cyberespionage plot are included in the BIS’
The main domestic intelligence agency of the Czech Republic has accused Russia of “the most serious wave of cyberespionage” to target the country in recent years. The claim was made on Monday in Prague by the Security Information Service (BIS), the primary domestic national intelligence agency of the Czech Republic. Details of the alleged cyberespionage plot are included in the BIS’  The director of Britain’s Secret Intelligence Service —known as MI6— has outlined the parameters of a new, “fourth generation of espionage”, which he said is needed to combat the “threats of the hybrid age”. Alex Younger, 55, is a career intelligence officer who joined MI6 in 1991, after serving in the British Army. He served as chief of global operations —considered the number two position at MI6— before being
The director of Britain’s Secret Intelligence Service —known as MI6— has outlined the parameters of a new, “fourth generation of espionage”, which he said is needed to combat the “threats of the hybrid age”. Alex Younger, 55, is a career intelligence officer who joined MI6 in 1991, after serving in the British Army. He served as chief of global operations —considered the number two position at MI6— before being  Saudi Crown Prince Mohammed bin Salman sent at least eleven text messages to the man in charge of the 15-member hit team that killed journalist Jamal Khashoggi last month, according to a classified report produced by the United States Central Intelligence Agency. The CIA report was leaked to The Wall Street Journal, which said in a
Saudi Crown Prince Mohammed bin Salman sent at least eleven text messages to the man in charge of the 15-member hit team that killed journalist Jamal Khashoggi last month, according to a classified report produced by the United States Central Intelligence Agency. The CIA report was leaked to The Wall Street Journal, which said in a  The United States government plan to impose tighter visa restrictions and wider background checks on Chinese nationals studying at American universities, over espionage concerns. The news follows reports earlier this year that the administration of US President Donald Trump considered banning all Chinese nationals from studying at American universities. In October of this year, The Financial Times
The United States government plan to impose tighter visa restrictions and wider background checks on Chinese nationals studying at American universities, over espionage concerns. The news follows reports earlier this year that the administration of US President Donald Trump considered banning all Chinese nationals from studying at American universities. In October of this year, The Financial Times  The Australian government has proposed a new law that would give intelligence officers broader powers to use firearms during undercover operations abroad. If it is approved by parliament, the new law would apply to the Australian Secret Intelligence Service (ASIS), a civilian intelligence agency that carries out covert and clandestine operations abroad. Modeled after Britain’s Secret Intelligence Service (MI6), ASIS was established in 1952, but its existence was not officially acknowledged by the Australian government until 25 years later, in 1977.
The Australian government has proposed a new law that would give intelligence officers broader powers to use firearms during undercover operations abroad. If it is approved by parliament, the new law would apply to the Australian Secret Intelligence Service (ASIS), a civilian intelligence agency that carries out covert and clandestine operations abroad. Modeled after Britain’s Secret Intelligence Service (MI6), ASIS was established in 1952, but its existence was not officially acknowledged by the Australian government until 25 years later, in 1977. A senior North Korea expert in the United States Central Intelligence Agency, who has been instrumental in the ongoing negotiations between Washington and Pyongyang, has tendered his resignation, according to sources. The official was
A senior North Korea expert in the United States Central Intelligence Agency, who has been instrumental in the ongoing negotiations between Washington and Pyongyang, has tendered his resignation, according to sources. The official was  A senior civil servant in the upper house of the French parliament has been arrested on suspicion of spying for North Korea, according to prosecutors. The news of the suspected spy’s arrest was first
A senior civil servant in the upper house of the French parliament has been arrested on suspicion of spying for North Korea, according to prosecutors. The news of the suspected spy’s arrest was first 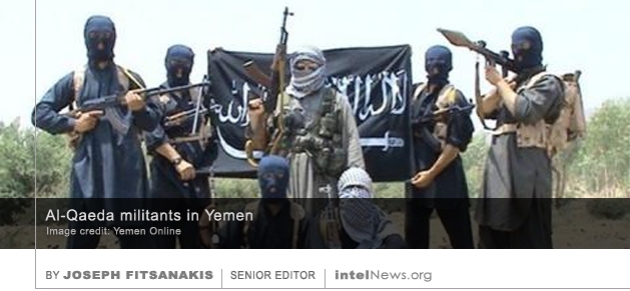 There are four times as many Sunni Islamist militants today in the world than on September 11, 2001, despite an almost 20 year-long war campaign by the United States and its allies, according to a new report. Washington launched the ‘global war on terrorism’ in the aftermath of the 9/11 attacks that were perpetrated by al-Qaeda. In the ensuing years, American and other Western troops have engaged militarily in over a dozen countries, including Afghanistan, Iraq, Pakistan, Syria, Libya, Yemen, Somalia, Sudan, and the Philippines. But a
There are four times as many Sunni Islamist militants today in the world than on September 11, 2001, despite an almost 20 year-long war campaign by the United States and its allies, according to a new report. Washington launched the ‘global war on terrorism’ in the aftermath of the 9/11 attacks that were perpetrated by al-Qaeda. In the ensuing years, American and other Western troops have engaged militarily in over a dozen countries, including Afghanistan, Iraq, Pakistan, Syria, Libya, Yemen, Somalia, Sudan, and the Philippines. But a  The amount of poison smuggled into Britain for a near-fatal attack on Russian former spy Sergei Skripal was powerful enough to kill “thousands of people”, according those leading the investigation into the incident. Skripal, a former military intelligence officer, was resettled in the English town of Salisbury in 2010, after spending several years in a Russian prison for spying for Britain. But he and his daughter Yulia almost died in March of this year, after being
The amount of poison smuggled into Britain for a near-fatal attack on Russian former spy Sergei Skripal was powerful enough to kill “thousands of people”, according those leading the investigation into the incident. Skripal, a former military intelligence officer, was resettled in the English town of Salisbury in 2010, after spending several years in a Russian prison for spying for Britain. But he and his daughter Yulia almost died in March of this year, after being  Norway’s supreme legislature body is considering a bill that would offer immunity from prosecution to intelligence officers and informants who are authorized by the country’s spy service to conduct espionage. The bill has been proposed on behalf of the Royal Norwegian Ministry of Defense, which supervises the operations of the Norwegian Intelligence Service (NIS), Norway’s primary intelligence agency. The NIS operates primarily abroad and is the only institution of the Norwegian state that can be authorized by the government to break laws in foreign countries. However, supporters of the new bill point out that NIS overseas operations can also break Norwegian law. That is something that the proposed bill addresses, they argue.
Norway’s supreme legislature body is considering a bill that would offer immunity from prosecution to intelligence officers and informants who are authorized by the country’s spy service to conduct espionage. The bill has been proposed on behalf of the Royal Norwegian Ministry of Defense, which supervises the operations of the Norwegian Intelligence Service (NIS), Norway’s primary intelligence agency. The NIS operates primarily abroad and is the only institution of the Norwegian state that can be authorized by the government to break laws in foreign countries. However, supporters of the new bill point out that NIS overseas operations can also break Norwegian law. That is something that the proposed bill addresses, they argue.






Russian spies ‘launched major cyber attack on Ukraine’ prior to naval incident
December 12, 2018 by Joseph Fitsanakis 1 Comment
But now a private cyber security firm has said that Moscow launched a series of cyber attacks on Ukrainian government servers, which were aimed at gathering intelligence that could be used for the ships’ capture. In a separate development, the European Union’s security commissioner has alleged that the Kremlin launched an elaborate “disinformation campaign” aiming to “soften up public opinion” before seizing the Ukrainian ships.
The American-based cyber security firm Stealthcare said this week that the cyber attacks were carried out by Carbanak and the Gamaredon Group, two hacker entities that are believed to be sponsored by the Russian intelligence services. The first wave of attacks, which occurred in October of this year, centered on a phishing campaign that targeted government agencies in Ukraine and other Eastern European countries. Victims of these attacks had “important functions” of their computers taken over by remote actors who stole and exfiltrated data, according to Stealthcare. Another attack installed back doors on computer servers belonging to Ukrainian government agencies in November, just days prior to the Kerch Strait crisis. The two attacks, said the company, provided the hackers with “information that would have been very […] relevant in planning” the November 25 naval crisis, said Stealthcare. The company added that there was “no doubt that this was a Kremlin-led reconnaissance effort to prepare for the Kerch Strait crisis”.
Meanwhile on Monday Julian King, a British diplomat who is currently the European Commissioner for the Security Union, said that Russia “paved the way for the Kerch Strait crisis” through a systematic fake news campaign that “lasted for more than a year”. The campaign, said King, included the use of social media to spread false rumors, such as claims that the Ukrainian government had infected the Black Sea with bacteria that cause cholera. Another report by Russian media allegedly claimed that Kiev had tried to secretly transport a nuclear device to Russian-annexed Crimea through the Kerch Strait. The EU security commissioner added that social media platforms and online search engines like Google had a responsibility “to identify and close down fake accounts that were spreading disinformation”.
► Author: Joseph Fitsanakis | Date: 12 December 2018 | Research credit: D.V. | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with 2018 Kerch Strait crisis, Carbanak, computer hacking, disinformation, Gamaredon Group, Julian King, News, psyops, Russia, Stealthcare, Ukraine