News you may have missed #818 (USA edition)
December 19, 2012 3 Comments
 By IAN ALLEN | intelNews.org |
By IAN ALLEN | intelNews.org |
►►The real-life female CIA officer who helped track bin Laden. The Washington Post has a good article on the real-life career of a female CIA officer who helped the Agency track al-Qaeda founder Osama bin Laden. It is disappointing, however that the article, authored by Greg Miller and Toby Warrick, is headlined “In Zero Dark Thirty she’s the hero; in real life, CIA agent’s career is more complicated”. The CIA employee in question is not an “agent”; she is an officer. In the CIA, agents are assets, people recruited and handled by CIA officers. Amazing that The Post, with its experienced journalists and editors would confuse such a basic operational distinction.
►►US spy agencies to detail cyber-attacks from abroad. The US intelligence community is nearing completion of its first detailed review of cyber-spying against American targets from abroad, including an attempt to calculate US financial losses from hacker attacks based in China. The National Intelligence Estimate, the first involving cyber-espionage, will also seek to determine how large a role the Chinese government plays in directing or coordinating digital attacks aimed at stealing US intellectual property, according to officials who spoke on the condition of anonymity to discuss a classified undertaking.
►►CIA begins LGBT recruiting. As part of the CIA’s efforts to diversify its workforce, the spy agency is reaching out to a group that once was unable to get security clearance: lesbians and gay men. CIA officials have held a networking event for the Miami gay community sponsored by the Miami-Dade Gay and Lesbian Chamber of Commerce and the CIA. “This is the first time we’ve done a networking event of this type with any of the gay and lesbian chamber of commerces in the United States,” says Michael Barber, a self-identified “straight ally” and the spy agency’s LGBT Community Outreach and Liaison program manager.

















Sophisticated cyberespionage operation focused on high-profile targets
January 17, 2013 by Joseph Fitsanakis 3 Comments
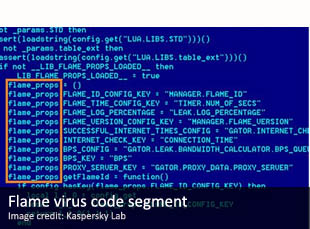
After Stuxnet and Flame, two computer programs believed to have made cyberespionage history, another super-sophisticated malware has been uncovered, this time targeting classified computer systems of diplomatic missions, energy and nuclear groups. The existence of the malware was publicly announced by Russian-based multi-national computer security firm Kaspersky Lab, which said its researchers had identified it as part of a cyberespionage operation called Rocra, short for Red October in Russian. The company’s report, published on Monday on Securelist, a computer security portal run by Kaspersky Lab, said that the malware has been active for at least six years. During that time, it spread slowly but steadily through infected emails sent to carefully targeted and vetted computer users. The purpose of the virus, which Kaspersky Lab said rivals Flame in complexity, is to extract “geopolitical data which can be used by nation states”. Most of the nearly 300 computers that have so far been found to have been infected belong to government installations, diplomatic missions, research organizations, trade groups, as well as nuclear, energy and aerospace agencies and companies. Interestingly, the majority of these targets appear to be located in Eastern Europe and former Soviet republics in Central Asia. On infected computers located in North America and Western Europe, the Rocra virus specifically targeted Acid Cryptofiler, an encryption program originally developed by the French military, which enjoys widespread use by European Union institutions, as well by executive organs belonging to the North Atlantic Treaty Organization. Read more of this post
Filed under Expert news and commentary on intelligence, espionage, spies and spying Tagged with Acid Cryptofiler, Central Asia, computer hacking, cyberespionage, cybersecurity, Eastern Europe, Kaspersky Lab, News, Rocra, Russia