Leaked documents show Georgian intelligence service spied on Western diplomats
September 23, 2021 1 Comment

THE EUROPEAN UNION HAS summoned the chief Georgian envoy to Brussels, in response to allegations that European, American and other diplomats were spied on by the Georgian security services. The allegations have emerged from an extensive collection of documents, which were released to the media by an anonymous whistleblower earlier this month.
The documents appear to confirm long-held suspicions among many in the former Soviet Republic, that the Georgian State Security Service (SSS) has been spying on members of the clergy, as well as on opposition politicians, journalists and others. But the documents also allege that the SSS has been spying on diplomats from the European Union, the United States, Israel, and other countries, who are stationed in the Georgian capital Tbilisi. Among those who have allegedly been targeted is the European Union’s ambassador to Georgia, Carl Hartzell.
The European External Action Service, which is the European Union’s foreign-policy diplomatic and foreign office, described the revelations as “a very serious matter”, and added that they have “implications in the framework of the Vienna Convention [on] Diplomatic Relations”. On Wednesday, the European Union reportedly summoned Georgia’s ambassador to Brussels, Vakhtang Makharoblishvili, in order to issue a formal complaint. Ambassador Hartzell said that the “volume and nature” of the alleged espionage went “beyond the normal activities of security services” and “raised serious questions about the relationship” between Georgia and the West.
Meanwhile, Georgia’s Prime Minister, Irakli Gharibashvili, described revelations in the leaked documents as “fabrications and falsifications”, and blamed his government’s political opponents for leaking them to the press. He also defended the conduct of the SSS, saying that the agency “conducts [only] legitimate wiretaps within the limits established by [Georgian] law”.
► Author: Joseph Fitsanakis | Date: 23 September 2021 | Permalink
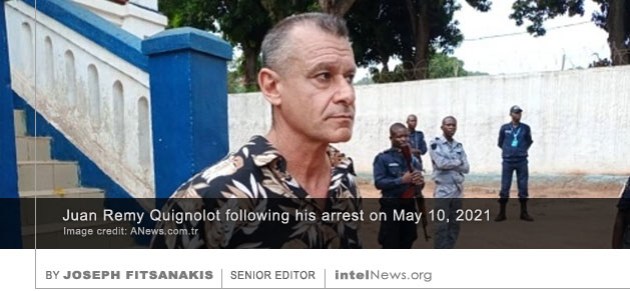
 An employee of the British embassy in Berlin, who was arrested last week on suspicion of spying for Russia, drew the attention of the authorities after he stopped using his bank account, according to reports. The man, who was
An employee of the British embassy in Berlin, who was arrested last week on suspicion of spying for Russia, drew the attention of the authorities after he stopped using his bank account, according to reports. The man, who was  An employee of the British embassy in Berlin has been arrested by German authorities, who charged him with spying for the intelligence services of the Russian Federation, according to reports. The German newsmagazine Focus
An employee of the British embassy in Berlin has been arrested by German authorities, who charged him with spying for the intelligence services of the Russian Federation, according to reports. The German newsmagazine Focus 












New Zealand judge refuses to disclose identities in rare espionage case
September 27, 2021 by Joseph Fitsanakis Leave a comment
A JUDGE IN NEW Zealand rejected on Monday a request by news media to lift the ban on the identity of a soldier, who was arrested nearly two years ago for allegedly spying for a foreign country. The soldier was arrested in December of 2019, and is being prosecuted under New Zealand’s 1961 Crimes Act. It is the first time in the post-Cold War era that this act has being used to prosecute someone in New Zealand.
The accused is facing a total of 17 charges, including six counts of espionage and attempted espionage, three counts of accessing a computer system for a dishonest purpose, and two counts of possessing an objectionable publication. The latter charge is believed to relate to the accused’s alleged connection with far-right and white nationalist organizations in New Zealand and possibly Australia. This claim has not been confirmed, however.
Since the arrest of the soldier, his name, as well as that of his wife and of multiple witnesses for the government, have been suppressed by the court. Importantly, the country for which the accused allegedly spied for has also been suppressed. This was done at the request of the government of New Zealand, which claims that doing otherwise could imperil “the defense and security of New Zealand”. The government also argues that naming the country for which the accused is believed to have spied could harm New Zealand’s diplomatic relations with that country.
On Monday, during a pre-trial court-martial hearing in Palmerston North, in which the suspect appeared via video-link, the chief judge in the case decided to extend the suppression of the information about the identity of those involved. The judge, Kevin Riordan, said that the name suppression would be extended at least until the next pre-trial hearing, which has not yet been scheduled. The trial was initially due to begin on October 6, but has been postponed indefinitely, due to complications arising from the use of classified evidence that the government’s lawyers intend to present during the court case.
► Author: Joseph Fitsanakis | Date: 27 September 2021 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with espionage, government secrecy, lawsuits, New Zealand, News