US politics in uncharted waters as FBI announces probe into Russian activities
March 21, 2017 2 Comments
 Monday’s official announcement that an investigation is underway into alleged Russian involvement in the 2016 United States presidential election was an important moment in American political history. It exposed the chaotic state of American politics and added yet another layer of complexity in an already intricate affair, from which the country’s institutions will find it difficult to recover for years to come. This is regardless of the outcome of the investigation, which is being conducted by the Federal Bureau of Investigation. Even if it fails to produce a ‘smoking gun’, the very fact that the country’s chief counterintelligence agency is examining the possibility that a US president was elected with help from Russia, is an astonishing development without parallel in modern American history.
Monday’s official announcement that an investigation is underway into alleged Russian involvement in the 2016 United States presidential election was an important moment in American political history. It exposed the chaotic state of American politics and added yet another layer of complexity in an already intricate affair, from which the country’s institutions will find it difficult to recover for years to come. This is regardless of the outcome of the investigation, which is being conducted by the Federal Bureau of Investigation. Even if it fails to produce a ‘smoking gun’, the very fact that the country’s chief counterintelligence agency is examining the possibility that a US president was elected with help from Russia, is an astonishing development without parallel in modern American history.
It is important to recognize that the FBI would never have initiated such a controversial and politically charged investigation without having concrete proof of Russia’s interference in last year’s presidential election. No agency of the US federal government would choose to dedicate enormous resources and personnel, and risk the political fallout that such a probe inevitably entails, without first having amassed indisputable evidence that necessitates it. Moreover, the FBI is not acting alone; its investigation almost certainly encompasses and incorporates similar probes carried out by other American security agencies, and possibly by agencies in allied countries, including the United Kingdom. It follows that the FBI investigation will undoubtedly confirm the existence of a systematic Russian intelligence operation that was aimed at influencing the outcome of last year’s American election.
As the present author has previously stated, it would be “extremely unusual and highly uncharacteristic of Russian spy agencies if they did not launch at least a rudimentary covert campaign to target the 2016 US presidential election […]. Indeed, the opposite would have been strange”. The central question, of course, is: what types of activities were part of the Kremlin’s covert campaign? Did it mostly involve the methodical production and dissemination of so-called ‘fake news’? Did it involve substantial funding of individual candidates or political parties? Or were there perhaps instances of extortion and blackmail of targeted individuals? These questions must be answered in full, and their inherent complexity explains fully why the FBI Director James Comey would not discuss details of the investigation on Monday.
Crucially, the FBI probe will have to answer conclusively the question of whether members of the administration of US President Donald Trump, or indeed the president himself, were implicated in the Kremlin’s actions. Did the president and his senior campaign team know that the Kremlin was —allegedly—assisting their efforts? If so, how did they know? And if not, did they deliberately ignore concrete warnings pointing to the contrary?
Every American, regardless of political persuasion, who genuinely cares about his or her nation’s political stability, hopes that the FBI probe finds no collusion between the Kremlin and the Trump campaign. However, there is an important sense in which, no matter the outcome of the investigation, serious damage has already been done. The reputation of American political institutions as a whole has been severely shaken, and mistrust between American civil society and its political institutions continues to rise exponentially. Meanwhile, it is safe to say that it will take months for the FBI’s probe to conclude. By then, the current chaotic state of American politics could be the a new permanently reality in Washington, a city that has witnessed much tumult in its history, though perhaps never as perplexing as the current crisis.
► Author: Joseph Fitsanakis | Date: 21 March 2017 | Permalink
 A Taiwanese government official has alleged that China maintains an army of more than 5,000 spies in Taiwan, many of whom have infiltrated the highest levels of government and industry. The allegation came after two sensational arrests were made in Taiwan last week, of people accused of spying for Beijing. Taiwanese counterintelligence officers reportedly arrested a bodyguard of Annette Lu, Taiwan’s former vice president. The bodyguard, who has been identified in Taiwanese media as Wang Hong-ju, has been charged with receiving payments from his Chinese intelligence handler in return for providing information about Mrs. Lu. This incident followed another arrest, made earlier in the week, this time of a Chinese man who is believed to have initially come to Taiwan as a student. Zhou Hong-xu is
A Taiwanese government official has alleged that China maintains an army of more than 5,000 spies in Taiwan, many of whom have infiltrated the highest levels of government and industry. The allegation came after two sensational arrests were made in Taiwan last week, of people accused of spying for Beijing. Taiwanese counterintelligence officers reportedly arrested a bodyguard of Annette Lu, Taiwan’s former vice president. The bodyguard, who has been identified in Taiwanese media as Wang Hong-ju, has been charged with receiving payments from his Chinese intelligence handler in return for providing information about Mrs. Lu. This incident followed another arrest, made earlier in the week, this time of a Chinese man who is believed to have initially come to Taiwan as a student. Zhou Hong-xu is  Russia may have become the latest country to deploy special forces soldiers in Libya, according to news reports citing anonymous United States officials. Late on Tuesday, the Reuters news agency
Russia may have become the latest country to deploy special forces soldiers in Libya, according to news reports citing anonymous United States officials. Late on Tuesday, the Reuters news agency  United States President Donald Trump has reportedly authorized the Central Intelligence Agency to bring back the routine use of lethal airstrikes by unmanned aerial vehicles (UAVs), which his predecessor, Barack Obama, curtailed in 2013. Washington began employing limited strikes by UAVs, otherwise known as drones, in the early 1990s, during the administration of President Bill Clinton. But it was under the Obama administration that the use of drone strikes reached an all-time high, with hundreds of such attacks documented after 2008. It is believed that Obama used this remote attack method to combat the Taliban and al-Qaeda, while at the same time keeping his promise of bringing back American troops from the Middle East and Central Asia. However, in 2013 the US president severely curtailed the controversial program, which some say damaged America’s image by inflicting civilian casualties.
United States President Donald Trump has reportedly authorized the Central Intelligence Agency to bring back the routine use of lethal airstrikes by unmanned aerial vehicles (UAVs), which his predecessor, Barack Obama, curtailed in 2013. Washington began employing limited strikes by UAVs, otherwise known as drones, in the early 1990s, during the administration of President Bill Clinton. But it was under the Obama administration that the use of drone strikes reached an all-time high, with hundreds of such attacks documented after 2008. It is believed that Obama used this remote attack method to combat the Taliban and al-Qaeda, while at the same time keeping his promise of bringing back American troops from the Middle East and Central Asia. However, in 2013 the US president severely curtailed the controversial program, which some say damaged America’s image by inflicting civilian casualties. Boris Johnson, the British foreign secretary has said in an interview that Russian spies may have orchestrated last year’s failed attempt to kill the then-prime minister of Montenegro, Milo Dukanović. Mr. Johnson, a senior figure in the Conservative Party of the United Kingdom, was a major contender for the prime minister’s position in 2016, after the administration of David Cameron collapsed under the weight of the Brexit vote result. Speaking on Sunday morning to reporter Robert Peston, of Britain’s ITV television network, Mr. Johnson said that the West should “engage” with Russia, but warned that it should also “beware” of Moscow’s “dirty tricks” in Europe and the United States.
Boris Johnson, the British foreign secretary has said in an interview that Russian spies may have orchestrated last year’s failed attempt to kill the then-prime minister of Montenegro, Milo Dukanović. Mr. Johnson, a senior figure in the Conservative Party of the United Kingdom, was a major contender for the prime minister’s position in 2016, after the administration of David Cameron collapsed under the weight of the Brexit vote result. Speaking on Sunday morning to reporter Robert Peston, of Britain’s ITV television network, Mr. Johnson said that the West should “engage” with Russia, but warned that it should also “beware” of Moscow’s “dirty tricks” in Europe and the United States. The leader of the Islamic State has abandoned the city of Mosul and is hiding in the desert zone of western Iraq, according to intelligence sources. Meanwhile Mosul, once the most populous city under the Islamic State’s control, is now reportedly being defended by a diminishing cadre of fewer than 3,000 Sunni militants, who are facing a 110,000-strong invading army.
The leader of the Islamic State has abandoned the city of Mosul and is hiding in the desert zone of western Iraq, according to intelligence sources. Meanwhile Mosul, once the most populous city under the Islamic State’s control, is now reportedly being defended by a diminishing cadre of fewer than 3,000 Sunni militants, who are facing a 110,000-strong invading army. The United States federal government has launched a criminal investigation into the public disclosure of thousands of documents that purportedly belong to the Central Intelligence Agency. The documents were
The United States federal government has launched a criminal investigation into the public disclosure of thousands of documents that purportedly belong to the Central Intelligence Agency. The documents were  Thousands of documents belonging to the United States Central Intelligence Agency, which were released on Tuesday by the international anti-secrecy website WikiLeaks, are almost certainly genuine. They reveal an entire universe of technical intelligence collection methods used by the CIA to extract information from digital applications and electronic devices, ranging from flash drives to smart screen televisions. WikiLeaks named the collection
Thousands of documents belonging to the United States Central Intelligence Agency, which were released on Tuesday by the international anti-secrecy website WikiLeaks, are almost certainly genuine. They reveal an entire universe of technical intelligence collection methods used by the CIA to extract information from digital applications and electronic devices, ranging from flash drives to smart screen televisions. WikiLeaks named the collection  The sensational assassination of Kim Jong-nam, half-brother of North Korea’s Supreme Leader Kim Jong-un, on February 13, revealed much about the current operational mindset of Pyongyang. But it also brought to light the shady network of front companies set up by the North Korean regime to facilitate the country’s illicit financial activities around the world. This extensive network permits Pyongyang to evade international sanctions against it, and to coordinate the activities of hundreds of clandestine operatives around the world. Through these activities, the reclusive country has been able to develop its weapons of mass destruction program unabated, despite concerted efforts by the United Nations to prevent it from doing so.
The sensational assassination of Kim Jong-nam, half-brother of North Korea’s Supreme Leader Kim Jong-un, on February 13, revealed much about the current operational mindset of Pyongyang. But it also brought to light the shady network of front companies set up by the North Korean regime to facilitate the country’s illicit financial activities around the world. This extensive network permits Pyongyang to evade international sanctions against it, and to coordinate the activities of hundreds of clandestine operatives around the world. Through these activities, the reclusive country has been able to develop its weapons of mass destruction program unabated, despite concerted efforts by the United Nations to prevent it from doing so.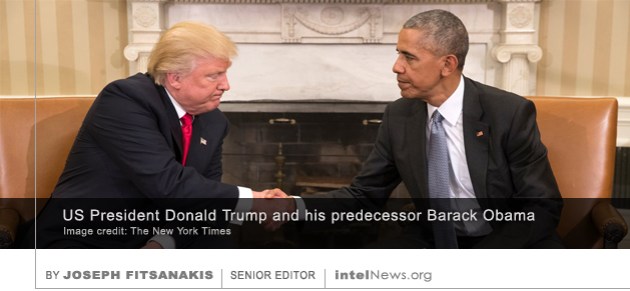 The absurdity of American politics reached new heights over the weekend, as President Donald Trump dramatically alleged on Twitter that his predecessor, Barack Obama, wiretapped his telephones last year. Even for a highly impulsive public figure known for his sensational and often-unsubstantiated allegations, Mr. Trump’s latest claims prompted a new sense of abnormality and astonishment in Washington. If the president is unable to prove his dramatic claims, his reliability will be further-eroded, and what little is left of his relationship with the American intelligence and national-security communities will disintegrate. If his allegations are proven, they will cause a scandal of unprecedented proportions from which American political institutions —including the presidency— will find it difficult to recover.
The absurdity of American politics reached new heights over the weekend, as President Donald Trump dramatically alleged on Twitter that his predecessor, Barack Obama, wiretapped his telephones last year. Even for a highly impulsive public figure known for his sensational and often-unsubstantiated allegations, Mr. Trump’s latest claims prompted a new sense of abnormality and astonishment in Washington. If the president is unable to prove his dramatic claims, his reliability will be further-eroded, and what little is left of his relationship with the American intelligence and national-security communities will disintegrate. If his allegations are proven, they will cause a scandal of unprecedented proportions from which American political institutions —including the presidency— will find it difficult to recover. order at the highest levels of the American government, Mr. Trump’s claims cannot possibly be true. American presidents have not been legally allowed to order wiretaps since 1978, when the Foreign Intelligence Surveillance Act (FISA) was established. Prompted by the abuse of executive power revealed through the Watergate scandal, FISA forces government agencies to seek the approval of specially mandated judges before installing wiretaps. If an agency like the Federal Bureau of Investigation (FBI) wants to wiretap an individual or group suspected of acting as agents of a foreign power, it must convince one of 11 federal district judges who rotate on the FISA court that the case warrants a wiretap order. Thus, before authorizing the wiretap, a FISA judge must be convinced by examining the available evidence presented before him or her.
order at the highest levels of the American government, Mr. Trump’s claims cannot possibly be true. American presidents have not been legally allowed to order wiretaps since 1978, when the Foreign Intelligence Surveillance Act (FISA) was established. Prompted by the abuse of executive power revealed through the Watergate scandal, FISA forces government agencies to seek the approval of specially mandated judges before installing wiretaps. If an agency like the Federal Bureau of Investigation (FBI) wants to wiretap an individual or group suspected of acting as agents of a foreign power, it must convince one of 11 federal district judges who rotate on the FISA court that the case warrants a wiretap order. Thus, before authorizing the wiretap, a FISA judge must be convinced by examining the available evidence presented before him or her. Britain’s primary external-intelligence agency will revert to old-fashioned ways of recruiting employees, including the co-called “tap on the shoulder” method, according to its director. Known informally as MI6, the Secret Intelligence Service (SIS) was founded in 1908 to protect Britain’s national security by collecting intelligence from foreign sources. However, the agency has had difficulty recruiting a diverse group of people, and many still view it as a professional destination for a small wealthy elite, drawn primarily from Britain’s most prestigious universities such as Oxford and Cambridge.
Britain’s primary external-intelligence agency will revert to old-fashioned ways of recruiting employees, including the co-called “tap on the shoulder” method, according to its director. Known informally as MI6, the Secret Intelligence Service (SIS) was founded in 1908 to protect Britain’s national security by collecting intelligence from foreign sources. However, the agency has had difficulty recruiting a diverse group of people, and many still view it as a professional destination for a small wealthy elite, drawn primarily from Britain’s most prestigious universities such as Oxford and Cambridge. The Islamic State is facing imminent financial collapse, according to a new study conducted by a London-based research group in association with one of the world’s leading international accounting firms. The recently launched report is entitled
The Islamic State is facing imminent financial collapse, according to a new study conducted by a London-based research group in association with one of the world’s leading international accounting firms. The recently launched report is entitled  For a very long time, the field of Intelligence Studies has been dominated by analysis of the Five Eyes community, which is comprised of the United States, Great Britain, Australia, New Zealand, and Canada. In reality, that study is more often the study of intelligence in the US and the UK. While not entirely fair to characterize this as Western prejudice —access to data is better in these two countries and intelligence scholars and analysts for the most part do not fear retribution or reprisal— more voices need to come forward to consider intelligence and its role on societies beyond the Five Eyes.
For a very long time, the field of Intelligence Studies has been dominated by analysis of the Five Eyes community, which is comprised of the United States, Great Britain, Australia, New Zealand, and Canada. In reality, that study is more often the study of intelligence in the US and the UK. While not entirely fair to characterize this as Western prejudice —access to data is better in these two countries and intelligence scholars and analysts for the most part do not fear retribution or reprisal— more voices need to come forward to consider intelligence and its role on societies beyond the Five Eyes. electoral reforms back in April of 2016. The protests were geared to influencing the December 2016 presidential election, which ultimately saw the defeat of incumbent President/Strongman Yahya Jammeh to Adama Barrow. Jammeh had corruptly governed the country since rising to power as a young military officer in a bloodless military coup in 1994.
electoral reforms back in April of 2016. The protests were geared to influencing the December 2016 presidential election, which ultimately saw the defeat of incumbent President/Strongman Yahya Jammeh to Adama Barrow. Jammeh had corruptly governed the country since rising to power as a young military officer in a bloodless military coup in 1994. The military intelligence service of Sweden warned last week that there were increasing incidents of espionage perpetrated against Sweden by operatives identified “beyond doubt” as agents of foreign powers. In its
The military intelligence service of Sweden warned last week that there were increasing incidents of espionage perpetrated against Sweden by operatives identified “beyond doubt” as agents of foreign powers. In its 






Israel’s chief of staff says Hezbollah killed its own commander in Syria
March 22, 2017 by Joseph Fitsanakis Leave a comment
Soon after the outbreak of the Syrian Civil War, the leadership of Hezbollah dispatched Badreddine to the Syrian capital Damascus. His stated mission was to command thousands of Hezbollah troops, who fought under Iranian guidance in support of the Syrian President Bashar al-Assad. But on May 13, 2016, Badreddine was reportedly killed in Damascus, causing observers to describe his death as the biggest setback for the Shiite militant group since the 2008 assassination of its leading commander, Imad Mughniyeh. Initial reports in Hezbollah-controlled Lebanese media suggested that Badreddine might have been killed in an Israeli air attack. But a press statement issued later by Hezbollah said the commander had been killed as a result of an armed attack by Sunni rebels. However, on March 8 of this year, the Saudi-owned pan-Arab television network al-Arabiya said it had conducted its own investigation into Badreddine’s death, and had concluded that he was killed by Hezbollah itself. The network claimed that Hezbollah’s Secretary General Nasrallah had ordered Badreddine’s killing, after the Iranians demanded it. Apparently the Iranians wanted him killed because he disputed the authority of Major General Qasem Soleimani, commander of Iran’s Revolutionary Guard Corps, who is often credited with having saved the Syrian government from demise during the Civil War.
The claim that Badreddine was killed by Hezbollah was echoed on Tuesday by Lieutenant General Gadi Eisenkot, Chief of the General Staff of the Israel Defense Forces. Speaking to the Associated Press, Lt Gen Eisenkot said that reports from Arab media that Badreddine was killed by his own forces agreed “with intelligence we have”, referring to the Israeli military. It is worth noting that Israeli officials rarely comment on intelligence operations, including assassination operations, choosing instead to adhere to a “refuse to confirm or deny” policy.
► Author: Joseph Fitsanakis | Date: 22 March 2017 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with Gadi Eisenkot, Iran, Israel, Lebanon, Mustafa Amine Badreddine, News, suspicious deaths, Syria, Syrian Civil War