European Union states begin requiring advance transit notices from Russian diplomats
February 2, 2026 2 Comments
 AT LEAST THREE EUROPEAN Union members states now require Russian diplomats who are not accredited in their territories to notify them prior to entering their borders. According to the new requirement, Russian diplomats must provide advance notification if they intend to travel to, or transit through, a European Union country in which they are not accredited.
AT LEAST THREE EUROPEAN Union members states now require Russian diplomats who are not accredited in their territories to notify them prior to entering their borders. According to the new requirement, Russian diplomats must provide advance notification if they intend to travel to, or transit through, a European Union country in which they are not accredited.
For instance, a Russian diplomat accredited in Germany and stationed at the Russian embassy in Berlin, must provide France with advance notice if they intend to travel there or transit through French territory en route to a third destination. The new rule was first reported late last month by Russia’s state-affiliated RIA Novosti news agency and picked up by the investigative news site The Insider.
Citing Russian diplomatic sources, RIA Novosti said three European Union states, Austria, France, and the Netherlands, had contacted the Russian Ministry of Foreign Affairs with information about the new requirement. The Insider said last week it was unclear whether other European Union states had already issued similar restrictions against Russian diplomats.
The measure is included in the 19th Package of Sanctions against Russia, which the European Union adopted in October 2025. The text of the sanctions package includes “an obligation for Russian diplomats, travelling across the EU beyond their country of accreditation, to inform the relevant EU Member State in advance”. It also notes that the measure is “meant to tackle the increasingly hostile intelligence activities that support Russia’s aggression against Ukraine”.
► Author: Joseph Fitsanakis | Date: 02 February 2026 | Permalink
 INTELLIGENCE PARTNERS IN THE North Atlantic Treaty Organization (NATO) are “not talking openly” anymore, while authorities in Denmark have advised government officials to disable Bluetooth functions on their devices due to spying concerns. According to reports in British news outlets, intelligence-sharing functions inside NATO are at a breaking point following a series of actions by the United States that one source
INTELLIGENCE PARTNERS IN THE North Atlantic Treaty Organization (NATO) are “not talking openly” anymore, while authorities in Denmark have advised government officials to disable Bluetooth functions on their devices due to spying concerns. According to reports in British news outlets, intelligence-sharing functions inside NATO are at a breaking point following a series of actions by the United States that one source  EARLIER THIS MONTH, FRANCE-based British reporter Chris Bockman was given rare access to a training course designed collaboratively by a leading French university and France’s intelligence services. The course is part of the Diplôme sur le Renseignement et les Menaces Globales (Diploma of Intelligence and Global Threats), which is offered by the Institut d’études politiques de Saint-Germain-en-Laye (known as Sciences Po Saint-Germain), located on the northwestern outskirts of Paris.
EARLIER THIS MONTH, FRANCE-based British reporter Chris Bockman was given rare access to a training course designed collaboratively by a leading French university and France’s intelligence services. The course is part of the Diplôme sur le Renseignement et les Menaces Globales (Diploma of Intelligence and Global Threats), which is offered by the Institut d’études politiques de Saint-Germain-en-Laye (known as Sciences Po Saint-Germain), located on the northwestern outskirts of Paris. A FORMER DEEP COVER Russian intelligence officer, whose cover was blown in 2010 when he was arrested in the United States, is spearheading efforts by the Kremlin to secure investments by India’s technology sector. The spy, Andrei Bezrukov, was recruited by the Soviet Committee for State Security (KGB) in the late 1970s or early 1980s—most likely alongside his wife, Elena Vavilova. For several years, the married couple lived in several countries, including Canada and France, before arriving in the United States in 1999 using fraudulently obtained Canadian passports.
A FORMER DEEP COVER Russian intelligence officer, whose cover was blown in 2010 when he was arrested in the United States, is spearheading efforts by the Kremlin to secure investments by India’s technology sector. The spy, Andrei Bezrukov, was recruited by the Soviet Committee for State Security (KGB) in the late 1970s or early 1980s—most likely alongside his wife, Elena Vavilova. For several years, the married couple lived in several countries, including Canada and France, before arriving in the United States in 1999 using fraudulently obtained Canadian passports. IN A RARE MEDIA interview, the chief of Colombia’s National Intelligence Directorate (DNI) has said that his agency’s collaboration with the Central Intelligence Agency (CIA) and other American spy organizations continues unabated. This statement appears to contradict a prior statement by the president of Colombia, who said his country had stopped all intelligence-sharing with the United States in protest against the lethal targeting of civilian vessels in the Caribbean.
IN A RARE MEDIA interview, the chief of Colombia’s National Intelligence Directorate (DNI) has said that his agency’s collaboration with the Central Intelligence Agency (CIA) and other American spy organizations continues unabated. This statement appears to contradict a prior statement by the president of Colombia, who said his country had stopped all intelligence-sharing with the United States in protest against the lethal targeting of civilian vessels in the Caribbean. A BRITISH MAN WANTED by American authorities for spying for China, who disappeared along with his Chinese handler while under house arrest, may have managed to escape to China using a private jet, a report claims. John Miller, 63, from Tunbridge Wells in the United Kingdom, was arrested alongside his alleged Chinese handler, Cui Guanghai, in April of this year.
A BRITISH MAN WANTED by American authorities for spying for China, who disappeared along with his Chinese handler while under house arrest, may have managed to escape to China using a private jet, a report claims. John Miller, 63, from Tunbridge Wells in the United Kingdom, was arrested alongside his alleged Chinese handler, Cui Guanghai, in April of this year. THE MOSSAD, ISRAEL’S PRIMARY covert action agency, had “some 100 agents” on the ground in Iran at the start of the Twelve-Day War, according to senior Israeli government officials who participated in a television documentary. The
THE MOSSAD, ISRAEL’S PRIMARY covert action agency, had “some 100 agents” on the ground in Iran at the start of the Twelve-Day War, according to senior Israeli government officials who participated in a television documentary. The  PROSECUTORS IN VIENNA HAVE charged a former intelligence officer with spying for Russia in a high-profile case that has had broad political ramifications in Austria and abroad. The criminal case centers on Egisto Ott, a former employee of Austria’s Federal Office for the Protection of the Constitution and Counterterrorism (BVT). The BVT operated as Austria’s primary domestic intelligence agency from 2002 until its dissolution in 2021.
PROSECUTORS IN VIENNA HAVE charged a former intelligence officer with spying for Russia in a high-profile case that has had broad political ramifications in Austria and abroad. The criminal case centers on Egisto Ott, a former employee of Austria’s Federal Office for the Protection of the Constitution and Counterterrorism (BVT). The BVT operated as Austria’s primary domestic intelligence agency from 2002 until its dissolution in 2021. A DISAFFECTED SOLDIER, WHO tried to commit espionage against New Zealand for a foreign government, has become the first convicted spy in the Pacific Island nation’s history. The only other time New Zealand prosecuted an individual for espionage was in 1974, when the government accused
A DISAFFECTED SOLDIER, WHO tried to commit espionage against New Zealand for a foreign government, has become the first convicted spy in the Pacific Island nation’s history. The only other time New Zealand prosecuted an individual for espionage was in 1974, when the government accused  A HACKER GROUP LINKED to Russia’s Federal Security Service (FSB) has compromised Russia’s domestic internet infrastructure and is using it to target foreign diplomats stationed in Russia. According to a
A HACKER GROUP LINKED to Russia’s Federal Security Service (FSB) has compromised Russia’s domestic internet infrastructure and is using it to target foreign diplomats stationed in Russia. According to a  A GROUP OF RESEARCHERS in Finland have managed to outline the structure and geographic footprint of a highly secretive Russian signals intelligence (SIGINT) unit by studying commemorative badges issued by the Russian government. The research group, known as
A GROUP OF RESEARCHERS in Finland have managed to outline the structure and geographic footprint of a highly secretive Russian signals intelligence (SIGINT) unit by studying commemorative badges issued by the Russian government. The research group, known as 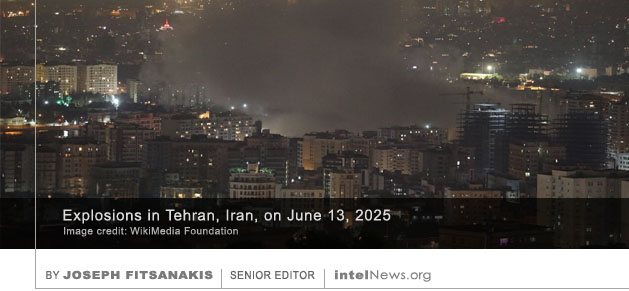 THE MOSSAD, ISRAEL’S PRIMARY external intelligence agency, had set up forward-operating bases deep inside Iranian territory several years prior to last week’s attacks, which targeted Iran’s military and nuclear infrastructure. In some cases, Mossad operatives, including commando forces, were operating inside the vicinity of the Iranian capital Tehran for months prior to June 13, according to Israeli media outlets.
THE MOSSAD, ISRAEL’S PRIMARY external intelligence agency, had set up forward-operating bases deep inside Iranian territory several years prior to last week’s attacks, which targeted Iran’s military and nuclear infrastructure. In some cases, Mossad operatives, including commando forces, were operating inside the vicinity of the Iranian capital Tehran for months prior to June 13, according to Israeli media outlets. TWO RUSSIAN SPIES USED forged documents acquired in Brazil in order to live in Portugal for years and use it as a base from where to conduct espionage, according to an investigation by Portuguese counterintelligence. The spies were husband-and-wife team Vladimir Aleksandrovich Danilov and Yekaterina Leonidovna Danilova, both in their 30s.
TWO RUSSIAN SPIES USED forged documents acquired in Brazil in order to live in Portugal for years and use it as a base from where to conduct espionage, according to an investigation by Portuguese counterintelligence. The spies were husband-and-wife team Vladimir Aleksandrovich Danilov and Yekaterina Leonidovna Danilova, both in their 30s. 






France arrests alleged Chinese spies living in small village—four arrests so far
February 11, 2026 6 Comments
Two of the arrests took place on-site at a property in Camblanes-et-Meynac, a picturesque village located around 10 miles from Bordeaux in south-western France’s Gironde region. The property had reportedly been rented through the rental broker application Airbnb by two Chinese nationals who arrived in France in January. They are believed to have entered the country using work visas as engineers for a wireless telecommunications firm.
After settling in Camblanes-et-Meynac, the men erected a large parabolic antenna system in the garden of the rented property. The move reportedly alarmed locals, who noticed that their own Internet service experienced disruptions following the erection of the parabolic antenna system by the Chinese nationals. A local family proceeded to alert local authorities about the antenna.
According to reports the DGSI arrested two Chinese nationals aged 27 and 29, while also seizing a substantial quantity of computer and satellite equipment that was found on the property. Two other men reportedly “of Chinese origin” but based in France, were also arrested over the weekend. They were charged with providing assistance to the two residents of the Airbnb property by illegally importing the satellite equipment installed on the property. Their identities have not been released by the authorities.
The French prosecutor’s office stated that the suspects were engaged in efforts to “capture satellite data from the Starlink [mobile broadband] network”. They were also allegedly trying to intercept communications data from “vital entities” in the military realm and “retransmit them to their country of origin”, namely China, according to the statement. They are now in custody facing charges of “delivering information to a foreign power […] likely to damage the interests” of France—a standard phraseology used in the French legal code to describe foreign espionage.
France’s Gironde region has long been an epicenter of espionage by international actors due to its proximity to a growing number of facilities and restricted sites related to critical telecommunication, aerospace, and defense industries. Several small towns and villages in the area are in proximity to the industrial core of France’s defense, space and aeronautics operations.
► Author: Joseph Fitsanakis | Date: 11 February 2026 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with China, DGSI (France), espionage, France, News, SIGINT, Starlink, telecommunications