NSA director made secret visit to Israel last week
March 28, 2016 1 Comment
 The head of the United States’ largest intelligence agency secretly visited Israel last week, reportedly in order to explore forging closer ties between American and Israeli cyber intelligence experts. Israeli newspaper Ha’aretz said on Sunday that Admiral Michael Rogers, who directs the United States National Security Agency (NSA), was secretly in Israel last week. The NSA is America’s signals intelligence (SIGINT) agency, which is responsible for electronic collection, as well as protecting US government information and communication systems from foreign penetration and sabotage.
The head of the United States’ largest intelligence agency secretly visited Israel last week, reportedly in order to explore forging closer ties between American and Israeli cyber intelligence experts. Israeli newspaper Ha’aretz said on Sunday that Admiral Michael Rogers, who directs the United States National Security Agency (NSA), was secretly in Israel last week. The NSA is America’s signals intelligence (SIGINT) agency, which is responsible for electronic collection, as well as protecting US government information and communication systems from foreign penetration and sabotage.
According to Ha’aretz, Rogers was hosted in Israel by the leadership of the Israel Defense Forces’ SIGINT unit, which is known as Intelligence Corps Unit 8200. The secretive group, which is seen as Israel’s equivalent to the NSA, is tasked with collecting SIGINT from Middle Eastern locations and protecting Israel’s electronic information infrastructure from adversaries. According to the Israeli newspaper, Rogers’ visit was aimed at exploring ways in which the NSA and Unit 8200 can enhance their cooperation, especially against regional Middle Eastern powers like Iran or non-state groups like Hezbollah.
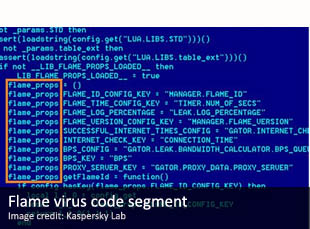
IntelNews readers will recall that the IDF’s Unit 8200 is viewed by some Middle East observers as the creator of the Stuxnet virus. Stuxnet is a sophisticated malware that is believed to have been designed as an electronic weapon against Iran’s nuclear program. Among these observers is New York Times correspondent David Sanger; in his 2012 book, Confront and Conceal, Sanger claimed that Stuxnet was designed by NSA and Unit 8200 programmers as part of a joint offensive cyber operation codenamed OLYMPIC GAMES. According to Sanger, the two agencies collaborated very closely between 2008 and 2011 in order to bring about Stuxnet and other carefully engineered malware, including Flame.
Ha’aretz said that Rogers’ visit was meant to solidify US and Israeli cooperation on offensive cyber operations, based on the legacy of Stuxnet and Flame. During his visit to Israel, the US intelligence official also met with the heads of other Israeli intelligence agencies, said Ha’aretz.
► Author: Joseph Fitsanakis | Date: 28 March 2016 | Permalink















Iranian engineer recruited by Holland helped CIA and Mossad deliver Stuxnet virus
September 4, 2019 by Joseph Fitsanakis 2 Comments
Most observers agree that Stuxnet was a joint cyber sabotage program that was devised and executed by the United States and Israel, with crucial assistance from Germany and France. But now a new report from Yahoo News claims that the contribution of Dutch intelligence was central in the Stuxnet operation. Citing “four intelligence sources”, Yahoo News’ Kim Zetter and Huib Modderkolk said on Monday that Holland’s General Intelligence and Security Service (AIVD) was brought into the Stuxnet operation in 2004. In November of that year, a secret meeting took place in The Hague that involved representatives from the AIVD, the United States Central Intelligence Agency, and Israel’s Mossad.
It was known that the Islamic Republic’s nuclear weapons program was crucially assisted by A.Q. Khan, a Pakistani nuclear physicist and engineer. In 1996, Khan sold the Iranians designs and hardware for uranium enrichment, which were based on blueprints he had access to while working for a Dutch company in the 1970s. By 2004, when the Dutch were consulted by the CIA and the Mossad, the AIVD had already infiltrated Khan’s supply network in Europe and elsewhere, according to Yahoo News. It also had recruited an Iranian engineer who was able to apply for work in the Iranian nuclear program as a contractor. This individual was provided with proprietary cover, said Yahoo News, which included two “dummy compan[ies] with employees, customers and records showing a history of activity”. The goal of the AIVD, CIA and Mossad was to have at least one of these companies be hired to provide services at the Natanz nuclear facility.
That is precisely what happened, according to Yahoo News. By the summer of 2007, the AIVD mole was working as a mechanic inside Natanz. The information he provided to the AIVD helped the designers of Stuxnet configure the virus in accordance with the specifications of Natanz’s industrial computers and networks. Later that year, the AIVD mole was able to install the virus on Natanz’s air-gapped computer network using a USB flash drive. It is not clear whether he was able to install the virus himself or whether he was able to infect the personal computer of a fellow engineer, who then unwittingly infected the nuclear facility’s system. The Yahoo News article quotes an intelligence source as saying that “the Dutch mole was the most important way of getting the virus into Natanz”.
It is believed that, upon discovering Stuxnet, the Iranian government arrested and probably executed a number of personnel working at Natanz. The Yahoo News article confirms that there was “loss of life over the Stuxnet program”, but does not specify whether the AIVD mole was among those who were executed. The website said it contacted the CIA and the Mossad to inquire about the role of the AIVD in the Stuxnet operation, but received no response. The AIVD declined to discuss its alleged involvement in the operation.
► Author: Joseph Fitsanakis | Date: 04 September 2019 | Permalink
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with AIVD (Netherlands), computer hacking, Iran, Iranian nuclear program, Netherlands, News, Stuxnet