Taiwan admits for the first time that Chinese general Liu Liankun was one of its spies
April 6, 2018 Leave a comment
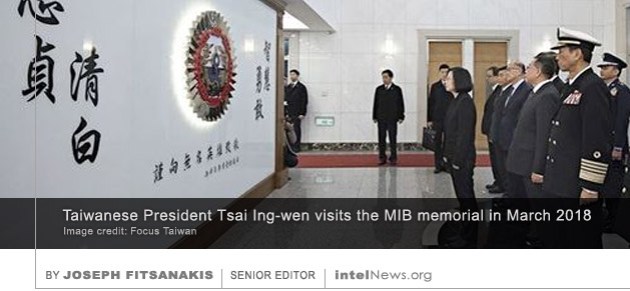 The government of Taiwan has acknowledged publicly for the first time that a Chinese major general, who was executed by Beijing in 1999 for espionage, was indeed one of its spies. The military officer was Liu Liankun, a logistician for the Chinese People’s Liberation Army, who headed its Department of General Logistics. However, China arrested Liu for espionage in 1999, and accused him of having spied for Taiwan for five years, in exchange for money. At the time, Taiwan denied that Liu spied on its behalf and refused to acknowledge that it had any role in the major general’s alleged espionage activities.
The government of Taiwan has acknowledged publicly for the first time that a Chinese major general, who was executed by Beijing in 1999 for espionage, was indeed one of its spies. The military officer was Liu Liankun, a logistician for the Chinese People’s Liberation Army, who headed its Department of General Logistics. However, China arrested Liu for espionage in 1999, and accused him of having spied for Taiwan for five years, in exchange for money. At the time, Taiwan denied that Liu spied on its behalf and refused to acknowledge that it had any role in the major general’s alleged espionage activities.
According to his Chinese government accusers, Liu passed information to Taiwan during the so-called 1996 missile crisis —known in Taiwan as the 1996 Taiwan Strait crisis. The crisis was prompted by a series of missile tests conducted by Beijing in the waters around the island of Taiwan. The crisis lasted several months, from July of 1995 to March of 1996. Many in Taiwan were convinced that China’s missile tests were the precursors of a military advance by Beijing, aimed at conquering the island one and for all. However, Taiwan’s Ministry of Defense eventually issued a press statement saying it was aware that the Chinese missiles were not equipped with armed warheads. The information was correct, but it made China realize that Taiwan was receiving information from a highly placed source inside its military. After an extensive counterintelligence investigation, the Chinese arrested Liu and accused him of having spied for Taiwan in exchange for nearly $2 million in bribes. Liu was eventually executed by lethal injection in a Beijing prison. He was 58. At the time of his conviction, Liu was the most senior Chinese military officer to have ever been convicted of spying for Taiwan.
But Taiwan continued to deny any involvement in Liu’s case. That changed last week, however, when Taiwan’s Military Information Bureau unveiled its renovated memorial, which is housed at its headquarters in Taipei City. The memorial features plaques commemorating 75 individuals who have died while carrying out MIB intelligence operations. Those featured include both intelligence officers and their assets —foreign people recruited by intelligence officers to spy for Taiwan. Among the plaques, visitors to the memorial saw one dedicated to Liu for the first time. A note beneath the plaque acknowledges Liu’s contributions during the 1996 missile crisis. But it also states that the Chinese military official also provided assistance to Taiwan during earlier crises with China in the 1990s, as well as inside information about the death of Chinese Premier Deng Xiaoping in 1997.
► Author: Joseph Fitsanakis | Date: 6 April 2018 | Permalink
 Chinese spies hacked the computer servers of the African Union headquarters in the Ethiopian capital Addis Ababa, which the Chinese government funded and built as a gift to the organization, a French newspaper has claimed. Beijing donated $200 million toward the project and hired the state-owned China State Construction Engineering Corporation to build the tower, which was
Chinese spies hacked the computer servers of the African Union headquarters in the Ethiopian capital Addis Ababa, which the Chinese government funded and built as a gift to the organization, a French newspaper has claimed. Beijing donated $200 million toward the project and hired the state-owned China State Construction Engineering Corporation to build the tower, which was  A former case officer in the Central Intelligence Agency, who was arrested this week for violating the United States Espionage Act, was lured back to America from Hong Kong at least once by counterintelligence investigators, according to reports. Jerry Chun Shing Lee, 53, served in the CIA from 1994 to 2007. He was
A former case officer in the Central Intelligence Agency, who was arrested this week for violating the United States Espionage Act, was lured back to America from Hong Kong at least once by counterintelligence investigators, according to reports. Jerry Chun Shing Lee, 53, served in the CIA from 1994 to 2007. He was  A former operations officer in the United States Central Intelligence Agency has been arrested on charges of illegally possessing top secret information, including lists of real names of foreign assets and addresses of CIA safe houses. The news emerged on Tuesday, as the US Department of Justice announced that the Federal Bureau of Investigation had filed a criminal complaint over the weekend. The complaint identifies the former case officer as Jerry Chun Shing Lee, also known as Zhen Cheng Li. Lee, a 53-year-old naturalized American, served in the CIA from 1994 to 2007 “in various overseas positions and locations”, according to court documents. Lee has
A former operations officer in the United States Central Intelligence Agency has been arrested on charges of illegally possessing top secret information, including lists of real names of foreign assets and addresses of CIA safe houses. The news emerged on Tuesday, as the US Department of Justice announced that the Federal Bureau of Investigation had filed a criminal complaint over the weekend. The complaint identifies the former case officer as Jerry Chun Shing Lee, also known as Zhen Cheng Li. Lee, a 53-year-old naturalized American, served in the CIA from 1994 to 2007 “in various overseas positions and locations”, according to court documents. Lee has  A North Korean nuclear scientist who defected to China but was involuntarily sent back to North Korea in November reportedly killed himself in his North Korean cell hours before he was due to be interrogated. Information about the scientist’s alleged suicide was issued on Thursday by Radio Free Asia (RFA), a multilingual news service based in Washington, DC, which is funded by the United States government. The service said its reporters spoke to an anonymous source in North Hamgyong province, North Korea’s northernmost region that borders China. The source identified the late scientist as Hyun Cheol Huh, but cautioned that this may not be his real name, because the North Korean security services are known to “use […] fake names when referring to important persons” in their custody.
A North Korean nuclear scientist who defected to China but was involuntarily sent back to North Korea in November reportedly killed himself in his North Korean cell hours before he was due to be interrogated. Information about the scientist’s alleged suicide was issued on Thursday by Radio Free Asia (RFA), a multilingual news service based in Washington, DC, which is funded by the United States government. The service said its reporters spoke to an anonymous source in North Hamgyong province, North Korea’s northernmost region that borders China. The source identified the late scientist as Hyun Cheol Huh, but cautioned that this may not be his real name, because the North Korean security services are known to “use […] fake names when referring to important persons” in their custody. In an unusual step, German intelligence officials have issued a public warning about what they said are thousands of fake LinkedIn profiles created by Chinese spies to gather information about Western targets. On Sunday, Germany’s Federal Office for the Protection of the Constitution (BfV) held a press conference in which it said that it had discovered a wide-ranging effort by spy agencies in China to establish links with Westerners. The agency said that it undertook a 9-month investigation, during which it identified 10,000 German citizens who were contacted by Chinese spy-run fake profiles on LinkedIn. Across Europe, the number of targets could be in the hundreds of thousands,
In an unusual step, German intelligence officials have issued a public warning about what they said are thousands of fake LinkedIn profiles created by Chinese spies to gather information about Western targets. On Sunday, Germany’s Federal Office for the Protection of the Constitution (BfV) held a press conference in which it said that it had discovered a wide-ranging effort by spy agencies in China to establish links with Westerners. The agency said that it undertook a 9-month investigation, during which it identified 10,000 German citizens who were contacted by Chinese spy-run fake profiles on LinkedIn. Across Europe, the number of targets could be in the hundreds of thousands,  A senior Chinese People’s Liberation Army (PLA) military official, who was seen as a close ally of President Xi Jinping, has allegedly committed suicide, according to Chinese state media. Zhang Yang was one of the most high-profile generals in the Chinese PLA. His rise to power after Xi became president of China was meteoric. He was appointed member of the Central Military Commission (CMC) of the Communist Party of China, which exercises political supervision of the Chinese armed forces. In addition to his role in the CMC, Zhang directed the General Political Department of the PLA’s Ground Force, which made him the top political commissar in the army.
A senior Chinese People’s Liberation Army (PLA) military official, who was seen as a close ally of President Xi Jinping, has allegedly committed suicide, according to Chinese state media. Zhang Yang was one of the most high-profile generals in the Chinese PLA. His rise to power after Xi became president of China was meteoric. He was appointed member of the Central Military Commission (CMC) of the Communist Party of China, which exercises political supervision of the Chinese armed forces. In addition to his role in the CMC, Zhang directed the General Political Department of the PLA’s Ground Force, which made him the top political commissar in the army. An American diplomat stationed in China was abducted and interrogated for several hours by Chinese authorities, who believed him to be an officer of the Central Intelligence Agency working under official cover. The alleged abduction took place in early 2016 but was revealed this week by the online news outlet Politico. The website said that the diplomat, who has not been named, was stationed at the United States consulate general in Chengdu, a city of 14 million that is the administrative capital of western China’s Sichuan province. Founded in 1985, the US consulate in Chengdu is one of Washington’s seven diplomatic and consular posts in China. It is staffed by 130 people, approximately 30 of whom are Americans and 100 are locally hired Chinese citizens. The facility’s consular district includes several Chinese provinces, including the politically sensitive Tibet Autonomous Region.
An American diplomat stationed in China was abducted and interrogated for several hours by Chinese authorities, who believed him to be an officer of the Central Intelligence Agency working under official cover. The alleged abduction took place in early 2016 but was revealed this week by the online news outlet Politico. The website said that the diplomat, who has not been named, was stationed at the United States consulate general in Chengdu, a city of 14 million that is the administrative capital of western China’s Sichuan province. Founded in 1985, the US consulate in Chengdu is one of Washington’s seven diplomatic and consular posts in China. It is staffed by 130 people, approximately 30 of whom are Americans and 100 are locally hired Chinese citizens. The facility’s consular district includes several Chinese provinces, including the politically sensitive Tibet Autonomous Region. The Parliament of Australia is reportedly reviewing the use of cell phones built by a Chinese manufacturer, after an Australian news agency expressed concerns about the manufacturer’s links with the Chinese military. The cell phone in question is the popular Telstra Tough T55 handset. It is made available to Australian parliamentarians though the Information, Communications and Technology (ICT) unit of the Department of Parliamentary Services (DST). Any parliamentarian or worker in Australia’s Parliament House can order the device through the Parliament’s ICT website. According to data provided by the DST, 90 Telstra Tough T55 cell phones have been ordered through the ICT in the current financial year.
The Parliament of Australia is reportedly reviewing the use of cell phones built by a Chinese manufacturer, after an Australian news agency expressed concerns about the manufacturer’s links with the Chinese military. The cell phone in question is the popular Telstra Tough T55 handset. It is made available to Australian parliamentarians though the Information, Communications and Technology (ICT) unit of the Department of Parliamentary Services (DST). Any parliamentarian or worker in Australia’s Parliament House can order the device through the Parliament’s ICT website. According to data provided by the DST, 90 Telstra Tough T55 cell phones have been ordered through the ICT in the current financial year. Australia has expressed concern about a plan by a Chinese telecommunications company to provide high-speed Internet to the Solomon Islands, a small Pacific island nation with which Australia shares Internet resources. The company, Huawei Technologies, a private Chinese venture, is one of the world’s leading telecommunications hardware manufacturers. In recent years, however, it has come under scrutiny by Western intelligence agencies, who view it as being too close to the Communist Party of China.
Australia has expressed concern about a plan by a Chinese telecommunications company to provide high-speed Internet to the Solomon Islands, a small Pacific island nation with which Australia shares Internet resources. The company, Huawei Technologies, a private Chinese venture, is one of the world’s leading telecommunications hardware manufacturers. In recent years, however, it has come under scrutiny by Western intelligence agencies, who view it as being too close to the Communist Party of China. A new report authored by a consortium of government and private organizations in Britain has revealed the existence of a computer hacking operation, allegedly based in China, that is said to be “one of the largest ever” such campaigns globally. The operation is believed to have compromised sensitive information from an inestimable number of private companies in Southeast Asia, Europe and the United States. The
A new report authored by a consortium of government and private organizations in Britain has revealed the existence of a computer hacking operation, allegedly based in China, that is said to be “one of the largest ever” such campaigns globally. The operation is believed to have compromised sensitive information from an inestimable number of private companies in Southeast Asia, Europe and the United States. The  An employee of the United States Department of State has been charged with lying to authorities about her contacts with Chinese intelligence operatives, who gave her money and gifts in return for information. Candace Claiborne, 60, joined the Department of State in 1999 as an office management specialist. She lives in Washington, DC, but has served overseas in American diplomatic facilities in Baghdad, Iraq, Khartoum, Sudan, and China, where she was stationed in Beijing and Shanghai. According to information provided by the Federal Bureau of Investigation, Claiborne had a top security clearance, which required her to report contacts with foreign nationals.
An employee of the United States Department of State has been charged with lying to authorities about her contacts with Chinese intelligence operatives, who gave her money and gifts in return for information. Candace Claiborne, 60, joined the Department of State in 1999 as an office management specialist. She lives in Washington, DC, but has served overseas in American diplomatic facilities in Baghdad, Iraq, Khartoum, Sudan, and China, where she was stationed in Beijing and Shanghai. According to information provided by the Federal Bureau of Investigation, Claiborne had a top security clearance, which required her to report contacts with foreign nationals. A Taiwanese government official has alleged that China maintains an army of more than 5,000 spies in Taiwan, many of whom have infiltrated the highest levels of government and industry. The allegation came after two sensational arrests were made in Taiwan last week, of people accused of spying for Beijing. Taiwanese counterintelligence officers reportedly arrested a bodyguard of Annette Lu, Taiwan’s former vice president. The bodyguard, who has been identified in Taiwanese media as Wang Hong-ju, has been charged with receiving payments from his Chinese intelligence handler in return for providing information about Mrs. Lu. This incident followed another arrest, made earlier in the week, this time of a Chinese man who is believed to have initially come to Taiwan as a student. Zhou Hong-xu is
A Taiwanese government official has alleged that China maintains an army of more than 5,000 spies in Taiwan, many of whom have infiltrated the highest levels of government and industry. The allegation came after two sensational arrests were made in Taiwan last week, of people accused of spying for Beijing. Taiwanese counterintelligence officers reportedly arrested a bodyguard of Annette Lu, Taiwan’s former vice president. The bodyguard, who has been identified in Taiwanese media as Wang Hong-ju, has been charged with receiving payments from his Chinese intelligence handler in return for providing information about Mrs. Lu. This incident followed another arrest, made earlier in the week, this time of a Chinese man who is believed to have initially come to Taiwan as a student. Zhou Hong-xu is 






German spy chief warns against Chinese investment in German hi-tech firms
April 12, 2018 by Joseph Fitsanakis 2 Comments
The purpose of these takeovers was “to gain access to German technical know-how”, added Maassen. He went on to say that “industrial cyberespionage is no longer needed if an actor can simply exploit liberal economic regulations to buy companies, and then proceed to disembowel them, essentially cannibalize them, to gain access to their know-how”. The spy chief noted that Germany did not object to foreign investment and the free flow of capital from all countries, including China. However, he added, “certain direct investments in specific technologies can compromise domestic security”. Maassen mentioned several examples in his presentation, including the takeover of Kuka, a German robotics firm, by a Chinese investor in 2016. He said that in the past few months alone, Chinese companies have attempted to purchase stakes in 50Hertz, a German energy grid operator, German car manufacturer Daimler, and Cotesa, a German aerospace contractor.
In response to a question from a journalist about policy coordination between Germany and the European Union, Maassen said that Germany, France and Italy have been pressuring Brussels to update and modernize its screening procedures against foreign takeovers of companies that are involved in manufacturing and selling “sensitive technologies”. He noted that a new EU-wide screening mechanism should be in place by the end of 2018.
► Author: Joseph Fitsanakis | Date: 12 April 2018 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with China, counterintelligence, cyberespionage, economic espionage, Federal Office for the Protection of the Constitution (Germany), Germany, Hans-Georg Maassen, News